Coinbase Wallet (called the Base app) is a self-custody app where your private keys live on your device and you approve every transaction. It is built for everyday on-chain use like swaps, NFTs, and DApps. That also means it’s a hot wallet, so “safe” here is about sensible risk management, not bank-style guarantees.
Crucially, Coinbase Wallet ≠ Coinbase Exchange: there’s no custodial insurance or platform recovery if you lose your keys. In this guide, we’ll deep-dive into features, real risks and incidents, comparisons with alternatives, step-by-step hardening and recovery, and exactly when to pair it with cold storage.
Quick Verdict
Coinbase Wallet is safe for everyday on-chain use when you set it up correctly, but it is a hot wallet and the risk sits with you. There is no insurance or chargebacks, and mistakes or phishing are unrecoverable. Use it as a daily driver for swaps, NFTs, and DApps. For large or long-term holdings, use a hardware wallet and keep only a spending balance hot.
Who it’s for
- Everyday DeFi and NFT users who want quick swaps, clear approvals, and broad DApp compatibility.
- Mobile-first users who value smooth UX and optional cloud backup.
- Builders and testers who rotate addresses and interact with many DApps.
Who should look elsewhere
- Long-term holders or large balances, pair with a hardware wallet such as Ledger or Trezor.
- Teams needing multisig or advanced policies, consider specialized wallets or institutional custody.
Safety scores
Biggest risks → quick fixes
Phishing, fake support, wallet drainers → Verify URLs, limit approvals, revoke monthly.
SIM swap, account takeover → Use security keys or passkeys, avoid SMS for Apple or Google.
Device malware → Keep the OS updated, treat this as a spending wallet, not a vault.
Important clarifications
- Wallet vs Exchange: Custodial insurance or policies do not cover self-custody.
- Keys are generated and stored locally, the 12-word seed controls funds.
- Encrypted cloud backup is only as strong as your Apple or Google account security.
Expert advice
- Use Coinbase Wallet for active use, hardware for anything you cannot afford to lose.
- Keep two wallets, Spending and Vault.
- Set a monthly reminder to review and revoke token approvals.
Coinbase Wallet at a Glance
Coinbase Wallet (now the Base app, formerly Coinbase Wallet) is a self-custody wallet: you hold the keys and approve every move. It’s separate from the Coinbase exchange account you might use to buy crypto. Here, you’re in charge of connections, permissions, and backups.
 Coinbase Wallet lets you Hold Crypto, Explore DeFi, and Manage NFTs while Connecting to Onchain Apps. Image via Coinbase
Coinbase Wallet lets you Hold Crypto, Explore DeFi, and Manage NFTs while Connecting to Onchain Apps. Image via CoinbaseThe appeal is straightforward: a single place to hold crypto, explore DeFi, and manage NFTs while connecting to onchain apps. If you’re curious about how those apps work, Coinbase’s primer on DApps explains the basics in plain language.
Who is it for? Anyone who wants a convenient “daily driver” for Web3, trying new protocols, making small swaps, collecting or listing NFTs, and moving funds between apps with minimal friction. If you’re storing large, long-term balances, pair this with an offline hardware wallet and keep only a spending amount hot; that split keeps things fast without treating your phone like a safe deposit box.
How Coinbase Wallet Protects You
Coinbase Wallet is a self-custody app that keeps your keys on your device, not on an exchange (see the difference between Coinbase and Coinbase Wallet). As a hot wallet, it’s designed for everyday on-chain activity.
 Coinbase Wallet Follows a Self-Custody Model. Image via Coinbase
Coinbase Wallet Follows a Self-Custody Model. Image via CoinbaseLocal Keys & Recovery
Coinbase Wallet follows a self-custody model: your private keys are generated and stored locally on your device (see Coinbase’s wallet security). Access is controlled by a 12-word recovery phrase, which acts as the master key to your funds. Store it offline and never share it. If you lose access to the app or your phone, you can recover your wallet by restoring with that phrase.
Optional seed-phrase alternatives. Coinbase’s smart wallet supports passkeys (FIDO/WebAuthn) with a recovery-key flow, letting you access a wallet without handling a traditional seed phrase. It is useful if you prefer device-bound security with fewer secrets to manage.
App-Level Protections
You can enable PIN/biometric locks and an optional encrypted cloud backup to iCloud or Google Drive. Backups are encrypted on-device using AES-256-GCM and are decrypted only with your backup password inside the app. Treat cloud backup as convenience (not a replacement for an offline copy), and secure your Apple/Google account with strong authentication.
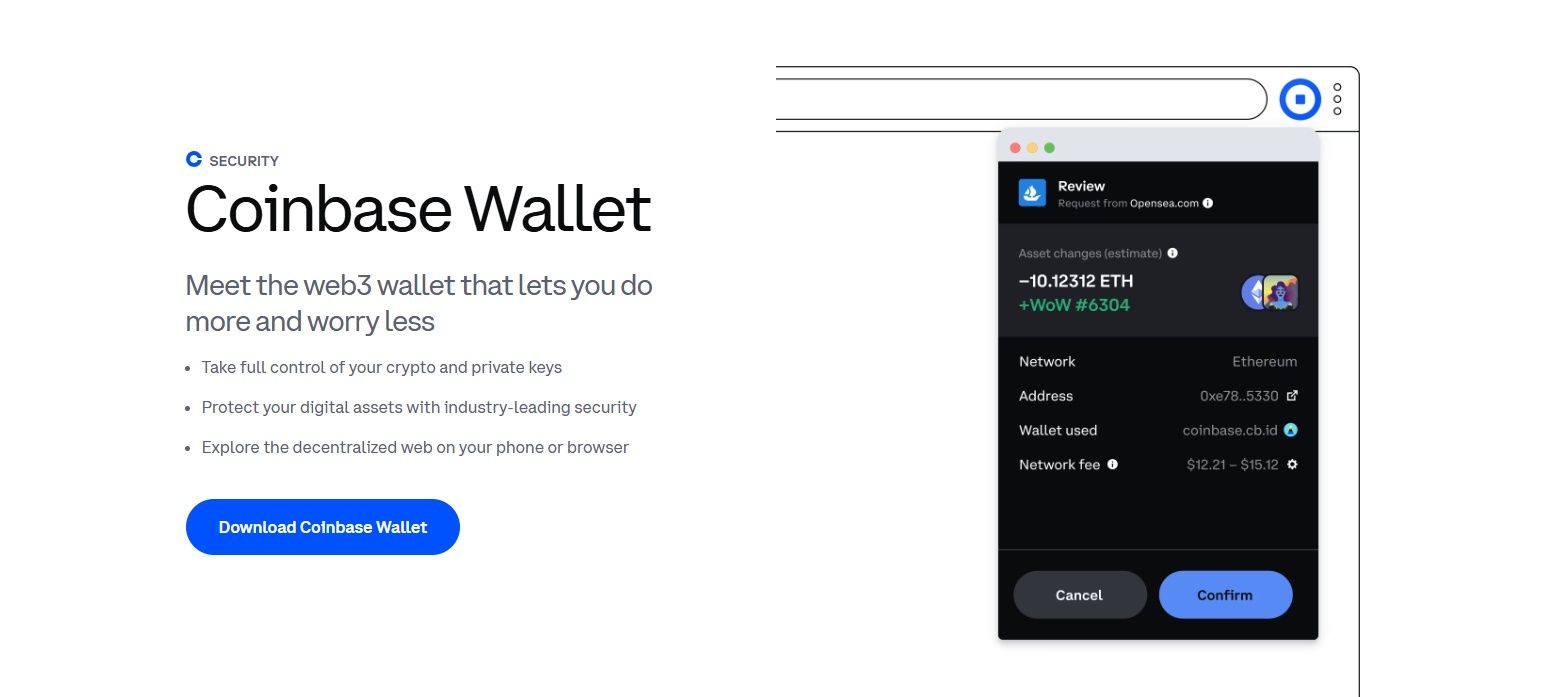
Safer DApp Interactions
Before you sign, Wallet shows permission previews, transaction previews, and explicit token approvals, making requested access clear. The app also applies a DApp blocklist (as noted under wallet security, see above) and defaults to spam-token filtering to hide obvious scam airdrops. From settings, you can review or revoke allowances and hide unwanted assets to reduce clutter and risk.
Hardware Support
For higher-value holdings, pair the Coinbase Wallet browser extension with a Ledger hardware wallet. Your keys remain offline on the Ledger while the extension serves as the interface, akin to tapping a payment card while the chip guards the secret. If you need setup guidance, follow Ledger’s connection guide for Coinbase Wallet.
Quick Feature Checklist
| Feature | What it does | What it mitigates |
|---|---|---|
| Local key generation & 12-word recovery phrase | Keys created/stored on your device; recover with seed | Server-side breaches; account lockouts |
| Smart-wallet passkeys (optional) | Sign with passkey; recovery-key option | Seed-handling errors; seed-phrase phishing |
| PIN/biometric app lock | Device-level gate to open/sign | Casual device access; shoulder-surfing |
| Encrypted cloud backup | AES-256-GCM backup to iCloud/Drive | Loss/theft of device; forgotten seed |
| Permission & transaction previews | Show requested access and balance deltas | Blind approvals; “drainer” contracts |
| Token-approval alerts & easy revokes | Review/revoke allowances in-app | Long-lived approvals exploited later |
| DApp blocklist & spam-token filter | Flags malicious sites; hides scam airdrops | Phishing redirects; airdrop bait |
| Multiple addresses (“spending” vs “vault”) | Separate public identities | Cross-contamination of approvals; privacy leaks |
| Ledger hardware support | Keep keys offline; sign via hardware | Malware on device; high-impact key theft |
Real-World Risks
Even with solid safeguards, a hot wallet carries real-world risks that hinge on user behavior and device hygiene. The biggest pitfalls are social engineering (see Coinbase’s guidance on support scams), device compromise, and the irreversibility of crypto transfers (U.S. regulators note they’re typically not reversible), which is why careful setup and ongoing vigilance matter.
 Crypto Transfers are Generally Not Reversible the Way Card Payments can be. Image via Freepik
Crypto Transfers are Generally Not Reversible the Way Card Payments can be. Image via FreepikSocial Engineering & SIM-Swap
The most common threats are phishing and fake support. Impersonators who pressure you to “verify” details or move funds to a “safe” wallet. A related risk is a SIM-swap, where attackers hijack your phone number and intercept codes. Reduce exposure by using passkeys (phishing-resistant) or security keys for login, and by hardening your email/cloud accounts with strong authentication. Remember: Coinbase will not call you out of the blue or ask for your seed phrase.
Device-Level Malware
Hot wallets live on connected devices, so malware can try to capture screens, keystrokes, or approvals. Keep OS and apps updated, avoid untrusted networks on mobile, and treat a hot wallet as a spending tool, not a vault. For high-value holdings, prefer cold storage (offline keys) and sign via hardware. On work phones, ask IT about MDM policies that might monitor or restrict crypto apps.
Check out our primer on hot wallets vs cold wallets, which explains the trade-offs clearly.
No Insurance/Chargebacks in Self-Custody
A crucial distinction: Coinbase Exchange may have custodial protections for fiat balances (see How is Coinbase insured?), but Coinbase Wallet is self-custody. You hold the keys and bear losses if compromised. Also, crypto transfers are not reversible the way card payments can be.
Coinbase Wallet Security Track Record
A company’s past tells you how it handles the next crisis. To set context, we’ll first look at Coinbase’s incident reports on its own security blog, then the independent controls it discloses through SOC reporting and its public bug bounty program, and translate what each means for day-to-day safety in self-custody.
 A Company’s pPast Tells you How it Handles the Next Crisis. Image via Freepik
A Company’s pPast Tells you How it Handles the Next Crisis. Image via Freepik Security Timeline: Key Events & Responses
2021 - SMS 2FA account-recovery flaw
Attackers exploited a weakness in Coinbase’s SMS account recovery flow and drained funds from at least 6,000 exchange accounts; Coinbase patched the flaw and notified affected users.
- Lesson: SMS is fragile → prefer passkeys for sign-in and recovery where supported (introducing passkeys).
February 2023 - Employee SMS-phishing
An employee fell for an SMS phishing page; controls limited access and the incident was contained (Coinbase’s case study; corroborated in industry press). Thankfully, no customer funds were lost.
- Lesson: Invest in staff training, device hardening, and phishing-resistant auth; wallet users should stay alert to “support” DMs.
Late 2024–May 2025 - Support-agent bribery & data exposure
Criminals bribed support agents at an external vendor, exposing personal data for a subset of users; Coinbase reported the breach, terminated involved staff, and warned customers.
- Lesson: Even with strong systems, human compromise is possible → never share seed phrases and verify contacts via official channels.
Standards, Audits & Controls (High-Level)
Coinbase maintains third-party SOC reports for specific lines of business and runs public bug bounties, as we mentioned before. An on-chain bounty of up to $5 million was announced in July 2025.
Limits: These audits cover organizational controls (e.g., service availability, change management) for covered services; they do not insure losses in self-custody wallets. Your keys remain your responsibility.
Tip: What changed after past incidents (practical wins today):
- SMS → passkeys: Broader passkey support across Coinbase sign-in reduces phishing risk.
- Employee-targeted phishing → tighter controls: Reinforced training, detections, and vendor oversight.
- On-chain risk → proactive research: Expanded bug bounty scope for smart contracts and on-chain components.
User Experience & Community Trust
Store ratings and community reviews aren’t perfect, but they’re useful “temperature checks.” Below is a snapshot of what users report today, plus common themes to watch for as you weigh Coinbase Wallet against your needs.
 Users Frequently Warn about Phishing and Malicious DApp Approvals, Prompting User Vigilance. Image via Freepik
Users Frequently Warn about Phishing and Malicious DApp Approvals, Prompting User Vigilance. Image via FreepikApp Store Ratings Snapshot
On iOS, the listing shows 4.6/5 across ~160k+ ratings (App Store). On Android, the wallet sits around 3.8/5 with ~128k reviews (Google Play).
Commonly praised for:
- Approachable UX for beginners
- Straightforward onramping to on-chain activity
- Wide DApp/asset coverage (see aggregated notes on G2).
Common Complaints:
- Slow/limited support
- Confusing fees or gas settings
- Occasional send/swap errors
Third-Party/Community Signals
Review hubs generally highlight ease of use and broad network support while noting mixed customer support experiences, as per the G2 notes. Over on TrustPilot, Coinbase enjoys a 4-star rating. In community spaces, users frequently warn about phishing and malicious DApp approvals. Recurring cautionary threads pop up on Reddit: r/CryptoCurrency and r/CoinBase.
Mobile apps score well overall, but the extension draws tougher feedback; regardless of platform, user vigilance around approvals and links remains a consistent theme.
Practical Scam Playbook (What Attacks Look Like Today)
Most crypto losses stem from social engineering and bad approvals, not code breaking. Below are the patterns we see most often today, and the simple habits that block them.
 Don’t Sign Transactions you don’t Understand and Document any Evidence. Image via Freepik
Don’t Sign Transactions you don’t Understand and Document any Evidence. Image via FreepikReal Scam Tactics to Watch For
- Fake “Coinbase Support” outreach and urgent account-lock messages that drive you to a look-alike site. Classic phishing.
- SIM-swap takeovers: Criminals reassign your phone number to intercept codes and reset logins; see the FCC’s guidance on cell-phone fraud.
- Refund/airdrop bait and malicious links that trigger wallet drainers or trick you into dangerous signatures (overview from Chainalysis).
- Romance/investment “pig-butchering”: Long-con relationships that funnel victims into fake platforms. Here’s a detailed description by the FBI.
How to Self-Defend
- Verify the messenger: Support won’t DM you first; type URLs yourself; look for misspellings and odd domains.
- Harden sign-in: Remove SMS where possible; use app-based codes or passkey-style logins; add a carrier PIN to reduce SIM-swap/port-out risk.
- Treat approvals like standing orders: Review token approvals and periodically revoke unused permissions (how-to guide).
- Use a two-wallet routine: A small spending wallet for daily DApps and a separate vault with no DApp activity, signed via hardware.
- When in doubt, stop: Don’t sign transactions you don’t understand; if you’re targeted, document evidence and report to IC3.
Coinbase Wallet vs Alternatives (When to Choose What)
Choosing the right wallet comes down to who holds the keys, whether you want any custodial protections, and how much on-chain access you need. The comparisons below outline those trade-offs so you can match the tool to the job.
 Choosing the Right wallet Comes Down to Who Holds the Keys. Image via Freepik
Choosing the Right wallet Comes Down to Who Holds the Keys. Image via FreepikCoinbase Wallet vs Coinbase Exchange
- Custody: Coinbase Wallet is self-custody, where you control the keys. By contrast, the Coinbase Exchange is custodial and manages assets on your behalf under its platform controls.
- Insurance: Custodial accounts may have limited, platform-level protections; self-custody in Coinbase Wallet does not.
- UX: For converting to cash, the Exchange offers straightforward cash-out flows. Coinbase Wallet prioritizes onchain features (DeFi, NFTs, DApps), which involve gas fees and permissions you approve.
Coinbase Wallet vs Hardware Wallets (Ledger/Trezor)
- Hot vs Cold: Hardware devices keep private keys offline and only connect to sign, reducing remote-attack surface.
- Who should use hardware: Long-term holders, larger balances, or teams needing stricter operational controls. Many users keep a vault on hardware and a smaller spending balance in a hot wallet for everyday DApps.
Check out our comparison of the hardware wallet giants: Trezor vs Ledger.
Coinbase Wallet vs Other Software Wallets (MetaMask, Trust, Rabby, Zengo)
| Wallet | Key model | Recovery options | Hardware support | DApp safety prompts |
|---|---|---|---|---|
| MetaMask | Seed phrase | Manual seed backup | Broad integrations (incl. hardware) | Confirmations with simulation add-ons |
| Trust Wallet | Seed phrase | Manual seed backup | Limited direct integrations | Built-in security scanner highlights risks |
| Rabby | Seed phrase | Manual seed backup | Works with common hardware | Transaction simulation shows balance changes pre-sign |
| Zengo | MPC (no seed) | Account-based recovery | No traditional seed signing | Phishing-resistant, seed-less setup |
Who picks what:
- DeFi power-user: Rabby or MetaMask for broad DApp compatibility and granular previews.
- NFT trader / mobile-first: Trust Wallet or Coinbase Wallet for app-centric UX and asset coverage.
- Beginner avoiding seed handling: Zengo’s MPC removes seed-phrase storage.
- Long-term saver / large balances: Hardware wallet for the vault; Coinbase Wallet (or similar) for daily spending.
Safety & Privacy Considerations
Convenience features can expand your attack surface, and some data collection is unavoidable when you use connected apps. The goal is to configure once, then verify periodically, so safety and privacy keep pace with how you use Coinbase Wallet.
 Configure Once, then Verify Periodically so Safety and Privacy Protocols Remains Up to Date. Image via Shutterstock
Configure Once, then Verify Periodically so Safety and Privacy Protocols Remains Up to Date. Image via ShutterstockCloud Backup Trade-Offs
Encrypted cloud backups reduce the risk of losing access if your phone dies, but they shift part of the risk to your Apple/Google account security. If that account is taken over, an attacker could attempt restore flows.
Mitigate by enabling Apple’s Advanced Data Protection for end-to-end encryption, using Google’s security keys for sign-in, and following NIST SP 800-63B guidance to avoid SMS as a second factor. If you opt into Wallet’s backup features, review Coinbase’s Wallet Help for current steps and store at least one offline copy (paper/steel) in a separate location.
Data Permissions & Telemetry
Understand what data may be collected and how it’s used. Coinbase outlines data practices for its Wallet in the Base Account & Base App Privacy Policy and the broader Global Privacy Policy.
Where available, use in-app privacy toggles and platform settings to minimize analytics; developer docs note optional telemetry and opt-out controls in related Coinbase tooling (Base Account telemetry, OnchainKit telemetry). Periodically recheck permissions (camera, contacts, Bluetooth), and keep sensitive activity on a separate, hardened device when possible.
Regulatory & Incident Context
Regulation shapes how a company operates, while self-custody defines who controls your assets. We will give you a background that explains why Coinbase can be highly regulated as a business, yet still cannot guarantee outcomes for funds you hold in Coinbase Wallet.
 Regulation Shapes how a Company Operates, while Self-Custody Defines who Controls your Assets. Image via Freepik
Regulation Shapes how a Company Operates, while Self-Custody Defines who Controls your Assets. Image via FreepikCoinbase Corporate Compliance Footing (High-Level)
Coinbase operates under a patchwork of licenses and registrations that vary by region, including U.S. money-transmitter and other approvals listed on its Licenses page. That compliance posture typically correlates with investments in security teams, audits, and oversight, and may improve operational resilience.
However, these obligations don’t convert a self-custody wallet into an insured account, and they don’t transfer key control from you to Coinbase. If you use Coinbase Wallet, you hold the private keys and are responsible for safeguarding them. For clarity on what government insurance does, and does not, cover, see the FDIC’s consumer guidance on deposit insurance (crypto with private keys is outside its scope).
Exchange Incidents vs Wallet Risk Model
Exchange incidents (e.g., outages or account-access issues) are tracked on Coinbase’s status page and can affect logins, trading, or withdrawals on the custodial platform.
By contrast, Coinbase Wallet operates on a user-held-keys model: access to funds depends on your device and recovery phrase, not on exchange uptime. Practically, this means the blast radius of an exchange disruption differs from a wallet compromise. One is a service availability problem; the other is a key-control problem with on-chain consequences.
Setup & Hardening Checklist (Step-by-Step)
Set things up once with care, then review on a schedule (e.g., monthly). The steps below balance convenience with strong defaults across mobile and extension.
 Set Things up once with Care, then Review on a Schedule. Image via Freepik
Set Things up once with Care, then Review on a Schedule. Image via Freepik- Create your wallet → Install the Coinbase Wallet mobile app or browser extension and follow the in-app prompts to create or import.
- Enable a device lock → Turn on a strong iPhone passcode (Apple guide) or Android screen lock (Android help). Prefer long numeric or alphanumeric codes.
- Secure your recovery phrase offline → Write the 12 words on paper or use a steel backup (stored separately). Do not take screenshots.
- Optional: Encrypted cloud backup → If you enable Wallet’s cloud backup, treat your Apple/Google account as part of your security perimeter (use strong auth and alerts). Keep an offline copy regardless.
- Connect hardware for high-value funds → Move long-term holdings to a hardware wallet and sign from there; see Trezor’s guide for moving from Coinbase (concept applies to Ledger too).
- Run a two-wallet setup → Keep a small spending wallet for DApps and a separate vault with no DApp activity.
- Enable address allowlisting (where supported) → If you also use Coinbase’s custodial platforms, turn on allowlisting so withdrawals only go to pre-approved addresses.
- Review approvals monthly → Treat token allowances like standing orders. Use an approval checker and revoke anything you no longer need.
- Set phishing/approval alerts → Turn on platform security alerts (email/app). Be suspicious of urgent “support” messages.
- Turn on passkeys or security keys → Prefer passkeys for phishing-resistant sign-ins wherever supported.
Recovery & Continuity (When Things Go Sideways)
In self-custody, recovery is about proving you still control the key (via seed, passkey, or backup) and cutting off any lingering access that a thief or malicious DApp might retain.
 To Restore, Install Coinbase Wallet and Choose I Already have a Wallet. Image via Freepik
To Restore, Install Coinbase Wallet and Choose I Already have a Wallet. Image via FreepikLost/Compromised Device
Act fast: remote-erase a lost phone via Apple Find My Device or Android Find My Device, then move to a clean device. On Coinbase, use the account flow to regain web3-wallet access (identity check where applicable), and immediately transfer funds to a fresh wallet or hardware vault. Treat the old device as untrusted, even if recovered.
Restore from Seed / Export to Other Wallets
To restore, install Coinbase Wallet and choose I already have a wallet → Restore with recovery phrase (steps under create/import). If you ever need to migrate, most wallets let you import via seed or private key. For example, MetaMask’s guide to using an existing wallet. Always test with a small transaction first to confirm you’re in the right account before moving larger balances.
Cut Off Malicious DApps
Disconnect any lingering site connections directly from Wallet (Coinbase’s primer on revoking DApp connections). Then review on-chain allowances with a token-approval checker (e.g., Etherscan) and revoke anything you don’t recognize. If approvals look compromised, rotate addresses (generate a new wallet) and move assets; keep the new wallet “clean” until you’re confident all risky permissions are gone.
Expert Verdict: Is Coinbase Wallet “Safe” in 2026?
Coinbase Wallet is a robust hot wallet when set up and used correctly. It’s well-suited to daily on-chain activity, swaps, DApps, and NFTs, where convenience and speed matter.
Not a substitute for cold storage: For long-term holdings or large balances, a hardware wallet (kept offline) remains the more conservative choice. Many users sensibly pair a hardware vault with a smaller spending wallet for everyday use.
Safety is shared: The app’s protections only go so far without good operational hygiene. Strong device locks, secure backups (preferably offline), careful permissioning and regular approval reviews, and disciplined phishing defenses.
Combine these habits with periodic audits to keep risk in check.





