In crypto, we have a lot of sayings, but two that I feel hold true above all else as they pertain directly to crypto safety are:
“It’s not about how much you earn, it's about how much you keep.”
And
“Not your keys, not your coins.”
The past couple of years have been absolutely devasting for crypto users, a period that has highlighted the significance of the above sayings as we witnessed the collapse of crypto projects and firms that resulted in people losing thousands, and in some sad cases, their life savings. There are not many crypto holders who have made it through the past year unscathed, either from the insolvency of firms, the collapse of entire crypto ecosystems, or the macroeconomic events that have wiped billions of dollars from the sector and have plunged us into a crypto winter.
“It’s not about how much you earn”:
- People were enticed by the 18% ROI offered on Anchor Protocol until Terra collapsed and wiped out everyone. Earning 18% means nothing if you lose 100% of your capital, so, “It’s about how much you keep.” Unfortunately, Anchor Protocol is just one example in a swamp filled with failed projects, scams and rug-pulls.
“Not your keys”
- There are countless examples of exchange hacks that have resulted in customers losing their funds, and when Celsius faced insolvency issues they completely froze all customer withdrawals. Millions of dollars worth of customer funds that were held on Celsius were locked overnight, leaving users with no way to access their coins so… “Not your coins.”
I know it may seem like the digital currency landscape can be a minefield of risks, but there are millions of average folks who use digital assets every day without issue and many of us have been navigating the crypto waters safely for a number of years with minimal risks or losses. This article will help teach you how to keep crypto secure and keep those Sats safe.

Is Cryptocurrency Safe?
This is a question we get asked a lot here at the Coin Bureau and it’s a good question as every week there seems to be another hack, scam, or exploit. I often like to relate crypto to a real-world example to answer this question.
You can own a car with the most state-of-the-art security and alarm system, every bell and whistle you can think of to keep the car safe. But, if you park that car overnight in a bad neighbourhood and leave the keys on the hood, none of that security means a thing. If you are careless with the keys someone is going to take advantage.
 Good Crypto Habits Can be the Difference Between Stacking Sats and Losing Everything. Image via Shutterstock
Good Crypto Habits Can be the Difference Between Stacking Sats and Losing Everything. Image via ShutterstockCryptocurrency is similar, it is absolutely safe and secure if the user follows proper cyber security best practices, and you don’t even need to be a computer whiz to implement many of the steps laid out in this article.
The majority of safety issues people face with crypto fall under these categories:
- Scams - Users get greedy and chase unrealistic returns on investments or get duped by the wrong people online. Remember, if it seems too good to be true, it probably is.
- Centralization - Users keep their digital currency on an exchange that gets hacked, or on a platform that goes bust and loses their crypto. This is why self-custody is so important as that is the only way that a user can truly control and have authority over their funds.
- Lost Private Keys/Seed Phrase - This is the #1 most important step in self-custody. If you are going to take responsibility for your funds you need to make sure you have this recovery phrase stored someplace safe, secret, and offline. If the recovery seed phrase is lost or forgotten, nobody can help recover those funds. Much of this article will be focused on best practices for securing a recovery phrase.
 Losing This Little Piece of Paper or Letting It Fall Into The Wrong Hands Equates to a Very High Probability of You Losing Your Crypto Forever. Image via Shutterstock
Losing This Little Piece of Paper or Letting It Fall Into The Wrong Hands Equates to a Very High Probability of You Losing Your Crypto Forever. Image via Shutterstock- Computer Virus/Malware - This issue pertains to software wallets and people who store their seed phrases on a computer or in a cloud like Google Drive or iCloud (Don’t do this!). There are a plethora of viruses and malware that can be downloaded unknowingly that will scour your computer for seed phrases and private keys that a hacker can exploit. There have also been seed phrases kept in Google Drive and iCloud accounts that have been hacked into and stolen. This is why hardware wallets are the best way to keep your crypto safe.
- Hacks - Some people choose to store their secret recovery seed phrases in a cloud storage solution like Google Drive or iCloud, bad idea! There have been plenty of cases of hackers (even government agencies) gaining access to people’s cloud storage accounts and accessing their recovery phrases. Phishing attacks have also been on the rise in recent years.
 Don’t Let This Guy Steal Your Crypto. The Tips in This Article Will Help Significantly Decrease Risk of Hacks and Theft. Image via Shutterstock
Don’t Let This Guy Steal Your Crypto. The Tips in This Article Will Help Significantly Decrease Risk of Hacks and Theft. Image via Shutterstock- Not Double-Checking Crypto Addresses - Crypto addresses can be tricky, they are long and full of numbers and letters, nearly impossible to remember. Cryptocurrency transactions are irreversible, if a user makes one mistake in entering a crypto address, those funds will not be sent to the intended destination and are likely gone forever. There is even a malware program that can swap an address to a hacker’s address when you copy/paste, so you’ll want to follow the steps laid out in the next section and be diligent.
- Fake Crypto Apps - Google and the App store have come under intense scrutiny for allowing scammers and hackers to upload fake crypto apps to the store. Hackers have found a way to create apps that look exactly like legitimate apps and can even populate thousands of fake reviews and download numbers so the fake scam app is nearly indistinguishable from the real one. As soon as a user downloads the fake app and transfers funds to it, poof funds are gone.
 Fake Crypto Apps are Plaguing the Crypto Industry. Image via CoinTelegraph
Fake Crypto Apps are Plaguing the Crypto Industry. Image via CoinTelegraph- DeFi Protocols Not Thoroughly Audited - Many DeFi enthusiasts will jump into a DeFi protocol that has not been adequately audited or battle-tested yet. The past 12 months have seen a record number of wormhole and DeFi exploits resulting from shoddy developing and lack of audits conducted.
These are all pretty worrying things that result in the crypto industry being considered high-risk and unsafe. As long as you are aware of these things, don’t fall into the traps, and follow the best practices in this article then crypto can be used with a high degree of safety. Solutions to the above bullet points will be covered in the next section:
How Do I Keep My Crypto Safe?
When considering crypto safety, it is a good idea to tackle it from a realistic approach based on your own needs weighing out security vs convenience and having a tiered plan of attack.
What I mean is that you can turn your crypto holdings into the absolute Fort Knox of security, but that is going to be incredibly inconvenient. When I first got into crypto, I went overboard on security in a way that was too much of a hassle for me. It took me days to secure my home network, and it would take me about an hour to set everything up every time I wanted to access my funds.
It was so cumbersome and inconvenient that it made me never want to bother interacting with my funds as it became too much of a chore, so I dialed it back to a more balanced approach that works for me. Though, if you have the time, energy, and patience for that, then all the power to you.
 Max Security is an Option. Image via Shutterstock
Max Security is an Option. Image via ShutterstockPersonally, I like a more tiered approach that balances convenience and security.
To pull from a real-world example again, let’s think about the way we access our money. You don’t walk around with your life savings in your pocket, do you? Of course not. And you don’t keep the pocket money you need for day-to-day use held in a private vault with armed guards dug deep underground in an impenetrable fortress.
While it would be more convenient to always have access to our entire wealth within reach, and it would be more secure to keep all our funds in a vault that is difficult to access, those extremes are not a realistic way to manage our wealth. You probably keep most of your money in the bank for “safe” keeping, or in a safe if you don’t trust the banks. Maybe you keep a small stash of cash someplace “just in case,” but generally, we only carry on us what we need in a wallet or purse while keeping the rest secured.
 This Probably Isn’t the Most Secure Way to Store Your Assets. Image via Marca
This Probably Isn’t the Most Secure Way to Store Your Assets. Image via MarcaWhat does all this have to do with crypto security?
Crypto safety can be approached in a similar manner to how we store our traditional assets. There are 3-4 main ways that digital currency users store crypto, each one balancing convenience and security. The more convenient the solution, the less secure, and vice versa. Let’s break each of these down:
Keeping crypto on an Exchange - Least Secure, Most Convenient: Many crypto users keep their crypto on the same exchange that they purchased it on. This is likely because they do not understand self-custody, or they are too lazy to move it. This is a bad idea as we have seen dozens of exchange hacks where millions in customer funds were lost. Exchanges are large and very popular targets for hackers.
 Exchanges are Popular Targets for Hackers. Image via NBC
Exchanges are Popular Targets for Hackers. Image via NBCRemember that keeping your crypto on an exchange is the same as keeping money in a bank account. You do not actually physically hold nor control those funds. When keeping funds on an exchange, or indeed, in a bank, what you are actually holding is an IOU, a promise that the entity will pay you back when the time comes to withdrawal.
The exchange/bank can do whatever they want to with the funds held in their care and if they mismanage those funds and lose them, are hacked, or simply decide to deny you access for whatever reason, like the peaceful protesters in Canada who were blocked from their bank accounts as the government didn’t approve of their cause, there is very little you can do to recover those funds.
It also helps to think about this from a hacker’s point of view. As mentioned, every hacker knows about Binance, Coinbase, KuCoin, etc. and they have big bullseyes on them. Hackers don’t know about little old Jane and John Doe, nor their crypto holdings, (unless they brag about their crypto wealth online, another no-no), so by choosing to self-custody, you are a much smaller, and likely unknown target for hackers vs a major exchange.
 If an Exchange Get’s Hacked, Customer Funds are at Risk.
If an Exchange Get’s Hacked, Customer Funds are at Risk.There are a couple of exceptions here to the “never keep your crypto on an exchange” rule, which are:
- Platform tokens may provide perks and benefits for holding a certain amount on an exchange.
- Day traders who actively trade need to keep funds on an exchange.
- If you anticipate selling in the near future.
- To access the plethora of earn or staking products, though this is riskier than withdrawing off the exchange to a self-custody crypto wallet.
Another exception to this rule that many users may disagree with, but hey, let's be honest and understand that not everyone is responsible enough for self-custody. If you are someone who is disorganized, forgetful, have a habit of losing/misplacing things and are your own worst enemy, then trusting yourself to keep your recovery phrase safe may not be the best choice and keeping funds on an exchange may be the better option. Though I do encourage everyone to learn and practice responsible behaviour and figure out ways to self-custody in a safe and responsible manner.
 The Responsibility of Self-Custody May Not Be For You. Image via Shutterstock
The Responsibility of Self-Custody May Not Be For You. Image via ShutterstockThe last example of when keeping funds on an exchange may be a good idea is if you are someone with no home base and no secure place or way to store crypto. If you are travelling or living out a backpack, keeping hardware wallets and recovery phrases in a backpack in a hostel is probably less secure than on an exchange.
If you are determined not to self-custody, but also do not want to keep funds on an exchange, there are crypto custodial provider solutions as well. These are professional companies that will provide virtual currency storage solutions and handle all the responsibility that comes with crypto storage for you. Some examples here are Coinbase Custody and Gemini, but there are dozens of alternatives as well if you search for “crypto custodian,” just be sure to pick a reputable one that is well-known in the industry.
If you currently have funds on an exchange and want to learn more about how to self-custody your assets, Guy has a fantastic video on there here:
Use a Software Wallet - Medium Security, High Convenience: A software wallet (hot wallet) offers a great mix of security and convenience. These are crypto wallets that can be downloaded onto a phone or a computer. When users hold their crypto in a software wallet, they hold the keys to their crypto, meaning that they are the sole owners and controllers of those funds, 100% responsible for the assets held within the wallet. This makes software wallets more secure than keeping them on an exchange, assuming, of course, that the user follows responsible crypto usage.
 The Exodus Wallet is a Popular Software Wallet for both Mobile and Computer. Image via Exodus
The Exodus Wallet is a Popular Software Wallet for both Mobile and Computer. Image via ExodusThe reason that this is not the most secure option is that these wallets are installed on devices with internet access. Internet access is the #1 attack vector for any crypto device as hackers have ways of accessing devices remotely through online methods. These devices are also at risk of viruses and malware that can expose private keys and recovery phrases. Other attack vectors with software wallets on a computer or mobile phone include Bluetooth access, NFC and mobile data. Anything that transmits or receives any sort of data can be considered an attack surface that could be exploited.
Mobile wallets are very convenient and the best choice for users who like to use their crypto on the go to make daily purchases. We will cover some of the steps you can take to use a software wallet in the most secure manner possible.
Use a Hardware Wallet - High Security, Low Convenience: Hardware wallets (cold wallets) provide the most optimal storage solution for crypto safety. Hardware wallets are a must for anyone serious about crypto security. These are little devices that store your private keys offline, and most are completely air-gapped, meaning they have no internet access, NPC or Bluetooth options, and do not transmit any data in or out wirelessly, meaning there is no way they can be accessed remotely.
 Hardware Wallets are the Holy Grail of Secure Crypto Storage. Image via Shutterstock
Hardware Wallets are the Holy Grail of Secure Crypto Storage. Image via ShutterstockThese devices plug into a computer or interface with a mobile phone which provides users with the ability to transact with their crypto while never exposing their private keys to any device with online access.
The drawback here is that these aren’t very convenient as they need to be plugged in or turned on and in your possession, along with a computer or phone anytime a transaction needs to be made, making these less convenient than a simple mobile wallet. These devices should also be kept hidden and secure, so they are not ideal for day-to-day out-and-about crypto transactions.
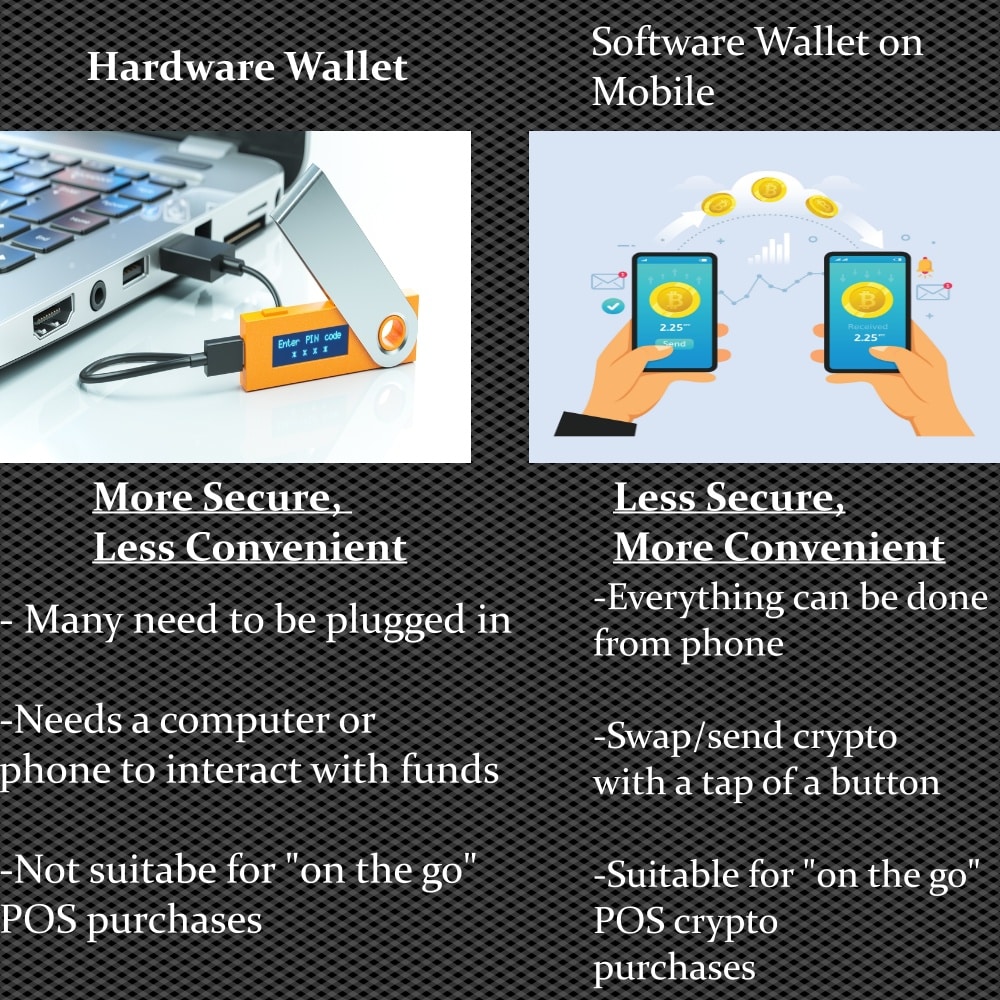 Images via Shutterstock.
Images via Shutterstock.You may have noticed the terms “hot wallet” and “cold wallet” used above. A hot wallet simply refers to any wallet or device with internet access while a cold wallet is anything with no internet connectivity.
It is a commonly believed misconception that a crypto wallet actually stores your crypto. This is not true, a cryptocurrency wallet simply controls the private keys needed to access funds that never leave the blockchain network. Bitcoin cannot magically jump off the Bitcoin network and enter your wallet, that is not how cryptocurrency wallets work, and why a recovery phrase can be used to recover your crypto even if you smash or lose a crypto wallet. This is an important topic to understand, I explain this in more detail in my review about one of the most secure cryptocurrency wallets ever made, the NGRAVE ZERO.
Paper Wallet - Most Secure, Least Convenient: Paper wallets are the most secure as I am pretty sure it is impossible to hack a piece of paper. These are simply pieces of paper that can be generated and printed, then hidden. They have a wallet’s public and private keys on them but are not very popular anymore as hardware wallets have become the industry standard and can conveniently interface with web3 applications and DApps. Not many people other than hardcore cypher punks use paper wallets anymore.
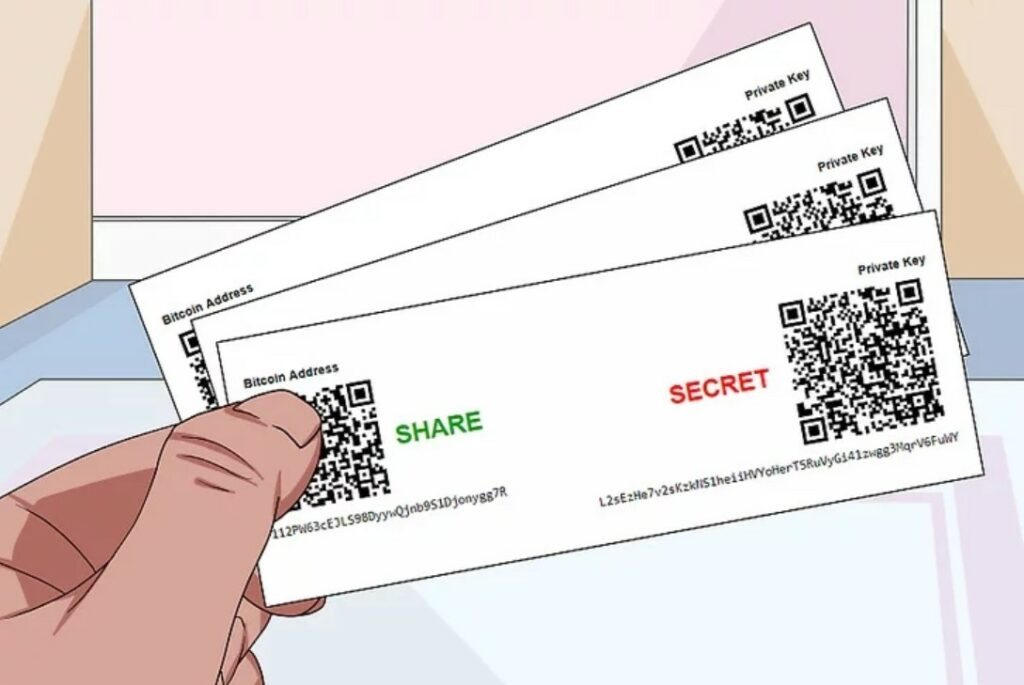 An Example of a Printable Paper Crypto Wallet. Image via Wiki
An Example of a Printable Paper Crypto Wallet. Image via WikiThese are also the least convenient as the piece of paper also cannot send virtual currency transactions or perform many of the functions of software and hardware wallets.
Okay, now we have an understanding of the different methods for storing crypto, how can we use this information to balance security and convenience?
If you are someone who doesn’t transact in crypto often and you are more of a long-term hodler, then the best approach would likely be to just keep all your funds in a hardware wallet. Many users spread their funds across more than one wallet to avoid a single point of failure risk in the unlikely event that a recovery seed phrase gets compromised.
The most balanced approach followed by many responsible crypto users is that they will keep the majority of their funds on a hardware wallet, treating that like a safe or bank vault, then use a software wallet as more like a physical wallet, where they will only keep an amount of funds that they anticipate needing to access for on the go for payments or in the short term. Staking is another popular reason to hold crypto in a software wallet, but this is not without risks. Funds should only be kept on an exchange once you are ready to sell, or if you are actively trading.
That covers crypto storage. Now let’s dive into how to avoid the pitfalls highlighted in the first section.
How to Protect Crypto Against Scams
This one is pretty self-explanatory, if something seems “off,” or unrealistic returns are being promised, big red flag. I won’t go into too much detail here as we have an entire article dedicated to How to Avoid Crypto Scams and one for How to Avoid Rug-Pulls that are definitely worth checking out.
 Image via Shutterstock
Image via ShutterstockOne of my favourite DeFi tools is called DappRadar. It is a useful site to track DeFi, NFT and gaming projects and for finding legitimate DApps.
How to Protect Crypto Against Centralization Risks
The best way to avoid this risk is to self-custody your own crypto with a cryptocurrency wallet and not leave it on an exchange, lending platform, or any platform. Choosing to self-custody your crypto is one of the biggest steps you can take to protect yourself. If you are looking for the best wallets to do this, we have an article on our top picks for Safe Crypto Mobile Wallets and The Best Hardware Wallets for Crypto Security.
There is also a centralization risk around certain crypto projects that could fall under regulatory scrutiny. Projects like Polygon and Solana are quite centralized, as in, they have a team behind the project, while other cryptocurrencies like Bitcoin have no developer team and had no ICO, undergoing what is known as a “fair launch.” Any project that had a token sale could be deemed a security and follow the fate of XRP. You can learn more about the risks of different cryptocurrencies in our article on How to Build a Crypto Portfolio.
Guy also has a video where he covers the most Decentralized coins, as the more centralized a project is, the higher the probability it has of facing certain risks:
How to Secure Crypto Against Lost Recovery Seed Phrases
If you are going to choose to self-custody your crypto, it is paramount that you follow the absolute best practices and highest standards when securing your recovery seed phrase and private keys. This step is so important that I will be covering it in great detail continuously throughout this article. Remember that a recovery phrase is the only way to recover crypto from a lost or broken crypto wallet.
How to Protect Crypto Against a Computer Virus/Malware
Using a hardware wallet is one of the best ways to protect against this risk. Any software wallets or seed phrases stored on your computer are at massive risk if your computer becomes infected. A hardware wallet can be used on a computer with a virus with no additional risk, though it is still a good idea to keep your computer clean for general safe online habits. I will be covering this in far greater detail in the cyber security section.
How to Protect Crypto Against Hacks
If a hacker manages to gain remote access to your computer or mobile, they have a strong chance of gaining access to your private keys and/or recovery phrase if you use a software wallet. Using a hardware wallet is the best way to protect against this as the wallet keeps your private keys offline and outside the reach of hackers.
There have been no known successful remote hacks on hardware wallets, but there have been cases of hackers using a technique called power glitching where they have been able to access the crypto on a hardware wallet if it is in their possession.
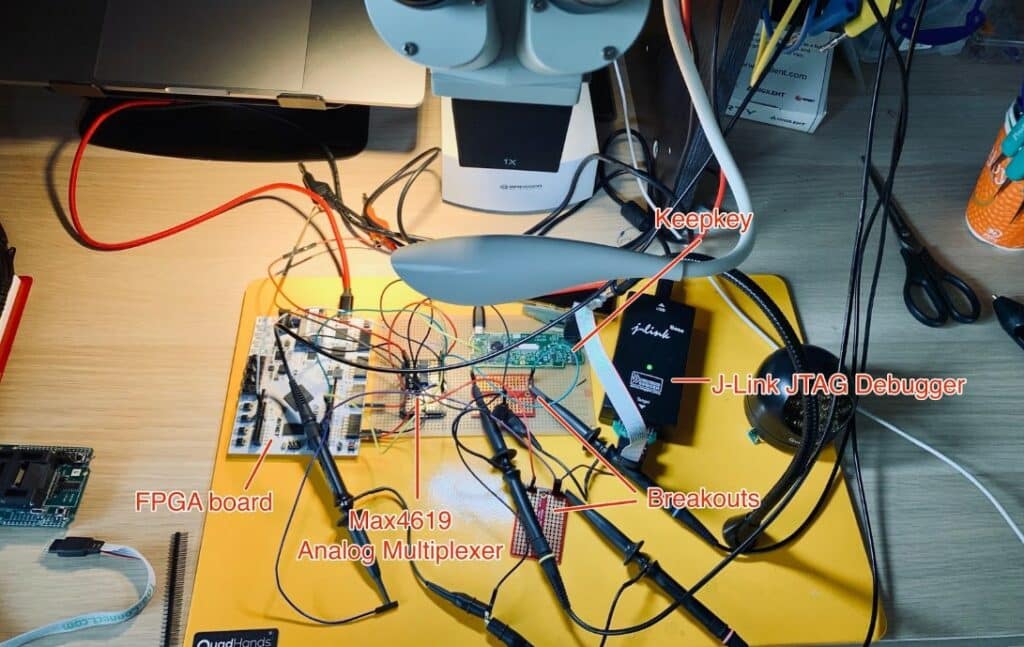 A Look at a Power Glitching Setup. Image via blog.kraken
A Look at a Power Glitching Setup. Image via blog.krakenThis is a highly sophisticated technique that is unlikely to happen, but it is still a good idea to keep your hardware wallet in a secure and secret location. The cyber security section next will cover protection against hacks in more detail.
How to Protect Crypto From Sending it to a Wrong Address
One of the best and worst features of crypto is that transactions are irreversible. If you make a mistake or send to a wrong address, there is no getting those funds back unless the person that received them sends them back.
This is also a strength as it means that nobody can reverse a transaction, nobody has control over transactions or authority over a network, unlike banks who can pull money from people’s accounts as they please. The downside of this is that you need to make 1,000% sure that you are sending to the right place. Follow these steps and you won’t have a problem:
- Always copy and paste the destination address OR use QR code scanning technology if available as that is very secure and convenient. Be sure there are no white spaces before or after the string of characters when pasting.
- Even if you copy/pasted, always double-check the address is correct after pasting as clipboard hijacking malware could have swapped the intended address with a hacker’s address.
- Consider acquiring a crypto domain as it is way easier to simply send crypto to an address like “guy.eth” than using long and complex crypto addresses. Plus, you don’t need to worry about clipboard hijackers or typos.
- Verify the network you are sending on. This is very important and often ignored by early crypto users. This is a mistake that can result in permanent loss of funds. When withdrawing from Binance, for example, many assets are supported on multiple networks, and you are given the option to choose one. Select the network that the wallet or platform supports that you are trying to send to, don’t just guess or pick the cheapest one!
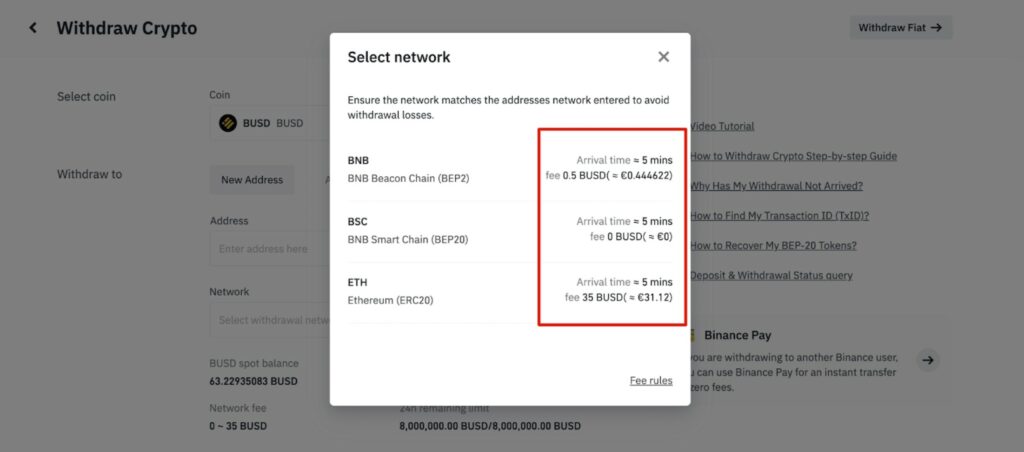 A Look at The Multiple Networks You Can Choose to Withdraw From on Binance. Image via Binance
A Look at The Multiple Networks You Can Choose to Withdraw From on Binance. Image via BinanceI have seen this happen hundreds of times, often resulting in users losing everything. If you are unsure, ask the support team before sending. We have an article that explains many of the different networks that goes into further detail on this. This is a very simple, yet important concept to understand. Exodus also has a great article that covers this concept with step-by-step examples.
- Double-check to see if you need an ID tag/Destination tag or Memo for your transaction. Most exchanges require a Destination Tag or Memo to receive funds, and if you don’t enter the right one, you may lose your virtual currencies forever.
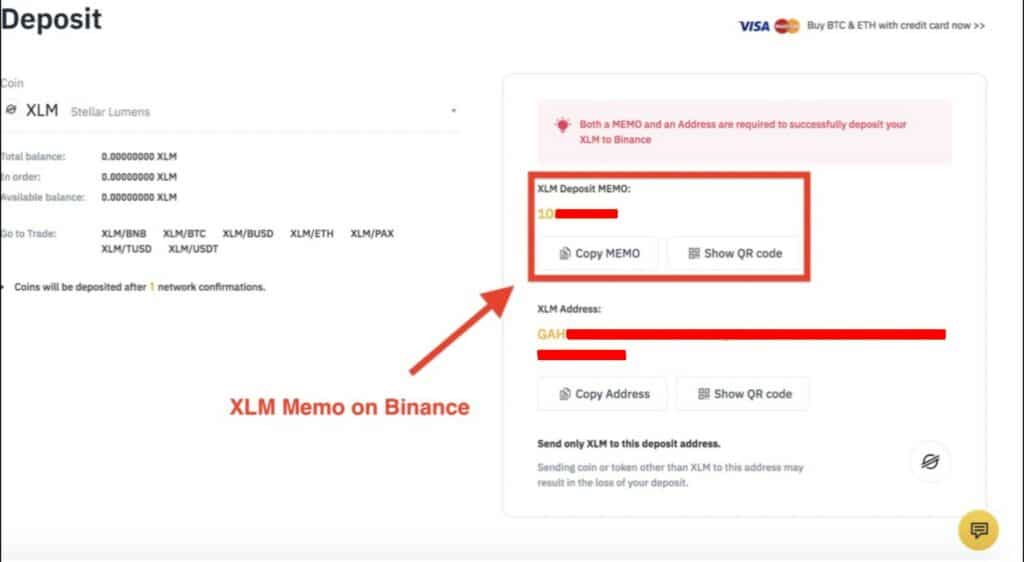 An Example of a Memo Needed To Deposit XLM on Binance.
An Example of a Memo Needed To Deposit XLM on Binance.The most common crypto assets that require ID tags or Memos are XRP, XLM, ATOM, BNB, XEM, KAVA, EOS, and a few more. Here is a good article from Coinbase that explains Destination Tags
How to Protect Crypto Against Fake Crypto Apps
This one is heart-breaking as it often hits new crypto users who think they are doing everything right then they lose their crypto. Fake crypto apps can be very difficult to detect and have affected a lot of users because there are so many fake apps in app stores that exactly mirror the official app, complete with reviews and comments, nearly indistinguishable from the real one.
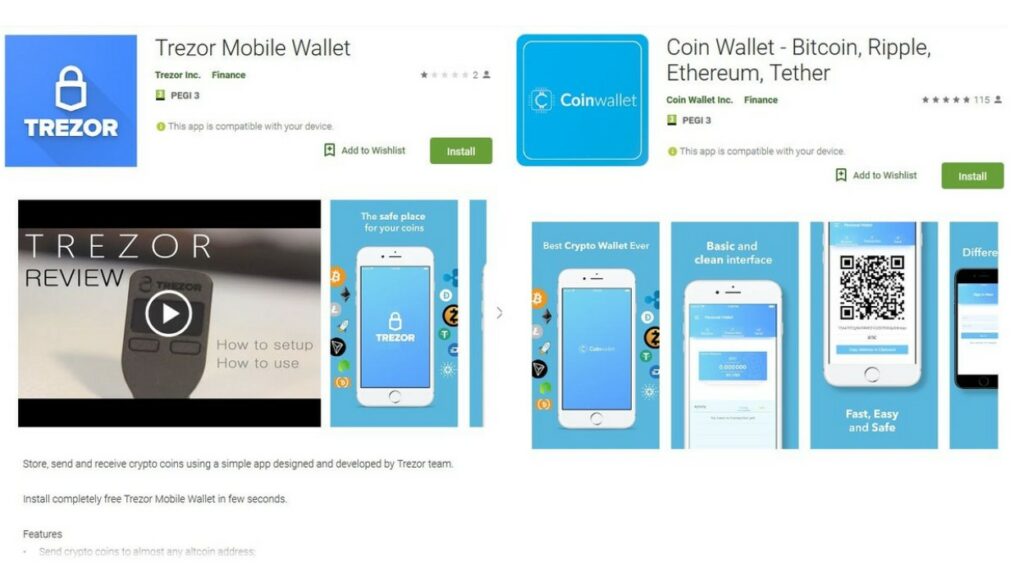 Here are Two Examples of Scam Apps in the App Store. Image via App Store.
Here are Two Examples of Scam Apps in the App Store. Image via App Store.The best way to protect against this is by never searching for crypto apps directly from an app store. Always find the direct download link or redirect link to the app store from the company’s official website or whitepaper.
When accessing DApps or DeFi, there are plenty of phishing websites set up that have a very similar URL that mirrors the real platform. Finding the link from the project’s whitepaper or Docs is a good step to find the legitimate URL, then bookmark it once you have it. A browser extension like Phishfort can help flag known phishing sites as well.
How to Secure Crypto Against a DeFi Protocol Exploit
I know it can be hard not to jump in and test out some exciting new DeFi project that is offering some next-generation products and services, but fortune often pays the patient.
The past year has seen record numbers of DeFi and wormhole hacks and exploits. This has primarily been the result of rushed releases from project teams, novice developers, and DeFi projects not being thoroughly audited. Blockchain audits are incredibly important, and something that is taken seriously by the most prominent protocols like 1Inch, Aave, Compound and more.
 Don’t Become One of These Statistics! DeFi Can be Enjoyed Safety When Used Responsibly. Image via via Protocol.com
Don’t Become One of These Statistics! DeFi Can be Enjoyed Safety When Used Responsibly. Image via via Protocol.comThe best way to protect yourself here is by using the most long-standing and battle-tested DApps and understanding blockchain audits, which is easy once you know what to look for. There are two articles I recommend here to navigate the DeFi waters as safely as possible:
- Safety and Security for DeFi and Web3 - From Exodus
- How to Understand Blockchain Audits - From Coin Bureau
Okay, now we know the safest way to store crypto, and how to avoid the traps that crypto holders fall into. Now let’s tackle cyber security and some crypto hygiene best practices.
How to Keep Crypto Secure
As alluded to, if you are transacting in crypto or storing private keys and recovery phrases on a device that is full of viruses and malware, you are likely to have a bad time. If you are inviting hackers onto your network and not protecting your online activity, you are likely to have a bad time. If you lose your recovery phrase, then you are definitely going to have a bad time!
 Following the Best Practices in This Section Will Help You Avoid Having a Bad Time in Crypto. Image via Shutterstock
Following the Best Practices in This Section Will Help You Avoid Having a Bad Time in Crypto. Image via ShutterstockJust like with crypto storage, there are different levels of security here and we can take another tiered approach. I am going to be honest when I say that the most secure tier 3 is a serious pain and highly inconvenient, most users won’t go as far as tier 3. Don’t feel bad if you don’t follow every point in this section, but the more you follow, the more secure you will be.
Tier 1 Crypto Security
If you are only willing to follow one of the 3 tiers, make it this one as this is easy and won’t only help with secure crypto storage, but general online security. This section will help with things like password, banking, identity, and crypto safety, basically, your entire online life will benefit from this tier.
These are the basic security measures that everyone should follow. If you don’t follow this tier, you may as well be shouting your passwords to your neighbours out the window and giving your crypto away.
- Protect your 12/24-word secret recovery/seed phrase at all costs! This is the #1 rule in crypto. This phrase is literally the master key to your wallet, anyone who has this can access your funds. This phrase is also the only way you can recover your funds if you lose or break a hardware wallet or the phone/computer that a software wallet was installed on. You are also the only person who should have access to this, meaning that nobody can help recover a wallet for you, not even the company who made the wallet. Many people think that it works similar to how you can contact a company to reset or recover a forgotten password, but it doesn't work like that. If you lose this phrase, you're hooped.
- Write this phrase down on paper or use a fire and flood-proof metal seed phrase engraving plate like the ones in the Coin Bureau Merch Store. If you use paper, make two copies kept it separate secret locations and laminate them with clear tape to protect them.
 Whether You Write the Recovery Phrase on Paper or a More Durable Metal Alternative, Keep it Safe! Image via Merch Store
Whether You Write the Recovery Phrase on Paper or a More Durable Metal Alternative, Keep it Safe! Image via Merch Store- This seed phrase needs to be written down in the correct order with correct spelling, so be diligent here and record this phrase exactly the way it is displayed to you on the screen when you set up a new hardware or software wallet.
- You should be alone and someplace without distractions when setting up a new wallet and writing down this phrase.
- Store this phrase someplace private and known only by you or your most trusted family or friends. You do not want these phrases falling into the wrong hands.
- Create two copies of this phrase and keep them in separate locations so if one gets lost in a fire or flood, you have a backup.
- NEVER enter this phrase online. There are common scams where fake DApps and websites will ask you to enter this phrase for whatever reason, this will always be a scam. No crypto protocols will require this info. Also, NEVER give this phrase to the customer support staff for any company.
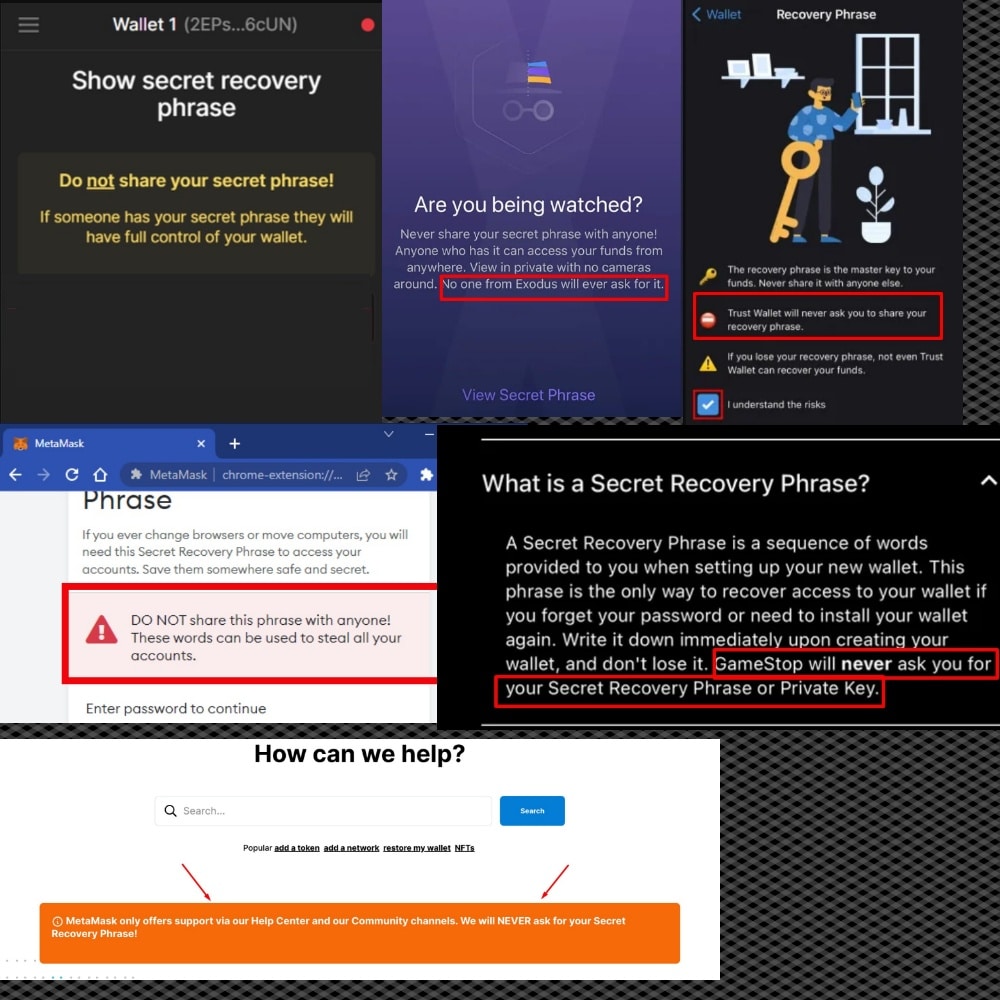 A Collage of Multiple Crypto Companies Saying They Will Never Ask for Your Recovery Phrase.
A Collage of Multiple Crypto Companies Saying They Will Never Ask for Your Recovery Phrase.Another popular scam comes from people online on chat sites like Discord, Reddit, and Telegram who pretend to work for customer support for a wallet company. When someone messages a community asking a question, these scammers will pose as support staff and DM the person saying they need this info to help resolve their problem. No customer support rep will ever ask for this information, nor would they ever need it to provide support, hence all the disclaimers in the image above. Wallets are designed to be used with recovery phrases that are kept 100% secret and known only by the wallet owner.
- Do not copy your private keys. Private keys are similar to a recovery phrase, in that they provide access to your crypto assets. Ethereum and all ERC20 assets, for example, are controlled by the same private key, so if this gets compromised, say goodbye to your precious Ethereum altcoins! Your private keys live inside your password-protected and encrypted crypto wallet, and that is where they should stay. Unless you are performing advanced tasks, you do not need to access your private keys, the wallet manages these for you. You do not need to write these down or store them separately.
- Password protect your crypto device. Hardware and Software wallets can be protected by a password, biometrics, or pin, be sure to make a password that only you know. Don’t choose 1234 or “password123”, you’re better than that. Anyone who gets access to your device and guesses the pin or password can access your crypto.
- Use passwords/biometrics on your computer and mobile. This one is pretty obvious. Your device should have some sort of protection in place in case it falls into the wrong hands. Your device should lock and require a password every time it sits idle for a few minutes, or the lid is closed.
 All Computers, Mobiles, and Wallets Should be Password, Pin, or Biometrically Protected. Image via Shutterstock.
All Computers, Mobiles, and Wallets Should be Password, Pin, or Biometrically Protected. Image via Shutterstock.In the terrible event your computer or mobile is lost or stolen, you can use a program like Find My Device by Google or Find My by Apple to locate the device. These programs can also be used to wipe the device remotely if it was stolen and you cannot retrieve it. Very handy!
- Keep your operating system and crypto app up to date. Operating system updates are a big one, as these are often done to patch security issues and vulnerabilities. If you’re still using Windows Vista and trying to use crypto, you’re likely to have a bad time. Many software wallets like Exodus will release an update every 2 weeks which continuously enhances security and provides patches so always keep software up to date. Be sure to only use legitimate operating systems and don’t use crypto on a jailbroken device as this can compromise security.
- Using jailbroken devices or illegitimate operating systems can come with “back doors” that give hackers access to your computer or mobile device.
- Many security experts agree that updating your operating system regularly is the most important step you can take to safeguard your computer.
- Don’t download/pirate from or visit suspicious sites. I know, now I’m just sounding like your dad, or someone trying to protect the interests of big media companies, but this step is very important! While I cannot condone doing anything illegal online, if you are someone who enjoys downloading or streaming (legally, of course!) I’ll suggest a workaround in a moment to show that I’m still “hip with the kids.” Downloading torrents or clicking on popups and links are the main ways viruses and malware get onto our computers.
- Do not download any kind of pirated material, whether it be videos, computer programs, video games, or even documents…Unless you want malware.
- Don’t click on popups or links randomly sent to you via social media. I often annoy my friends by taking this step. Any time someone sends me something, I always message them first before clicking on it and asking, “hey, did you mean to send me that?” To that, their response is usually, “yes, you paranoid weirdo!” I am not kidding though, there have been about 6 or 7 cases where the response was, “No, I was hacked! Don’t click on that!” And I was glad I double-checked.
- Do not open attachments in emails if you do not trust the sender. If it was sent from someone you trust but looks odd, you can always email them back and verify if they meant to send it before you open it.
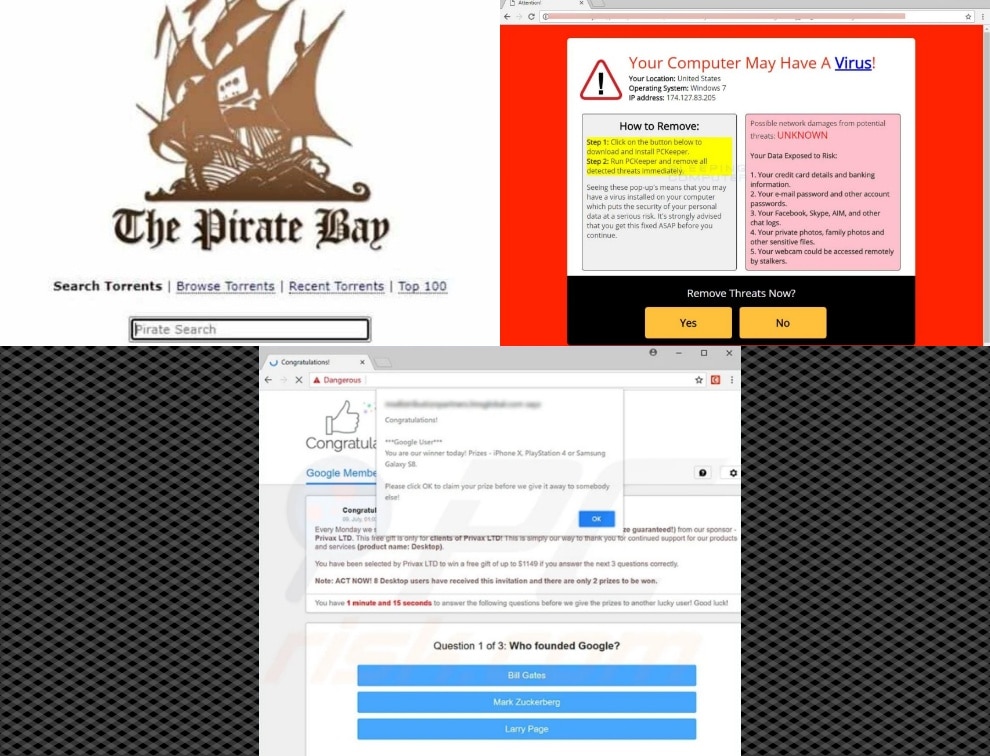 Avoid Visiting Websites And Clicking on Popups Like These. Especially on Any Device You Use for Crypto and Banking.
Avoid Visiting Websites And Clicking on Popups Like These. Especially on Any Device You Use for Crypto and Banking.Okay, now the workaround. If you can, many crypto users have one computer and/or one phone that is only used for crypto, then they have their day-to-day computer/phone for their downloading, streaming, and general daily use. This is one of the best ways to ensure the device you use crypto on remains virus and malware free.
Pro tip: Use a free website like haveibeenpwned to see if any of your passwords or phone number have been involved in any breaches or hacks. Change your password immediately if it has. If you receive a link, before clicking on it you can copy and paste it into the free website virustotal.com to see if it’s a virus before opening it. Most antivirus programs also allow you to right-click on a link or a download before opening it and scan it for viruses. I love that last one and use it all the time.
Alright, that covers the fairly simple steps you can take that should protect you against most threats and keep yourself and your crypto secure online. Let’s kick it up a notch.
Tier 2 Crypto Security
This tier has a mix of crypto and general cyber security tips. Some of these concepts are a bit more advanced but definitely worth following.
- Easy stuff- Use a hardware wallet for the majority of your funds and don’t brag to Billy down at the pub about your crypto holdings or show screenshots of your 10x gains on Twitter. This is just inviting hacker attention and maybe Billy is low on cash or heard that Bitcoin is kind of cool and wouldn’t hesitate to initiate a $5 wrench attack to get yours.
 Image via explainxkcd.com
Image via explainxkcd.com- Use 2FA when applicable- Any time 2FA is an option, it should be enabled. If a hacker gets your username and password, they still won’t be able to access your account unless they also have your phone or device with the 2FA authenticator on it, a device that should also be password or biometrically protected. Good luck with that, hackers.
Google Authenticator, Authy or the YubiKey are good choices here. Don’t use mobile SMS for 2-factor authentication as a slew of “Sim Swap Attacks” have resulted in users having their crypto exchange and bank accounts breached. Email 2FA is also not the best choice because if a hacker has enough info to breach a bank or crypto account, they may also have your email login info. You can learn more about this in an article from Wire on why you should Stop Using Texts for 2FA.
 Enabling 2FA Everywhere You Can Greatly Enhances Your Online Protection. Image via Shutterstock
Enabling 2FA Everywhere You Can Greatly Enhances Your Online Protection. Image via ShutterstockNote that many software wallets will not support 2FA which is a complaint from many crypto users, but it shouldn’t be. 2FA requires the sharing of user data and usernames or email addresses, plus relies on the use of centralized servers. As crypto wallets are designed to be used anonymously and without reliance on a centralized entity that could become a point of failure or attack target, most trusted crypto wallets cannot be linked to a 2FA account which is a good thing.
- Use a password manager- This is something I did not do for years, and now that I use one, I have no idea how I ever survived without it…Oh wait, yes, I do, I used the same password for everything. D’OH!
If you are someone who uses the same password for everything, like 15-year-old me, please stop right now. Use something like LastPass, it is completely free, and it can generate and save hundreds of passwords. It is a big upfront time commitment to change all of your passwords, but once each password is generated and saved by a password manager, it makes your life so much more secure and easier going forward.
 Password Management Is a Huge Pain in the Butt. Let a Password Manager Do the Hard Work. Image via LastPass.com
Password Management Is a Huge Pain in the Butt. Let a Password Manager Do the Hard Work. Image via LastPass.comIf you want to explore password managers, which I highly recommend, here is a great article from PCMag where they cover the Best Free Password Managers.
- Use a VPN and firewall- This is where we start getting into more high-end security measures. These are crucial for anyone who wants to take their security seriously, especially for those who find themselves often using public WiFi.
A firewall is a necessary piece of kit on your computer but can also be used on a router. Firewalls protect your network from unauthorized traffic by blocking malicious traffic from the internet to your computer. Simply put, it keeps the bad stuff out.
Here is a great visual from Wallarm simplifying this concept:
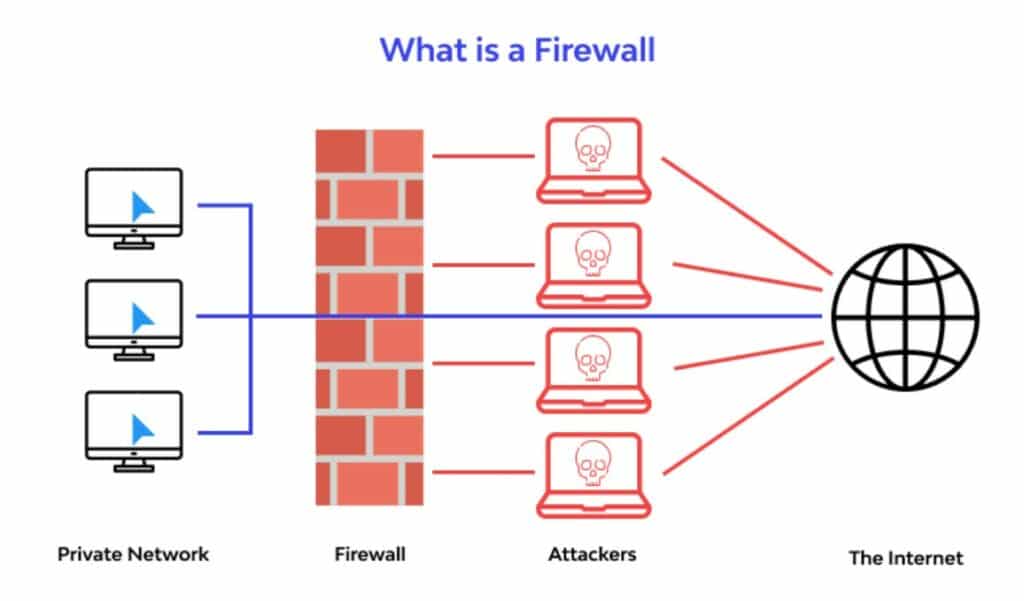 Source: Wallarm.com
Source: Wallarm.com
A VPN gives users an extra layer of privacy by securing and encrypting the communication your computer is sharing with the internet, keeping data hidden from prying eyes online. It prevents people from intercepting your data or spying on your online activity. Surfing the internet without a VPN is kind of like if you were shouting across the street to your neighbour to have a conversation, all your neighbours could listen in. But if you used a couple of cans tied together with a string and spoke normally, no eavesdroppers could listen in.
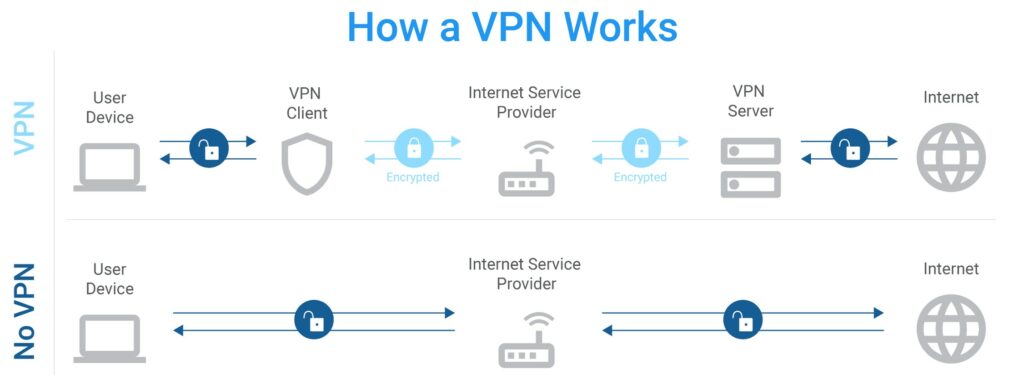 A Look At VPNs. Image via SecurityMetrics.com
A Look At VPNs. Image via SecurityMetrics.comHere are a couple of best practices here:
- Don’t ever use public WiFi without a firewall and VPN. Even with these, I avoid doing personal banking or crypto activity on public WiFi.
- All operating systems come with a firewall built in these days, which is often good enough, but if you want to go above and beyond, here is a good article from TechRadar showing their Top Picks for Best Firewalls.
- There are plenty of free and paid VPNs to choose from. I have tried dozens of them and researched these thoroughly over the years. As a penny pincher, I tried very hard to find a free one that works well, but most of the free ones are pretty bad, to be honest. VPNs are one of the very few times I suggest sucking it up and paying. Luckily, they are very cheap and a good one can be used for a couple of bucks a month. My favourite one is ExpressVPN, but I know a lot of cybersecurity professionals who opt for NordVPN and Proton VPN.
- Check to see if your router can support a VPN too as many of them can nowadays. Many VPN providers will keep your device safe online, while also offering solutions that can cover the router as well at no additional cost. This will ensure end-to-end encryption, encrypting both outgoing and incoming data.
- Up your browser extension game- There are some fantastic browser extensions that can help keep you safe online. Phishfort helps identify what websites are legit and which ones are phishing websites designed to look like the real ones. Many browsers now have a built-in setting that only allows you to visit sites that are HTTPS encrypted, but if not, you can use browser extensions that will block non-encrypted websites. Finally, uBlock Origin is a great ad-blocking extension that can block not only intrusive ads, but trackers and pop-ups that can contain viruses and malware. All these extensions are free, so there is no reason not to use them.
- Use Antivirus and Anti-Malware Programs- Come on, you knew this was coming. If you don’t use a good antivirus yet, after likely knowing about them for years, why not?
 Purchasing Decent Software May be the Best Investment You Ever Make if it Prevents Crypto Theft. Image via Shutterstock
Purchasing Decent Software May be the Best Investment You Ever Make if it Prevents Crypto Theft. Image via ShutterstockThese programs are great for keeping yourself and your computer safe and clean. Using an antivirus has so many benefits, with the biggest ones being:
- Keeping your computer working for longer - Viruses can frag a computer, fast. Using an antivirus can keep your computer running optimally for years, meaning you won't need to constantly be buying new ones.
- Keeping your personal information safe - We use our devices for everything from banking, to work, to crypto, etc. If a virus gives a hacker backdoor access to our devices, they can pretty much steal our entire identity with all our passwords and account details. Imagine how much damage they could cause.
Now, don’t think that good antivirus programs are a substitute for safe online browsing. Just cause you have a good antivirus that doesn’t mean you can go and download all you want from shady websites, you should still practice good online hygiene.
My favourite low-cost antivirus is Webroot, as it is award-winning and trusted by governments and academic institutions. It is the only antivirus that I know of that will quarantine specific infections and allow a roll-back to before that particular file or program was infected so you do not have to lose the entire thing. It is like a mini-time machine for every singular file or program on your computer or mobile phone. My favourite anti-malware is Malwarebytes, and here is PCMag’s Top Picks for Antivirus Software.
Tier 3 Crypto Security
Now you may be thinking, “Wait, there’s more?!” You bet, giddy up cause these next steps will really bulletproof your online presence and ensure your crypto remains as safe as possible.
If you have followed everything else in this article, you are probably like 90-95% safe, the suggestions in tier 3 are more for those uber cyber security-minded who want to make their online and crypto usage an impenetrable fortress. Most average folks are most likely fine with the first two tiers.
 Tier 3 Will Supercharge Your Security and Offer Robust Protection from Attacks. Image via Shutterstock
Tier 3 Will Supercharge Your Security and Offer Robust Protection from Attacks. Image via ShutterstockHere are some steps you can take to enhance your security fortification:
- Supercharge your passwords - We have already covered using a password manager, but there is a way you can take this to the next level. Make sure all of your passwords are the highest complexity, and now do something crazy. Delete the last 2-4 characters of your most important passwords that are saved in your password manager (after memorizing them, of course). This way, if someone gets their hands on your password or breaks into your password manager, they won’t be able to use it without knowing the last 2-4 characters that only you know.
This is risky as you run the risk of forgetting yourself. You could even write these 2-4 characters down and keep them offline, effectively separating your passwords. This same technique could be used to separate 1 word from the rest of your recovery phrase, though again, this is quite risky.
- Fortify your Network - This step bolsters the security of your home network, which is something that is commonly overlooked as it is something not understood by the average internet user. Learning how to increase the security of your overall home network is a good step in protecting your assets and online activities.
- Enable WPA2 encryption on your WiFi. If this option isn’t available, use WPA. How-to guides are provided by clicking on the terms in this bullet point. Don’t use WEP as it provides weaker security, the link above explains why.
- WPA2 needs a strong password. Feel free to use your handy password manager again 😉
- Disable WiFi Protected Setup (WPS) as it is less secure. A router with WPS enabled is vulnerable as it was designed as a quick and easy way to help non-techie folks quickly add devices onto the network. Successful attacks on a router’s WPS function will reveal a network password, so it should be disabled.
- Keep your router’s firmware updated regularly.
- Routinely check the router logs for unauthorized activity. Each router is slightly different, but the link should help as a general guide. If you see unauthorized activity, you can end the unauthorized session then change your router password and repeat the steps in this section.
- Create different Service Set Identifiers (SSIDs) on your router. This is your network’s name essentially, and you can create more than one. Consider setting one up for your home devices, one for guests, and one for the computer you dedicate to crypto usage. Each one is isolated from the rest and should have separate, strong passwords.
- Encrypt your hard drive. Encrypting your hard drive will protect all the data on your computer in case it gets stolen or lost. Just be sure the password you use is something you will be able to remember. A password manager may not help much here if you can’t even access your computer in order to launch your password manager.
- Consider using a Tor along with your VPN for added security. A Tor is an open-source privacy network that enables anonymous web browsing. Using this along with a VPN is like a strong one-two combo, supporting truly anonymous and encrypted browsing. Some good VPNs will come with an additional Tor option. My favourite way to use a Tor is simply by using the Brave browser as it comes with a private Tor window option for free.
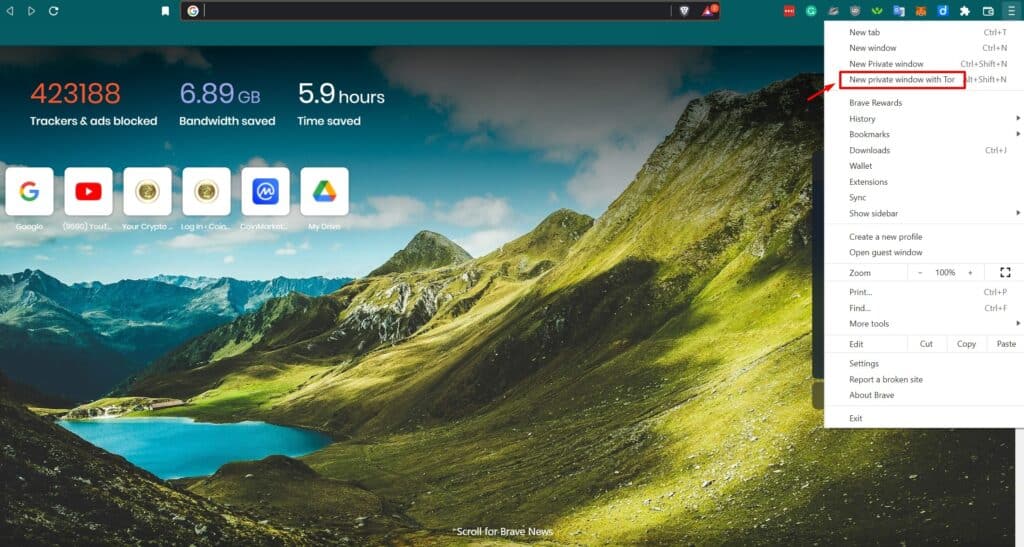 Brave Browser is a Highly Secure Browser that Automatically Blocks Trackers and Ads and Has a Built-in Tor Feature.
Brave Browser is a Highly Secure Browser that Automatically Blocks Trackers and Ads and Has a Built-in Tor Feature.Note that using Tor will slow your internet speeds significantly so this is best only switched on when transacting with your crypto.

Is Cryptocurrency Safe? Closing Thoughts:
Phew, that was a doozy of an article and there was a lot to unpack here. Don’t let this article overwhelm you or feel like you need to implement all of this in one day. Just as Rome wasn’t built in a day, neither does your cyber security fortress have to be.
Feel free to bookmark this article and come back to it each time you are ready to incrementally increase your internet and crypto safety. If you follow even a fraction of what is highlighted in this article, you will be miles ahead of the average crypto user and that much less likely to wander into the pitfalls of crypto.
Because here at the Coin Bureau, we are passionate about crypto education and helping as many people as we can navigate the crypto jungle in the safest possible manner, so please consider sharing this article with any of your friends and family who are into crypto. Together we can spread the word about safe crypto usage which will only help advance and benefit the entire crypto community.
Until next time, safe hodling, cryptonaut.





