There has been extensive attacks that make use of malware and file encryption to extract monetary ransoms. Hackers will lock up important files on the machines of the victims and demand a payment in cryptocurrency.
Now it seems as if hackers are restoring to another attack vector in order to extract their ransom payments. They are making use of Memcached DDoS (Dedicated Denial of Service) attacks on servers.
Unlike a standard DDos attack that would just inundate a server with random packets of data, these packets contained an interesting message. They instructed whoever was reading it to pay 50 Monero in order to stop the attack.
At current market prices, that is about $17,000 that a company would have to cough up in the hope that the attackers would let up.
But what exactly is a memchached DDos attack and are Ransom DDoS attacks common?
What is a Memcached DDoS Attack?
Memcached DDoS attacks have only recently started coming onto the scene and have enabled hackers to launch some of the largest DDoS attacks that have been seen. They are doing this by exploiting poorly configured memcached servers.
As explained in a blog post by Akamai, this poor configuration means that the server will respond to UDP traffic with packets that are much larger than those being sent. Sometimes these are many multiples bigger.
Moreover, given that it is the UDP protocol, the packet's origin IP can easily be spoofed. Hence, the attackers will spoof the IP and make it look like another server is sending the request. The memcached servers will respond to that IP.
The packets being sent are sometimes so large that attacks can actually produce DDoS with a peak of 1.35 terabytes per second. In fact, it was this type of attack that just recently hit Github with some cyber security experts calling it the biggest attack ever.
This is called a reflective DDoS attack which has an "amplification factor". In this case, the multiplied packet size was the amplification factor that brought the servers down.
It is not immediately clear who is behind the attack but there are many security researchers who believe that it could another hacking group from North Korea that is attempting to extort companies and websmasters around the world.
Pay Up, Or we Attack
Ransom DoS (RDoS) attacks are not entirely new. They have been practiced before with some organisations as victims. Initially, they would involve a group of attackers emailing numerous people in an organisation threatening an attack.
They would demand a Bitcoin payment in order to stave off a potential attack. They were also referred to as DDoS-for-Bitcoin (DD4BTC) and although they were intimidating, they were just threats.
Although they were threatening the DDoS, they most often did not have the firepower to actually bring down the servers. Hence, the people in the organisation were more than happy to ignore the majority of these requests.
With the vulnerabilities in the Memcached servers now known, they are being actively exploited. Attackers have the firepower they have been looking for and they are not afraid to use it.
In fact, they are not even threatening.
Pay Up, Or we Don't Stop
In the case of this RDoS, the attackers did not threaten the company with their demands first. They immediately started launching the Memecache attack which must have brought many servers to their knees.
However, in the case of this attack, instead of sending random data, they sent a little message with the packets. Below is the screenshot of the ransom message that came from the attackers.
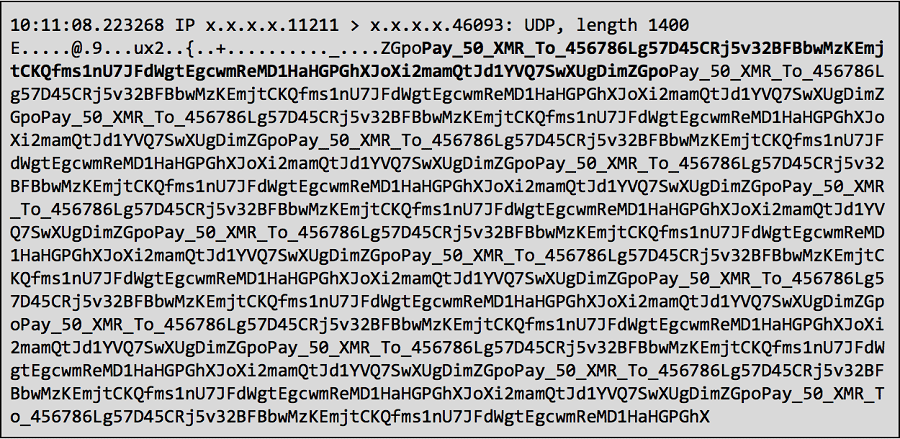
The Ransom Hidding in the Data. Source: Akamai.com
As you can see, the attackers are asking the victims to pay 50 XMR to a particular wallet address. They have no doubt chosen to receive their payment in Monero given that it is one of the most privacy conscious cryptocurrencies around.
This also does not appear to be targeted at only one victim. A French security researcher received the same attack with the samiliar ransom threat in the data packet.
This shows that the attackers may be sending their deformed data packets to a number of different targets and hoping that someone is spooked enough to pay up. Given how secure Monero is, one has no way of knowing how much was being sent to that address.
Paying Won't Help
Unfortunately for those under attack, paying the ransom is almost certainly unlikely to stop it. This is because it will be impossible for the attacker to identify who actually paid the 50 XMR as the payment address used is the same for all the attacks.
This is something that the attackers would most likely know with their goal being to scare the recipient enough to send over the Monero. This could have an adverse effect as the attacker would then see a return on their investment and they could ramp it up further.
What this attack demonstrates is the ability for cyber criminals to adapt faster than authorities and researchers are able to respond. It also shows that run of the mill cyber-attacks are now been re-engineered to include cryptocurrencies.
From malware that run on servers to website miners who hijack browsers to mine Monero, we are likely to see many more vectors open up over the next few months.
Featured Image via Fotolia



