Trust Wallet has become one of the most widely used crypto wallets in the world today. It has grown to great lengths ever since it was acquired by Binance in 2018. With over 200 million downloads, it has 140+ million monthly users, while supporting over 100 blockchains.
Trust Wallet is, without a doubt, a large wallet, and users are often worried about its safety for everyday use. This guide will answer this very question without sugarcoating. In this guide, you will learn about Trust Wallet’s security architecture, risks attached to it, and missing protection, among others.
The guide will also provide unbiased comparisons between Trust Wallet and MetaMask, Coinbase Wallet, and Ledger, giving readers ample options to understand where Trust Wallet stands in today’s landscape. Whether Trust Wallet is secure or not, this guide will cover it all.
If you want to read our full review of Trust Wallet, take a look here.
Quick Verdict
Trust Wallet is a solid choice for managing crypto day to day. The tech is strong and, for most people, it is safe to use. Still, you need to know what you are signing up for.
If you lose your seed phrase, the funds are gone. There is no recovery process and no support team that can restore access.
The wallet has no two-factor authentication for sending funds. It does not support multisig. Your device lock, app lock, and seed phrase form the entire security model.
Trust Wallet works well for people who understand private keys and can follow simple safety habits. It is not ideal for beginners who struggle with passwords or are prone to phishing mistakes.
How Trust Wallet’s Security Model Works
Trust Wallet follows a straightforward and modern security model. Everything revolves around user control. There is no cloud backup that the company manages, no private key stored on remote servers, and no central account that can be recovered on request. The design is meant to give complete control to the user, and that design comes with strengths and weaknesses.
Non-Custodial Design — What It Really Means
Trust Wallet is non-custodial, although the term can be confusing. In layman's terms, you directly control your private keys because of the wallet. However, Trust Wallet never holds them, never stores a copy of your seed phrase, and cannot step in if something goes wrong. The wallet on your phone is the actual “account” as far as the blockchain is concerned.
This model has clear benefits. No one can freeze your assets or slow down a transfer. There’s no built-in KYC process just to create a wallet, and your activity isn’t tied to a central account the company manages. You can export your seed phrase and move your wallet to any BIP39-compatible app whenever you like. Many people choose Trust Wallet for that level of control.
The downside is you're truly on your own in non-custodial scenarios. Lose your seed phrase, and there’s no recovery system. Share it accidentally or type it into a fake website, and whoever gets it gains full control. Send funds to the wrong address, and there’s no “undo” button or support agent who can pull the transaction back.
Non-custodial freedom feels empowering when everything goes right, but it also means there is no fallback if you slip up.
 Trust Wallet Has Become One Of The Most Widely Used Crypto Wallets In The World Today. Image Via Shutterstock
Trust Wallet Has Become One Of The Most Widely Used Crypto Wallets In The World Today. Image Via ShutterstockLocal Key Generation and Storage
All the wallet info in Trust Wallet is made right on your phone. It uses the usual BIP39/BIP44 standards to give you a recovery phrase, and every address you use comes from that one phrase. Since your phone handles the entire process, your private keys stay on your device and aren’t sent to Trust Wallet’s servers.
Your private keys are always tucked away safe and sound, right here on your phone, fully scrambled and encrypted. We only ever peek at them when you need to approve a transaction. For ultimate protection, they're hidden behind your phone's own security checks (like your fingerprint) and backed up by that super-important 12-word recovery phrase. The key point is that we never upload your keys to Trust Wallet's cloud. This structure means you are in full control, and even if our company servers were ever compromised, your private keys would remain completely safe and secure on your personal device.
Hardware Security Integration
Most modern phones include dedicated security hardware designed to store sensitive information safely. Trust Wallet taps into this built-in protection.
On iPhones, there’s something called the Secure Enclave. Think of it like a little locked box inside your phone where it keeps all the really sensitive stuff. Even the operating system can’t just open it up, and apps have no access to it at all. On Android devices with proper hardware support, the Android Keystore provides similar isolated storage.
Using these modules brings a few important benefits. Private keys aren’t floating around as readable files. Malware has a much harder time grabbing them. Exporting a key requires a deliberate action from the user. In short, common attacks that work on ordinary files become far less effective.
However, if you are using a rooted phone or a compromised device affected by malware, it would be considered a risk. Updating the hardware gives extra security, but the seed phrase remains the top pick. If that gets exposed, no hardware module can protect the wallet.
Core Security Features of Trust Wallet
Trust Wallet builds on its non-custodial foundation with several practical layers of protection. These don’t replace personal responsibility, but they do reduce the likelihood of simple mistakes or common scams. What follows are the key security features you interact with during daily use.
Encryption and Device Lock
Trust Wallet keeps your wallet data locked down right on your phone using AES-256 encryption—the same level of protection banks use. Your private keys aren’t just sitting there in plain text; they’re wrapped up tight and linked to your device’s security.
You can make it even tougher for anyone to get in by locking the app with a PIN or biometrics. Paired with your phone’s own lock screen, it creates two hurdles someone would have to clear just to open your wallet. If your phone has no lock, a weak PIN, or is shared with others, these protections aren’t very effective. But with a strong device lock and an app lock in place, your wallet becomes far harder to access without your permission.
Open-Source Code and Security Audits
A good chunk of Trust Wallet’s code is out in the open on GitHub. People can just go look at it—poke around, see how things work, call out anything that looks weird. It’s basically the opposite of those sketchy closed‑source crypto apps where you have no idea what’s going on behind the curtain.
And it's not just random users checking it. Big security firms like CertiK, Quantstamp, Cure53, Halborn, and others have gone through the wallet over the years. They dig up bugs, point out weak spots, and help fix things before they turn into real problems for anyone using it.
However, audits do not ensure flawlessness. They don’t stop new bugs from appearing in future updates, and they can’t protect users who fall for phishing attempts or approve malicious smart contracts. Audits are just one piece of a bigger security picture.
Transaction Signing and Risk Scanning
Trust Wallet handles everything right on your phone. It puts the transaction together, shows you the details, and waits for you to say “ok.” Only then does your private key do its thing—and it never leaves your device. After that, the signed transaction gets sent out to the blockchain.
There is also a built-in risk scanner in Trust Wallet. It won’t catch everything, but it helps highlight suspicious contracts or DApps, and warns you when permissions look unusual. That reduces risk, but it can’t replace careful reading and a bit of skepticism when interacting with unknown sites.
Data Privacy and Tracking
Trust Wallet doesn’t store your private keys, seed phrase, or personal identity on its servers. The wallet works without KYC, and the company doesn’t maintain central databases that connect real names to blockchain addresses. It does collect limited analytics to track app performance and stability, but these don’t map specific blockchain activity to a personal identity. For people who value privacy, that’s a meaningful difference compared to custodial platforms.
Of course, blockchains themselves are public. Anyone analyzing on-chain data can still trace activity across addresses unless they take extra privacy measures.
 Trust Wallet Doesn’t Store Your Private Keys, Seed Phrase, Or Personal Identity On Its Servers. Image Via Shutterstock
Trust Wallet Doesn’t Store Your Private Keys, Seed Phrase, Or Personal Identity On Its Servers. Image Via ShutterstockWhat Trust Wallet Does Not Offer (Missing Protections)
Trust Wallet puts you in full control of your crypto, but it’s not like a bank or an exchange with built-in safety nets. That doesn’t make it unsafe; it just works best if you are okay with handling your own security. Here’s what it doesn’t do.
No Two-Factor Authentication (2FA) for Transactions
On an exchange, sending funds usually involves multiple checks, like email confirmation, SMS codes, or authentication apps. Trust Wallet isn’t like a bank. Once your phone is unlocked and the app is open, you can send crypto without any extra verification.
That’s just how non-custodial wallets operate, but it also comes with some risks:
- If someone gets access to your unlocked device, they can send funds.
- A compromised phone has no extra verification layer to block unauthorized transfers.
- There’s no extra friction as you’d see on an exchange.
- Trust Wallet prioritizes mobility and speed. If you want exchange-style withdrawal confirmations, this isn’t the wallet for you.
No Multisig Wallet Support
A multisig wallet splits control across several people or devices. Think of a setup where two out of three approvals are needed before anything can move. It is a simple idea, but very effective for group wallets and for anyone holding a large amount of crypto. Multisig wallets need multiple approvals before money can move, which is great for shared wallets, team funds, or just adding an extra layer of safety for big holdings.
There is no simple built-in multisig feature in Trust Wallet. You can use outside tools to set this up, but the process isn't smooth. For everyday spending or using DApps, that’s usually fine. But if you’re holding a lot long term, a hardware wallet or a proper multisig setup is generally a safer bet.
No Insurance or Regulated Protection
Trust Wallet is not a bank, nor a regulated brokerage. It doesn’t custodize funds, which means it doesn’t offer insurance against hacks, user mistakes, or losses. There’s no FDIC-style coverage and no promise to reimburse you if something goes wrong.
This isn’t unique to Trust Wallet, as nearly all self-custodial wallets operate this way. But beginners often assume crypto wallets work like online banking, and that’s not how self-custody works.
Limited Customer Support
Trust Wallet’s support team cannot reset your seed phrase, recover a lost account, or reverse a transaction, as it does not hold your keys. They can only provide guidance. Many negative reviews come from users who expected help recovering lost funds or fixing blockchain mistakes that can’t be undone.
If you are used to customer service that can “fix” account problems, Trust Wallet will feel strict. That’s the nature of self-custody.
Trust Wallet’s Real-World Security Record
Trust Wallet’s been around since 2017, and the mobile app has been rock-solid. The only genuine issue happened with the browser extension, not the phone app.
Looking at real incidents helps paint an honest picture of the wallet’s safety record.
Major Incidents and How They Were Handled
Around 2022–2023, a bug in the browser extension hit a few new wallets, and roughly $170,000 was lost, according to CoinTelegraph. The issue only touched the new browser extension, not the mobile app. A fix went out quickly, and the team explained what happened in public. Anyone who lost money was compensated. It was not a small problem, but the response was quick and clear, and it’s a good reminder that early-stage features and extension wallets carry more risk than the core mobile app.
The real lesson for users is simple: keep your wallet updated and avoid storing large amounts in experimental features or early-stage extensions
Bug Bounties, Audits, and Ongoing Security Work
On the plus side, Trust Wallet runs a bug bounty program and does regular security checks to catch issues early and keep your funds safe. No wallet is ever “finished” from a security perspective, especially one that supports many blockchains and DApps. What matters is whether the team keeps up with the work, and Trust Wallet generally does.
What Users Actually Experience (Reviews and Community Sentiment)
Reviews help reveal how the wallet performs in the hands of everyday users. The picture is mixed, but predictable.
App Store and Play Store Ratings
Trust Wallet generally sits above the four-star mark on both major app stores, which gives a quick sense of how broad its appeal is.
Most positive reviews focus on the same themes. People like that the app feels simple, even when it handles a lot of chains in the background. They mention that it is easy to move between networks, stake assets, or make a quick swap without jumping through extra menus. The interface also gets credit for feeling familiar to new users while still offering enough depth for those who manage several wallets or hold assets across many blockchains.
 Trust Wallet Has a 4.5 Rating on Google Play.
Trust Wallet Has a 4.5 Rating on Google Play.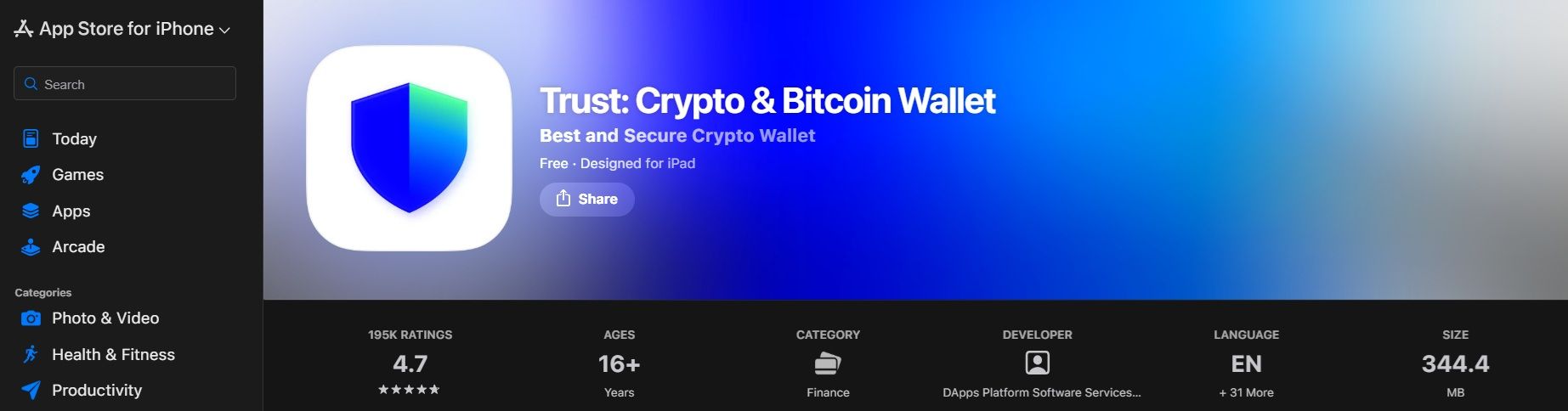 Trust Wallet Has a 4.7 Rating on Apple Store. Image via Apple App Store
Trust Wallet Has a 4.7 Rating on Apple Store. Image via Apple App StoreTrustpilot and Independent Reviews
Trustpilot tells a different story. The score is low, but the complaints follow familiar patterns. A large share of complaints comes from users who lost their seed phrase, fell for fake support accounts, or were tricked by phishing sites that mimic the real wallet. Others describe slow or unhelpful support, or assume their funds are “lost” when the genuine issue is a congested network or an unconfirmed transaction. Very few comments point to the wallet itself failing.
It's important to note that Trust Wallet has not claimed this profile.
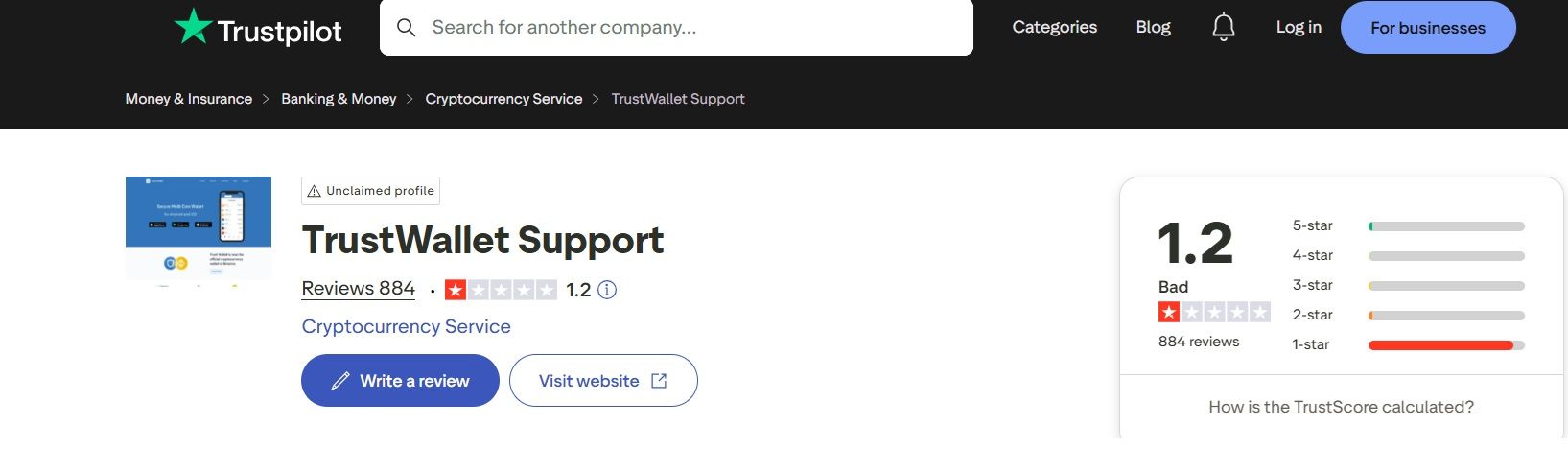 Trust Wallet Rating On Trustpilot Is Low, But There Is A Reason Behind It. Image via TrustPilot
Trust Wallet Rating On Trustpilot Is Low, But There Is A Reason Behind It. Image via TrustPilotWhat This Means for Safety
Real-world reviews make one thing clear: Trust Wallet itself isn’t usually the weak link. Instead, losses happen because of mistakes, poor device hygiene, scammers, or misunderstanding how DApps work. The wallet is safe when you use it cautiously—and unforgiving when you don’t.
Common Ways People Lose Funds with Trust Wallet
Most losses happen the same way again and again. Knowing these patterns helps users avoid them.
Phishing and Fake Apps
Scammers frequently impersonate Trust Wallet support or create fake apps and extensions. They often try to trick people into entering their seed phrase under the guise of “verification” or “unlocking” the wallet. The golden rule never changes: no legitimate service will ever ask for your seed phrase.
Malicious or Risky DApps
Some DApps request permissions that allow them to move tokens later without asking again. Others are outright scams disguised as farms, airdrops, or NFT tools. Trust Wallet’s scanner can warn you, but it can’t catch everything. Reading approval prompts carefully is essential.
Device Compromise and Insecure Backups
Many real-world compromises don’t come from sophisticated hacks. They come from screenshots of seed phrases stored in cloud backups, rooted devices, shared phones, or malware that captures screen data. Almost every attacker chooses the easiest path—stealing the seed phrase through user mistakes.
Human Error and Irreversible Mistakes
Crypto transactions can’t be undone. Sending to the wrong address, using the wrong network, approving a malicious contract, or miswriting a seed phrase can lead to permanent loss. Trust Wallet can’t reverse this because the blockchain itself can’t.
How Trust Wallet Keeps Transactions Secure
Trust Wallet follows the same principles used by other reputable non-custodial wallets. Understanding how transaction security works helps users trust the process.
Local Signing and Blockchain Confirmations
Every transaction is handled right on your phone. Your private key never leaves the device—only the signed transaction goes out to the blockchain. Once it’s confirmed, it’s there for good.
Approval Flows for DApps and Tokens
When you connect Trust Wallet to a DApp, the flow is simple. You connect, you review what the DApp wants permission to do, and you sign only if it looks right. You will be able to see the requested actions on every step, coupled with the estimated gas cost. Therefore, you need to be super attentive here. You can step away at any point if something feels wrong. Most problems happen when people just click “yes” without thinking.
Comparing Trust Wallet’s Safety to Other Wallets
This guide will now compare Trust Wallet with some other prominent wallets in this section. Each wallet and its own strengths and weaknesses. Take a look at this table in order to decide which wallet suits you the best.
Feature Comparison Table
Trust Wallet is all about being mobile, handling multiple chains, and jumping straight into DApps. MetaMask is amazing for browser-based DeFi and pairs nicely with hardware wallets. Coinbase Wallet has strong branding and optional cloud backups. Ledger is the gold standard for locking away crypto long term. At the end of the day, it’s about picking the wallet that fits your style and how you like to use crypto.
| Feature | Trust Wallet | MetaMask | Coinbase Wallet | Ledger (Nano X / S Plus / Stax) |
|---|---|---|---|---|
| Non-custodial | Yes | Yes | Yes | Yes |
| 2FA | No | No | Optional (via cloud backup login, not for sending) | Device-level only (PIN + Secure Element) |
| Multisig | No | Limited (via Smart Contract wallets, not native) | No | No (requires external multisig solutions) |
| Hardware Option | No | Supported via Ledger/Trezor | Supported via Ledger | Hardware wallet itself |
| DApp Browser | Yes (mobile) | Yes (browser extension + mobile) | Yes | No (uses Ledger Live integrations only) |
| Audit History | Mixed (not consistently audited) | Mixed (periodic reviews) | Audited (more consistent security reviews) | Audited firmware + Secure Element certifications |
| Recovery Support | Seed phrase only | Seed phrase only | Seed phrase or optional cloud backup | Seed phrase only |
| Ideal User Type | Mobile-first users who want broad chain support and fast DApp access | Web3 users focused on Ethereum, L2s, DeFi, and NFTs | Users who want a cleaner interface with strong Coinbase ecosystem ties | Long-term holders who want maximum security and offline protection |
Trust Wallet vs MetaMask
Trust Wallet just feels smoother on your phone, while MetaMask is the go-to if you’re doing DeFi in a browser. Both put you in full control, so your safety really comes down to how careful you are. If you mostly use mobile, Trust Wallet is super easy to use. If you’re deep in desktop DeFi, MetaMask is hard to beat.
Trust Wallet vs Coinbase Wallet
Coinbase Wallet sits closer to the regulated world and offers optional recovery tools tied to a Coinbase account. Trust Wallet stays entirely self-custodial. If you like the idea of a big company standing behind your tools, Coinbase Wallet may feel safer. If you prefer independence, Trust Wallet fits better.
Trust Wallet vs Ledger
A hardware wallet like Ledger is perfect for storing large amounts of crypto long-term. Trust Wallet, on the other hand, works better for everyday use—quick transactions and jumping into DApps. Many users end up using both: hardware for storage, Trust Wallet for active use.
Who Trust Wallet Is (and Isn’t) Right For
Trust Wallet fits certain user profiles better than others.
Good Fit
Trust Wallet is great if you want a mobile-first wallet that works with lots of blockchains and makes it easy-to-use DApps. It’s best for people who understand seed phrases and are comfortable following basic security habits. If you prefer holding your own keys and managing your own crypto, it’s a strong everyday option.
Poor Fit
It’s not ideal for people who frequently lose passwords, dislike managing backups, or plan to hold large amounts of crypto on a single device. If you want customer support that can reverse mistakes or recover lost keys, you won’t find that here.
 Trust Wallet Fits Certain User Profiles Better Than Others. Image Via Shutterstock
Trust Wallet Fits Certain User Profiles Better Than Others. Image Via ShutterstockBest Practices to Keep Trust Wallet Safe
These habits dramatically improve your safety with Trust Wallet.
Before You Install
Only download Trust Wallet from official app stores. Make sure the publisher is correct and avoid APKs or unofficial versions—scammers love setting up fake listings to trick new users.
During Setup
Write down the seed phrase on paper or metal and keep it offline. Don’t screenshot it. Store backups in separate locations. Set a strong device lock and enable the app lock.
Daily Use
Keep your phone updated and avoid dodgy apps. Watch for alerts from the risk scanner—they help catch problems before they happen. Read permission requests carefully. Never share your seed phrase—not with “support,” not with websites, not with anyone.
When Holding Larger Sums
Use a hardware wallet to store crypto long-term, and keep a separate “burner” wallet for trying out DApps and smaller transactions. Review and revoke older DApp permissions regularly.
Regulation, Insurance & Legal Protection
Trust Wallet sits outside traditional financial protections. Understanding that ahead of time prevents confusion later.
Is Trust Wallet Regulated?
Trust Wallet isn’t a custodial service, so it isn’t regulated like an exchange or a bank. It doesn’t hold funds, run accounts, or take deposits. Regulation applies more to the services you connect to—not the wallet itself.
Is Any of My Crypto Insured?
Crypto stored in Trust Wallet isn’t insured. There is no government-backed program covering losses. Some exchanges insure their own hot wallets, but that protection doesn’t extend to user-held keys.
What Are My Options If Something Goes Wrong?
If you lose your seed phrase, approve a malicious contract, or send funds to the wrong address, there’s no recovery path. You can file a police report in cases of clear fraud, but recovery is rare. In the self-custody world, prevention is everything.
Final Verdict
It is safe to say that Trust Wallet has achieved a reputable reputation, especially for everyday crypto use. Your keys stay safely on your device as it takes advantage of hardware-backed security, and it supports lots of blockchains and DApps.
For regular users with modest balances and good habits, it’s safe enough and very convenient. For DeFi users, it’s a strong mobile companion—as long as you stay careful with approvals and avoid unknown links. For large, long-term holdings, a hardware wallet should still be part of the setup.
Trust Wallet gives you freedom, flexibility, and control. It also holds you fully accountable for your own security. Used thoughtfully, it’s a solid choice. Used casually, it can be unforgiving.




