There’s a good chance you’ve mined crypto at least once in your life. And no, I’m not talking about those big mining rigs people set up with fans running in the background, making the entire room hot as an oven.
I’m telling you that you’ve been tricked! Bamboozled! Swindled! That’s right; I’m saying that if you’re someone who has been using the internet for at least a few years, you’ve probably mined crypto. Except, all the crypto you’ve mined was for someone else.
If you scoffed at that statement, this article is for you.
Once again, we at the Coin Bureau are taking you down one of crypto’s many dark alleys, exposing its secrets, and ensuring you’re equipped to survive. The crypto industry is notorious for its vast amounts of rug pulls, NFT Scams, phishing, and other malware attacks.
Today, we’re taking a look at the world of ‘Cryptojacking’, also known by the street name ‘drive-by mining’.
What Is Cryptojacking?
Well, to put it simply, the word ‘cryptojacking’ refers to the usage of someone else’s device to mine cryptocurrencies without their permission or knowledge. This allows the attacker to mine cryptocurrencies for profit without incurring costs for hardware or electricity. These costs are instead off-loaded onto the infected device’s owner.
 Steal my CPU one more time. I dare you! Image via Memegenerator
Steal my CPU one more time. I dare you! Image via Memegenerator You know the guy at the office that steals your lunch and pretends not to know that it was yours? Yes, THAT guy. That’s the office-lunch version of a cryptojacker.
Devices of cryptojacking victims often heat up and slow down because of the CPU usage by the cryptojacker. But, of course, if it were as apparent as that, then most cryptojacking attacks would be detected and removed pretty easily.
So, most cryptojacking software these days are designed to stay hidden from the user. For example, there is cryptojacking software that is programmed to activate when the mobile or tablet device is locked and docked for charging. Since the battery is charging, users would not be able to notice the rapid power drain from the device and would attribute the heating to the charging process.
But that doesn’t mean that they are completely undetectable. A vigilant user might notice the subtle difference in the time it takes to charge the device and the consistent heating issues with the device. Most devices that fall victim to cryptojacking software have a short device life. The persistent use of the CPU leads to hardware failure in the long term.
In 2020, Cisco’s cloud security division reported that cryptojacking malware affected 69% of its clients. So, when I say that there’s a high chance you’ve mined crypto for someone else, I mean it.
How Cryptojacking Works
It is a process by which a remote attacker successfully installs a script on a computer, smartphone, or cloud server infrastructure, thus enabling it to use that device’s processing resources to mine cryptocurrency.
There are primarily two ways this can happen: either the infected user has downloaded a file with the hidden malware that auto-installs once downloaded, or the user is visiting a website with an embedded JavaScript that runs the mining program.
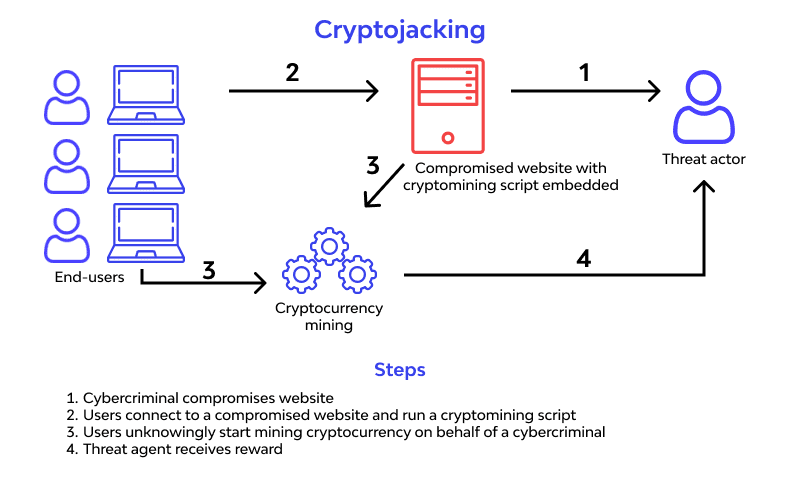 Cryptojacking Process via Wallarm
Cryptojacking Process via Wallarm The first method is commonly deployed through sending phishing emails that prompt you to download an attachment or file. For example, you might receive an email from a furniture company claiming to contain a pdf of their product catalogue or downloading a free game application that claims to have no ads but is cryptojacking your device. The installed malware can also sometimes self-propagate and spread to other devices connected to your network. This leads to high costs in removing and scrubbing the malware off all the devices in the network.
The second method is commonly referred to as ‘drive-by mining’. This name represents the nature in which the attack is carried out. Since the code is embedded in the website that the user is visiting, the cryptojacking usually terminates once the tab or browser is closed and remains active as long as the user accesses the website. These scripts are also sometimes embedded in advertisements displayed across various websites.

The most common crypto mined during cryptojacking attacks is Monero (XMR). Since XMR is a privacy coin, it is perfect for malicious actors using cryptojacking software, as it becomes easier to mask their trail and evade punishment. Moreover, Monero’s special hashing function allows it to be mined by CPU, which means it can mine XMR with ordinary devices, unlike Bitcoin.
History & Evolution Of Cryptojacking
Coinhive: Web-based Cryptojacking (2017-2019)
The concept behind cryptojacking has its origins as a legitimate monetization idea for businesses. It began in September 2017 when a website called Coinhive published code that would allow businesses that incorporated it into their website to leverage their customer’s device computing power to mine Monero. This business model would allow websites to remain ad-free.
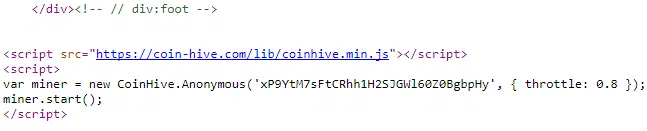 Coinhive Mining Code
Coinhive Mining Code Pirate Bay, a peer-to-peer file-sharing website, put this code into its website and invited users to utilise it to generate revenue for Pirate Bay instead of seeing on-site advertisements. Unfortunately, once this particular business model became popular, fraudulent copycat websites appeared, offering similar scripts that allowed miners to illegally steal the computational power of mobile devices, laptops, and servers.
The problem began when websites no longer asked permission from their users to borrow computational energy from devices. Since most of these websites directly copied the Coinhive code to run their shadow operations, multiple security firms identified cryptocurrency mining service Coinhive as the top malicious threat to Web users.
According to publicwww.com, a service that indexes the source code of Web sites, nearly 32,000 Web sites were running Coinhive’s JavaScript miner code in 2018. The public backlash due to the misuse of the Coinhive code coupled with the crypto bear market prompted the Coinhive website to shut down its services in March 2019.
If you’re someone who likes reading about the story and team behind the project, I would recommend reading KrebsonSecurity’s exposé article on Coinhive. I’d reckon you’d get more than your required fill of drama for the day.
MikroTik Routers: Router-based Cryptojacking (2018)
In 2018, nearly 200,000 MikroTik Routers were compromised after a serious security flaw in Winbox, a remote management service bundled in MikroTik routers’ operating system, RouterOS, was exploited. This allowed cryptojackers to install cryptojacking malware that infected every device connected to the router.
 Image via Medium
Image via Medium The attack began primarily with MikroTik routers in Brazil but quickly spread to other countries. The infection exploited a vulnerability (CVE-2018-14847) in the targeted devices' Winbox component, leading to unauthenticated, remote admin access to any vulnerable MikroTik router.
The configurations of the infected routers were then altered to inject a copy of the Coinhive malware's in-browser crypto-mining script into select parts of the victims' web traffic. The attacker initially injected the Coinhive script into all pages served by the router; later, he grew more cautious, injecting the Coinhive script solely into error pages returned by the routers.
This method of attack allowed the attacker to receive greater mining power as infecting the source produced a greater mining reach than the mining reach a small infected site would produce.
Glupteba: Botnet-based Cryptojacking (2020- present)
Glupteba is a cryptojacking "botnet" that silently installs crypto miners on Windows PCs to steal login credentials and authentication cookies. A "botnet" refers to a network of computers infected with malware that the attacker can use to hijack the computers.
The Glupteba botnet propagated through Google ads promising software cracks and phishing emails referring to malicious Google Docs files. Glupteba has been found infecting machines worldwide, with an estimated one million devices affected since 2020. A complaint filed by Google in late 2021 named multiple Russian nationals and entities alleged to be responsible for operating the Glupteba botnet.
Before I begin breaking down how Glupteba and botnets work, please note that much of my understanding of Glupteba has been derived from reading the recent Chainalysis Report on Crypto Crime in 2022. As a result, I've borrowed liberally from their report in explaining the mechanism behind Glupteba.
If you have the time, I would recommend that you read the entire report, or you can also watch Guy's video summary of the same.
Now let's begin.
How do Botnets work?
Cybercriminals control botnets using command-and-control (C2) servers. These servers allow the attacker to send commands to malware-infected PCs via the internet. Botnets hunt for domain addresses owned by their C2 servers to receive instructions, with instructions on where to look hardcoded into the malware.
One of the most common strategies used by law enforcement and cybersecurity experts to tackle botnets is to take certain sites offline, preventing botnets from receiving instructions from the C2 server. As a result, botnet operators generally create many backup domains in the event that the primary domain is taken down.
How does Glupteba's botnet work?
Most malware generates new domain addresses for botnets to scan until one of those backups is discovered, allowing them to receive further instructions from the C2 server. Glupteba, on the other hand, does something different. Glupteba is programmed to examine the Bitcoin blockchain for transactions carried out by three addresses controlled by its operators if its C2 server is down.
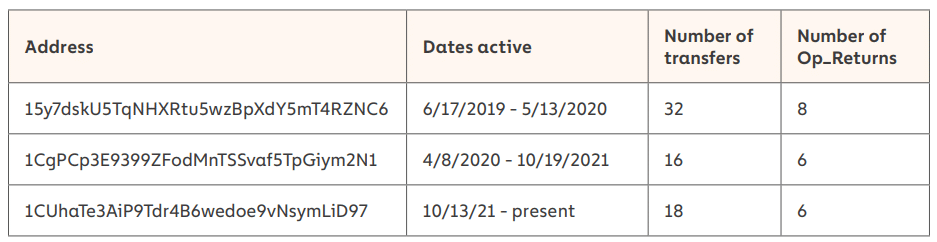 Three Operator Wallet Addresses via Chainalysis
Three Operator Wallet Addresses via Chainalysis These addresses carry out low-value transactions with encrypted data sent into the transaction's Op_Return field, which flags transactions as invalid. The Glupteba malware can then decode the data supplied into the Op_Return field to acquire the domain address of a new C2 server.
To put it another way, if one of Glupteba's C2 servers is shut down, the company may simply scan the blockchain for the new C2 server domain address, which is concealed amid hundreds of thousands of daily transactions.
Is Glupteba still a threat?
By collecting and examining an IP address used by one of Glupteba's C2 servers, Google was able to identify the persons mentioned in the complaint. The involvement of the identified individuals was further confirmed when their names were found as the registered owners or administrators of shell firms linked to Glupteba-related offences, including one that sold false digital advertising impressions such as the one used to infect devices with the botnet.
On the technological front, the present C2 server was successfully taken down by Google. However, since Glupteba has shown to be impregnable against such attacks thanks to its blockchain failsafe, a new C2 will be assigned soon. On the other hand, some security analysts fear that Glupteba might eventually pivot to becoming a ransomware or distributed denial of service (DDoS) botnet once it grows big enough.
How To Know If Your Device Has Been Cryptojacked
Most cryptojacking programs are hard to detect these days as they are programmed to activate when the device is idle. However, this does not make detection impossible. Let us look at some of the factors to consider.
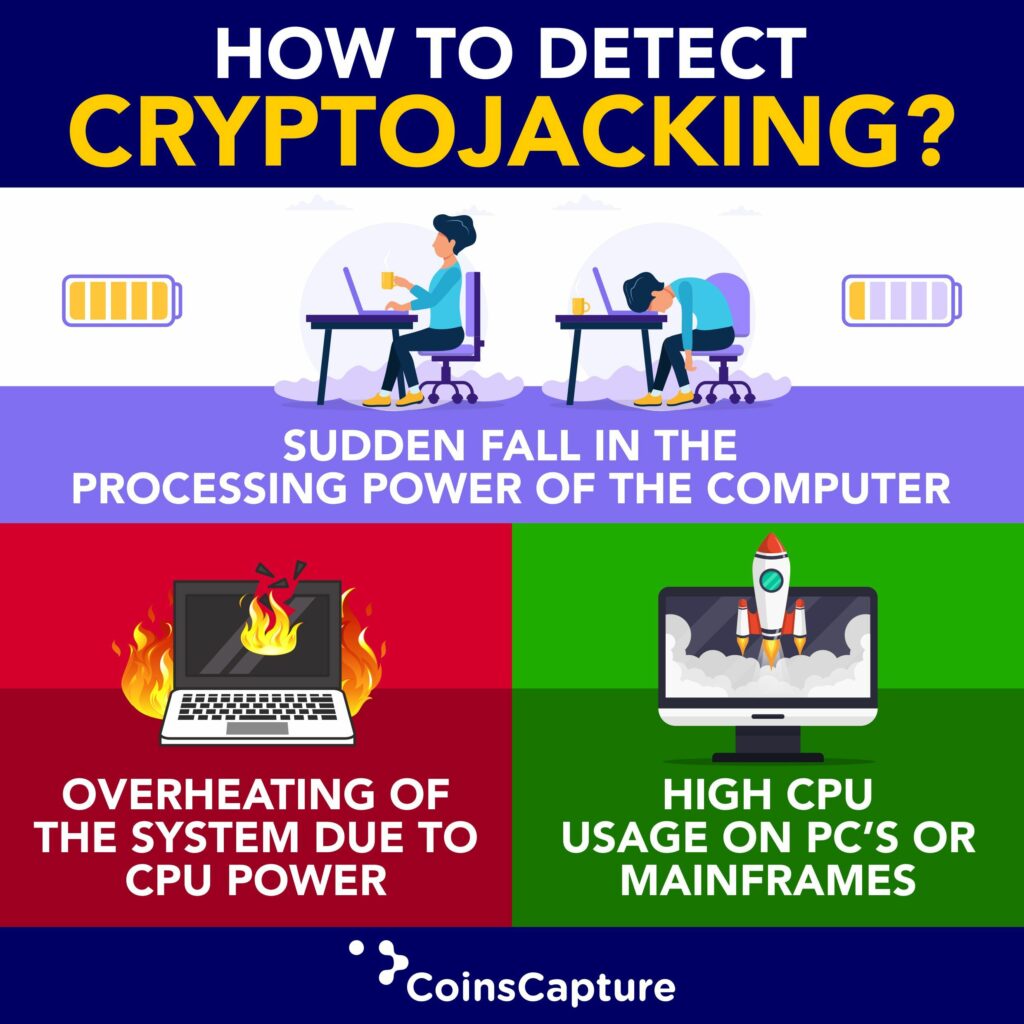 How to detect cryptojacking. Image via Pinterest
How to detect cryptojacking. Image via Pinterest Decreased Performance & Battery Life
One of those most tell-tale signs of being cryptojacked is if you suddenly notice a sharp decrease in your device performance. This could be in frequent crashes, slow processing speed and decreased battery life.
However, if your device is being cryptojacked during the idle state or charging state, it would help to analyse the speed at which your device is getting charged. If you notice that it is taking longer than usual, your device might be running the cryptojacking program in the background, which is draining power from the device.
Heating Issues
If your device overheats almost all the time, it could signify that it is being cryptojacked. Cryptojacking is a resource-intensive operation that can cause computers to overheat. This can damage computers or reduce their lifespan. In addition, fans that run longer than they should to cool down the system are also related to overheated equipment.
High CPU Usage
Keep an eye on your device’s CPU usage during activity and idle states. The Activity Monitor or Task Manager can keep track of how much CPU is being used. If you notice a sudden spike in CPU usage during idle states, it’s a sign that crypto mining scripts may be running.
Run a malware or website scanner
If you suspect that your device might be infected with cryptojacking malware, it’s better to confirm your suspicions by running a malware scanner like Avast or Malwarebytes. On the other hand, if you suspect that your website has been compromised and infected, you can manually inspect the HTML code or use programs like Malcure and Sucuri that can scan for malicious codes.
How to Avoid Getting Cryptojacked
As with any other form of internet security, it helps to have some clean browsing and internet habits. A few of these habits are:
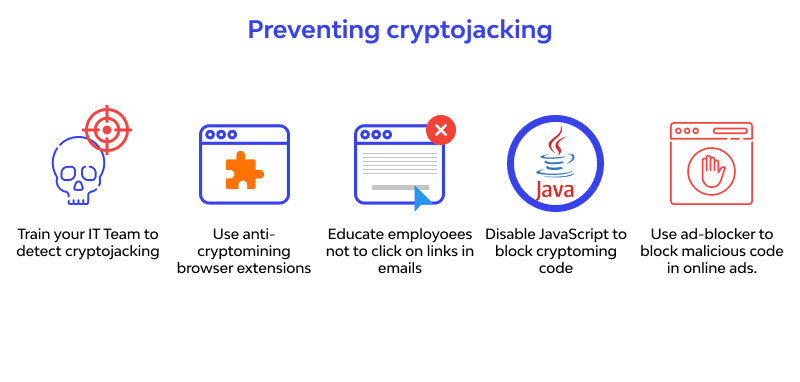 Cryptojacking Prevention via Wallarm
Cryptojacking Prevention via Wallarm Avoiding phishing emails and links
Never click on anything you find on the internet without double-checking the address and sources. Avoid responding to random discord DMs asking you to join groups or offering an opportunity for a rare NFT mint. Nothing good will ever come of it. Once you click the link, you might be directed to a webpage that could infect you with cryptojacking malware.
Use an Adblocker
Install an Adblocker extension to your browser or use a browser like Brave to avoid getting infected through JavaScript code embedded in malicious advertisements.
Disable JavaScript
Deactivating JavaScript can protect your device against cryptojacking malware when visiting the web. However, keep in mind that deactivating JavaScript will prevent you from using many of the features you require while browsing.
Antivirus and Malware Scanners
Purchase online security protection from your Internet or Communications Service Provider. Install and keep your antivirus and anti-malware protection systems updated regularly.

How To Remove Cryptojacking Malware
If you’ve been infected with cryptojacking malware, follow the steps below to remove it from your device.
Run Microsoft Defender Scan
The first step to removing the malware is to identify it. Download and launch the Microsoft Defender Scan App. Run a full scan to detect the malware. Remove any threats if detected.
Once the full scan is completed, run an offline scan to catch trojans that pretend to be system files. Remove any threats if detected.
Boot in Safe Mode
The next step in the process is to run a safe boot of your system. To do so, press the Windows and R buttons. Type ‘msconfig’ in the text box and click enter.
Now a pop-up must have appeared. Select the safe boot option under the boot tab and restart your PC. The safe boot mode will allow you to remove any suspicious programs without them causing any interference in the background.
Remove Suspicious Programs and Temporary Files
Enter the Control Panel of your device and start uninstalling unwanted or unnecessary programs. This will clear up memory space while also ensuring that you are not exposing yourself to unwanted risks.
To remove temporary files, search for disk cleanup or type “%temp%” on the search bar. It should display the list of all temp and cache files. Select all and delete.
Reset Browser Settings
Click on the settings menu within your browser and click reset.
Boot in Normal Mode
Remember the safe boot we performed? It’s time to disable that. Press Windows and R buttons together again. Now type ‘msconfig’ and disable the safe boot option and restart the system.
Scan With Anti-Malware Scanners
Now that we’ve cleaned the system, run a scan again to see if all suspicious files have been removed. It helps to have a reliable scanner.
If you’re a visual person, refer to this video on the subject by MalwareFox.
Closing Thoughts
Now that you’re aware of what ‘cryptojacking’ is remember to keep informed on all the latest developments and news on the subject. Attackers are constantly innovating different methods of infecting users to make a profit. The more we know, the better we are at avoiding these pitfalls.





