Your on-chain identity is your gateway to digital empowerment in Web3 and DeFi. At the heart of this identity lies a crypto wallet—a tool essential for navigating the decentralized economy. However, creating and managing a wallet isn’t just about having a digital address; it’s about understanding and safeguarding the pair of cryptographic keys that form the backbone of your interactions with blockchain networks.
These public and private keys enable you to send and receive cryptocurrencies, interact with smart contracts, and stake your claim in the decentralized ecosystem. Put simply, your keys are your identity in Web3. Losing or mismanaging them can lead to devastating consequences, including losing your holdings or exposure to scams.
This article is designed to help you grasp the importance of public and private keys and how to use them responsibly. Key management practices are non-negotiable for protecting your digital assets. If you’ve ever felt uncertain about handling your keys, this article is your introduction to the intricacies of crypto wallets and using them securely.
Check out our top picks for the best:
What is a Public Key?
Imagine a bank account system. To receive money, you share your bank account number, allowing others to deposit funds without letting them access or withdraw money from your account. This is similar to how public keys work in blockchain technology.
On a blockchain, the ledger functions similarly to a bank’s book of accounts, tracking every transaction involving wallet addresses. Your wallet address, comparable to a bank account number, is what you share with others to receive cryptocurrency. However, sharing it doesn’t give anyone the authority to access or control the funds in your wallet.
For instance, in the Ethereum network, a wallet address is a 42-character hexadecimal string (e.g., 0xabc123...) derived from a public key. It acts as your identity on the blockchain, allowing others to send you crypto. As a bank ledger logs debit and credits, blockchains record all transactions involving wallet addresses in an immutable, publicly accessible ledger. Tools like blockchain explorers let you view these transactions, ensuring transparency and accountability.
How It Works
A public key is a cryptographic identifier used in blockchain transactions to receive funds and verify transactions. Public keys are derived from private keys through a cryptographic process known as the Elliptic Curve Digital Signature Algorithm (ECDSA), ensuring a mathematical link between the private and public keys while maintaining the confidentiality of the private key.
 This is How a Wallet Address Looks Like | Image via MetaMask
This is How a Wallet Address Looks Like | Image via MetaMaskWallet addresses, in turn, are derived from public keys through an additional hashing process, making them shorter and more user-friendly. While a wallet address is what you share to receive crypto, the public key is its underlying structure, enabling secure interactions on the blockchain. Public keys and wallet addresses create an on-chain system for receiving and managing digital assets without exposing sensitive information.
What is a Private Key?
Continuing with the analogy of a bank account, imagine you need personal identifiers like a PIN, signature, or social security number to authorize transactions. These identifiers are unique to you; anyone who gains access can fully control your account. For this reason, you keep these credentials secret and secure.
Similarly, in the blockchain world, a wallet address (or public key) is controlled by a private key—a long hexadecimal string that acts as the cryptographic "password" to your wallet. This private key provides full access to the funds stored in the wallet and is essential for authorizing transactions. If someone gains access to your private key, they gain complete control over your wallet, making it critical to keep it secure and offline whenever possible. Ethereum uses the ECDSA algorithm to derive the public key from the private key.
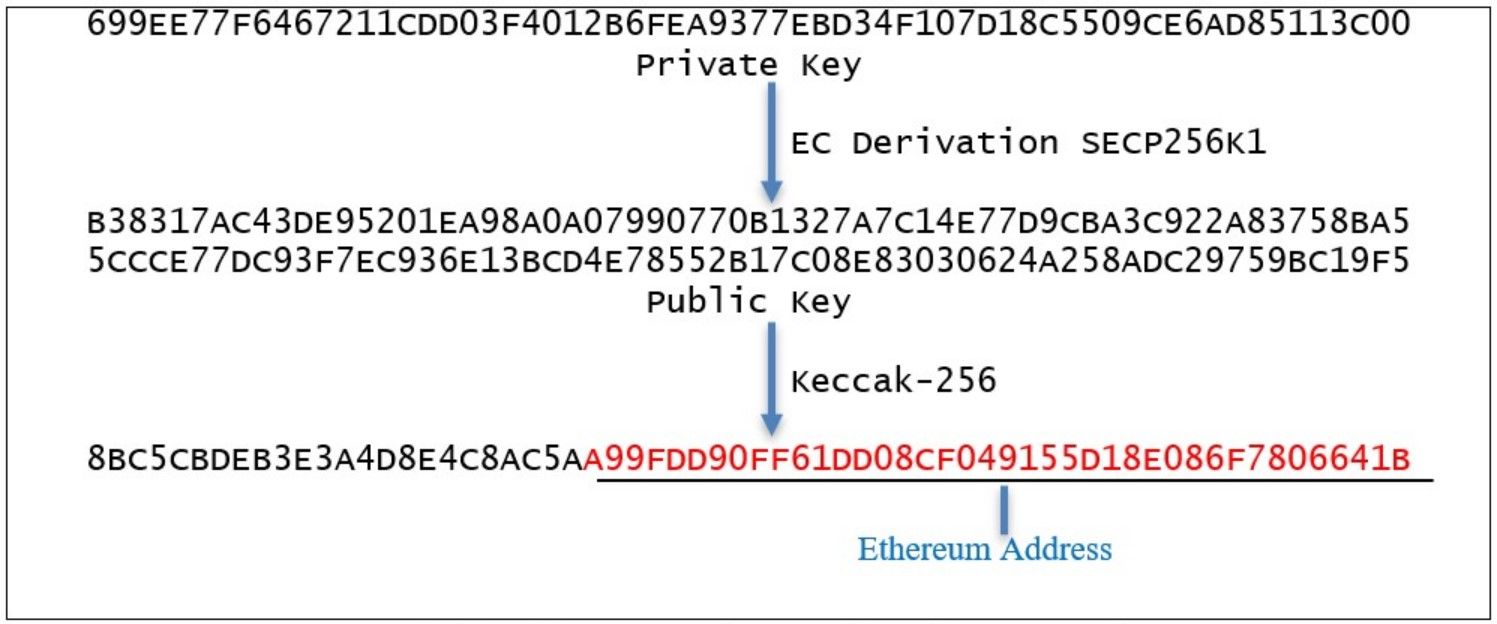 Addresses Are Derived From the Private Key | Image via ise.io
Addresses Are Derived From the Private Key | Image via ise.ioFor this reason, while wallet addresses (public keys) are shared freely to receive funds, private keys remain confidential, safeguarding your digital assets.
How It Works
A private key is a cryptographic code unique to your crypto wallet. It is the foundation of your control over your blockchain assets, allowing you to sign transactions and prove ownership of funds. Just like a PIN secures your bank account, a private key secures your wallet by providing the sole authority to initiate transactions.
When you perform a transaction, the private key encrypts the transaction details in a process known as signing the transaction. This signature verifies that the rightful owner of the wallet initiated the transaction. Notably, anyone can validate the signature using the corresponding public key without revealing the private key itself, ensuring both the authenticity of the transaction and the confidentiality of your credentials.
For example, if you send cryptocurrency to another wallet, the private key generates a unique cryptographic signature for that specific transaction. The blockchain network uses your public key to confirm that the signature matches the transaction and that the wallet owner authorized it. This process highlights private keys' critical role in securing and enabling blockchain transactions.
Key Differences Between Public and Private Keys
Public and private keys work together to secure blockchain transactions but have distinct roles and different properties. Here’s a breakdown of their fundamental differences:
| Aspect | Public Key | Private Key |
|---|---|---|
| Visibility and Sharing | Meant to be shared openly; used to generate wallet addresses. | Must remain confidential; acts as the "master key" to control wallet funds. |
| Purpose | Enables the receipt of funds and verifies transaction legitimacy. | Authorizes transactions by creating digital signatures; encrypts transaction data. |
| Security Implications | Safe to share; poses no direct security risk but must be shared carefully to avoid phishing attacks. | Must be kept secure; exposure leads to unauthorized access and potential loss of funds. |
| Role in Wallet Address Creation | Wallet addresses are derived from public keys through hashing. | Public keys are derived from private keys using cryptographic algorithms like ECDSA. |
| User Interaction | Indirect interaction through wallet addresses used for receiving funds. | Direct interaction is rare; managed through seed phrases or encrypted storage in wallets. |
Visibility and Sharing
- Public Keys: As the name suggests, public keys are meant to be shared openly. They are used to generate wallet addresses, which act as identifiers for receiving cryptocurrency or other blockchain interactions. Sharing your public key or wallet address does not pose a security risk.
- Private Keys: Private keys, on the other hand, must remain confidential. They are the "master key" to your wallet, granting complete control over its funds. Sharing a private key compromises the wallet's security, potentially leading to unauthorized access and loss of funds.
Purpose
- Public Keys: Their primary purpose is to enable the receipt of funds and verify the legitimacy of transactions. Public keys are also used in cryptographic processes to validate digital signatures generated by private keys.
- Private Keys: A private key authorizes transactions by creating a digital signature. It is also used to encrypt transaction data, which can only be verified using the corresponding public key.
Security Implications
- Public Keys: Public keys are safe to share and do not expose your wallet to theft or unauthorized transactions. However, ensuring they are not shared via insecure or suspicious platforms is still important to avoid phishing scams or other indirect attacks.
- Private Keys: Private keys must always be kept secure. If a private key is lost or exposed, the funds in the associated wallet could be permanently lost or stolen, as blockchain transactions are irreversible.
Role in Wallet Address Creation
- Public Keys: Wallet addresses are derived from public keys through a hashing process. This makes wallet addresses shorter and easier to use while mathematically linking them to the public key.
- Private Keys: Public keys are derived directly from private keys using cryptographic algorithms, such as the Elliptic Curve Digital Signature Algorithm (ECDSA). This hierarchical relationship ensures that the private key is the root of all security in the wallet system.
User Interaction
- Public Keys: Users interact with public keys indirectly through wallet addresses, which are shared with others to receive funds or interact with smart contracts.
- Private Keys: Direct interaction with private keys is rare in modern wallets, as most wallets use seed phrases or encrypted storage to manage them securely. However, users are responsible for backing up and safeguarding their private keys or recovery phrases.
Understanding these differences is essential for proper key management and safeguarding your digital assets. Public keys enable secure communication and transactions, while private keys protect access to your funds, making them the cornerstone of blockchain security.
How Crypto Wallets Use Public and Private Keys
Crypto wallets operate on a key pair system, utilizing public and private keys to secure blockchain interactions. These wallets simplify the behind-the-scenes cryptographic processes, enabling users to send and receive cryptocurrencies effortlessly.
Public keys, derived from private keys, allow users to share wallet addresses to receive funds. Meanwhile, private keys are securely stored within the wallet and used to authorize and sign transactions. By abstracting these cryptographic functions, wallets provide an intuitive interface for managing digital assets while ensuring the security of the underlying keys.
Transaction Process
Let’s break down the process of sending a crypto transaction using the MetaMask wallet on the Ethereum network:
- Initiating the Transaction:
- Open your MetaMask wallet and navigate to the “Send” option.
- Enter the recipient’s wallet address (public key) and specify the amount of ETH or tokens you want to send.
- Transaction Details: The wallet calculates gas fees and previews the transaction details, including the total amount to be sent and estimated network fees.
- Authorization and Signing:
- When you confirm the transaction, MetaMask uses the private key stored within the wallet to generate a digital signature.
- This signing process occurs in the background, ensuring the private key is never exposed to the user or transmitted over the network.
- Broadcasting the Transaction: The wallet submits the digitally signed transaction to the Ethereum blockchain for node validation.
- Confirmation: A transaction is considered complete once it is validated and included in a block. You can view the transaction details via blockchain explorers like Etherscan.
This seamless process demonstrates how wallets handle cryptographic complexity, making blockchain interactions accessible to users while securing private keys. For detailed steps on using crypto wallets, read our Guide to Using Metamask.
Hot vs. Cold Wallets
Crypto wallets are broadly categorized into hot wallets and cold wallets, depending on how they store and manage private keys.
| Feature | Hot Wallets | Cold Wallets |
|---|---|---|
| Connection | Connected to the internet | Stored offline and not connected to the internet |
| Use Case | Ideal for frequent transactions and active trading | Best for long-term storage and large holdings |
| Security | More susceptible to hacking and phishing attacks | Highly secure against cyber threats |
| Convenience | Easy to use and accessible anytime, anywhere | Less convenient due to the need for physical access |
| Examples | MetaMask, Trust Wallet, Coinbase Wallet | Ledger Nano X, Trezor Model T, ELLIPAL Titan |
By understanding the distinction between hot and cold wallets, users can choose the solution that best fits their security and usability needs.
Security Best Practices for Private and Public Keys
Proper management of private and public keys is essential for safeguarding your digital assets. Here are key practices to follow:
Protecting Private Keys
- Use Hardware Wallets: To prevent exposure to online threats, store your private keys offline in hardware wallets like Ledger or Trezor.
- Backup Recovery Phrases: Safeguard your wallet’s recovery phrase by storing it in multiple secure locations, such as a fireproof safe or password manager.
- Avoid Digital Storage: Never store private keys or recovery phrases in digital formats like cloud storage, emails, or unsecured files.
- Keep Offline Copies: Write down your recovery phrase on paper or use a secure engraving method to avoid digital vulnerabilities.
- Enable Two-Factor Authentication (2FA): Add 2FA to your wallets and accounts for an extra layer of protection.
Sharing Public Keys Safely
- Verify Addresses: Double-check wallet addresses before sharing or transacting to avoid sending funds to malicious actors.
- Beware of Phishing Attacks: Only share your public key on trusted platforms and avoid clicking on suspicious links.
- Avoid Oversharing: Share your public key only when necessary and with trusted parties, as it may reveal transaction history.
Avoiding Common Mistakes
- Never Share Private Keys: Even accidental sharing of private keys can lead to loss of funds. Treat them with the utmost confidentiality.
- Be Wary of Scams: Ignore requests for private keys, even if they appear to come from reputable sources.
- Update Wallet Software: Regularly update your wallet software to patch vulnerabilities and access improved security features.
- Use Secure Networks: To reduce the risk of interception, avoid accessing wallets or sharing keys over public Wi-Fi networks.
By following these practices, you can minimize the risks of theft or loss and ensure the safety of your cryptocurrency holdings.
Pros and Cons of Using Private and Public Key Wallets
Advantages
Enhanced Security
- Private Keys: Offer complete control over your wallet, ensuring only the owner can authorize transactions.
- Public Keys: Allow secure sharing of wallet addresses without risking funds.
Decentralized Control
- Users maintain full ownership and control of their funds, with no reliance on intermediaries or custodial services.
Transparency
- Public keys enable transactions to be tracked on the blockchain via explorers, providing accountability and visibility.
Interoperability
- Public-private key systems are widely adopted in Web3 and DeFi, ensuring compatibility with most blockchains, wallets, and smart contracts.
Cryptographic Integrity
- Transactions are secured through robust cryptographic algorithms (e.g., ECDSA), making them tamper-proof and resistant to unauthorized access.
Flexibility in Use Cases
- Can be used for a wide range of blockchain interactions, including sending/receiving funds, staking, interacting with smart contracts, and voting in DAOs.
Disadvantages
Complexity for Beginners
- Understanding and managing private and public keys can be overwhelming for new users, increasing the risk of mistakes.
Irreversible Errors
- Losing a private key or recovery phrase results in permanent loss of access to funds. Similarly, transactions sent to the wrong address cannot be reversed.
Security Risks
- Private keys are highly vulnerable to theft if not properly secured (e.g., via phishing, hacking, or physical theft).
- Public keys, while safe to share, can expose transaction history and attract unwanted attention if shared irresponsibly.
Dependency on User Responsibility
- The system relies entirely on users to protect their private keys and recovery phrases, which can be challenging without proper knowledge and tools.
Limited Recovery Options
- Unlike traditional financial systems, no customer support exists to recover lost or stolen funds.
Target for Scams
- Scammers often exploit users' lack of understanding by attempting to trick them into revealing their private keys.
Closing Thoughts
The first interaction with Web3 begins with recognizing the vital role of public and private keys. From the foundational concepts of how these keys work to the differences in their purpose and security implications, this article has explored the essential elements of managing digital assets. We’ve discussed the transaction process, the types of wallets available, and the security best practices that can safeguard your funds. While crypto wallets empower users with unparalleled control and security, they also require careful handling to avoid pitfalls like human error or lost keys.
As blockchain technology evolves, the landscape of wallet management is also advancing. A groundbreaking development in this space is account abstraction, which aims to simplify the wallet experience further. Instead of relying solely on cryptographic keys, account abstraction introduces alternative identifiers like passwords, email addresses, or biometrics to manage accounts and authorize transactions. This innovation reduces the complexities associated with key management, making crypto wallets more accessible to a broader audience, including those unfamiliar with blockchain technology.
By bridging the gap between security and user-friendliness, account abstraction can unlock new levels of adoption for DeFi and Web3. With this simplified approach, participating in the decentralized economy becomes more intuitive, paving the way for a future where managing digital assets is as easy as using traditional online services.




