Hodl, FOMO, market cap, tokenomics, altcoin, airgap, DeFi, GameFi, NFT, TradFi…The list goes on.
The crypto industry is full of weird and wonderful synonyms and made-up words, making this already technical and complex industry even more confusing for newcomers trying to understand the landscape. The terms “cold storage,” “airgap,” “cold wallets,” and “hardware wallets,” all essentially refer to the same thing, referring to an offline secure method for managing cryptocurrency. To help demystify the world of crypto storage, this article is going to explore crypto cold storage and answer the question: How do hardware wallets work?
What is a Hardware Wallet? A Summary:
A hardware wallet is a device that stores your private keys, which is the data that allows users to access their crypto. Hardware wallets ensure these keys are kept offline and away from hackers, viruses, and malware, and can mitigate phishing scam risks, eliminating multiple attack vectors. This feature is a cornerstone of cryptocurrency security, ensuring digital asset protection at its finest. They also ensure that the owner needs to sign transactions on the wallet in order to interact with blockchain networks and DApps, providing a second-factor authentication method as an additional security layer.
Hardware wallets are referred to as "cold storage" as the term "cold" refers to the fact that the wallets have no online connectivity. This is in contrast to software wallets, aka, "hot" wallets, which can be downloaded on devices like phones or computers with internet connectivity. Understanding the differences between hot wallets and cold wallets is crucial for making informed decisions about cryptocurrency storage.
How Do Hardware Wallets Work: A Summary:
Different hardware wallets work differently from a user perspective as some connect via USB cable to a computer, while others may use Bluetooth or QR codes with a mobile device, but the technical workings remain similar across hardware wallets.
When a user makes a transaction, the hardware wallet needs to connect to a computer or mobile, and the hardware wallet verifies and signs the transactions with private keys, which are never exposed to the internet. Only once verified with the hardware wallet will the transaction be broadcasted to the blockchain network.
The Key Features of Hardware Wallets Are:
- Stores private keys offline, adding a layer of protection against hackers, phishing, viruses and malware
- Segregated operating system and firmware manages communication between the device and the blockchain network
- Many devices have anti-tamper features that will destroy the inner components if someone tampers with the device
- Hardware wallets sign transactions and send them back to the network without exposing the private keys
- Many crypto hardware wallets have touchscreens and can display balance and transactional information
- Are capable of supporting different blockchain networks and multiple cryptocurrencies
- Can be backed up and restored via recovery phrases
Hardware Wallets Pros and Cons:
-
Proven secure track record. Hardware wallets provide top level of security and are more secure than software (hot) wallets
-
Can be backed up so funds can be recovered in the event of a lost or stolen device
-
Some can be used to access DApps and Web3 applications directly from within the wallet's app
-
The user retains full control, custody, and responsibility over their digital assets at all times
-
Many are capable of storing thousands of digital assets and NFTs
-
Many are beginner friendly and can be used to easily buy, trade, and sell cryptocurrencies without leaving the wallet’s interface
-
Some can be used as an additional 2FA authenticator when accessing online DApps
-
Can be expensive
-
Full custody can also be a con- if you are irresponsible with your recovery phrase or private keys, you risk losing your funds forever. Nobody can help get your funds back if you mishandle them
-
Some cold wallets are not beginner-friendly and require some technical knowledge
-
Less convenient than mobile wallets
-
Not as suitable for crypto use “on the go” as crypto wallets on a smartphone

What are Hardware Wallets?
A crypto hardware wallet is a type of cold wallet, meaning it is not connected to the internet. Such cold storage solutions are essential for long-term investors looking to safeguard their digital assets from online vulnerabilities. With the two most popular hardware wallet manufacturers, Trezor and Ledger, the hardware wallet is a small device that resembles a USB stick or small device, which can be plugged into your computer or smartphone when you need to make a transaction.
 A Look at the Trezor Model T (Left) and Ledger Nano (Right). Image via Shutterstock
A Look at the Trezor Model T (Left) and Ledger Nano (Right). Image via ShutterstockThe interesting thing about hardware wallets is they are actually quite “dumb” in terms of simplicity. The majority of hardware wallets are incredibly simplistic, single-purpose devices that act as single-purpose computers that only handle your private keys, which are the codes that allow you to access and spend your cryptocurrency. This focus on private key encryption is what makes hardware wallets a reliable choice for crypto enthusiasts and professionals alike.
There are other types of hardware wallets such as the ELLIPAL Titan and NGRAVE, which look more like touchscreen phones and come with corresponding mobile apps that allow you to manage your crypto on your phone instead of having to plug a device into your computer.
 A Look at the NGRAVE ZERO. Image via NGRAVE
A Look at the NGRAVE ZERO. Image via NGRAVEThough wallets like NGRAVE and ELLIPAL look very different to Ledger and Trezor, the basics are still the same, being that the managing of private keys is always done without the devices needing to connect to the internet. For wallets like NGRAVE and ELLIPAL, communication happens between the device and mobile app by scanning QR codes.
The main advantage of using a hardware wallet over software/desktop/mobile wallets is security. Software wallets that are downloaded onto a computing device store your private keys on the device, meaning they can be exposed if a virus or malware finds its way onto the device or if a hacker manages to gain access.
Cold storage wallets don’t have a way for hackers to reach them remotely as they do not have Wi-Fi access. In fact, a hardware wallet can even be safely used with a computer that is riddled with malware as the malicious program cannot spread from the computer to the wallet.
Hardware wallets also have additional security features, such as PIN codes, passwords, recovery phrases, and some come with biometric support and physical buttons that require your confirmation before signing any transaction.
Hardware wallets come with different levels of convenience. In my ELLIPAL review, I mention how I really enjoy that I can access multiple DApps from directly within the wallet app and that it provided me with the convenience that I was used to with a mobile wallet, but with better security.
Though, in general, most would agree that hardware wallets are less convenient than software wallets as you need to have the physical presence of the device to transact, and have it plugged into a computer or phone, crypto transactions require an extra step with hardware wallets, and they aren’t the easiest to use for crypto payments on the go.
So far, I mentioned a few different types of popular hardware wallets. If you are in the market for a hardware wallet, you can check out our article on the Most Secure Hardware Wallets to find the one that is right for you. You can also find Guy's top picks for hardware wallets in the video below:
Why Use a Hardware Wallet?
Hardware wallets are one of the most secure and convenient ways to store and interact with your cryptocurrency. Here at the Coin Bureau, we praise these devices and bang the “not your keys, not your coins” drum all day long. You may have heard that saying before, but let’s quickly cover it.
In 2022, the crypto industry had a bad year, to put it mildly. We watched as centralized platforms like Celsius, Voyager, BlockFi, FTX and others collapsed with no warning, halting the withdraws of all the users who held their crypto on those platforms.
The insolvency of these companies led regular crypto users like you and me to lose access to hundreds of millions of dollars worth of crypto, crypto that users are likely to never get back. All these companies, centralized exchanges, lending platforms, etc. had one thing in common: they were all centralized, and they were all custodial, meaning they held YOUR crypto with THEIR private keys.
Crypto wallets are “self-custodial,” meaning that the user controls their keys themselves, and therefore, their funds. So as the crypto world was burning and centralized platforms were collapsing, anyone who practiced responsible self-storage using cryptocurrency wallets had nothing to worry about as they knew their crypto was safe.
 How Hardware Wallet Users Sleep Knowing Their Funds are Safe. Image via Shutterstock
How Hardware Wallet Users Sleep Knowing Their Funds are Safe. Image via ShutterstockCold storage wallets offer high levels of protection against online threats, centralization risk, censorship risk, and regulatory risk, all while providing users with a secure and easy way to manage their funds with any compatible platform or web interface such as DApps, DeFi protocols, other wallets, and more.
With a hardware wallet, users can easily track their balances and make transactions with any compatible software wallet or web interface. Most hardware wallets can also manage hundreds, if not thousands of cryptocurrencies with the same device, as most hardware wallets support various coins and tokens.
 Manage Your Crypto Securely and Easily. A Look at Trezor Suite.
Manage Your Crypto Securely and Easily. A Look at Trezor Suite.As this article focuses on hardware wallets, I won’t go into detail about how they compare to software wallets, desktop wallets, mobile wallets, or paper wallets, but if you would like to learn about that, we cover that and heaps more in our How to Keep Your Crypto Safe article.
How Do Hardware Wallets Work?
Hardware wallets work by being connected to a computer or smartphone either via a USB cable, Bluetooth, or by the scanning of QR codes. When a user wants to make a crypto transaction, interact with a smart contract, DApp, or send crypto, they will need to verify the transaction on the hardware wallet, which “signs” the transaction. This verification layer means that unauthorized transactions cannot happen.
This offline transaction signing process adds an extra layer of security, distinguishing hardware wallets from their online counterparts.
 Signing a Transaction. Image via Trezor
Signing a Transaction. Image via TrezorA common misconception is that funds are stored in a crypto wallet, which actually is not the case. It is impossible for cryptocurrencies to leave the blockchain. One Bitcoin does not simply jump off the Bitcoin network and enter your wallet, like how we can pull cash from an ATM and put it in our physical wallet.
In actuality, instead of storing your crypto, what is really happening is that the hardware wallet only stores your private keys, which are like the keys to the door on the blockchain where your crypto is stored. Just as your house key opens the door to your house, your private keys open your address on the blockchain where your assets are stored.
When a user connects a hardware wallet to a computer or mobile, this creates a sort of bridge, where unsigned transaction data gets transferred to the wallet. With the wallet, the user then signs or “verifies” the transaction data, which is done with the private key, and broadcasts the now authorized transaction back over the bridge to the blockchain network where it is then processed.
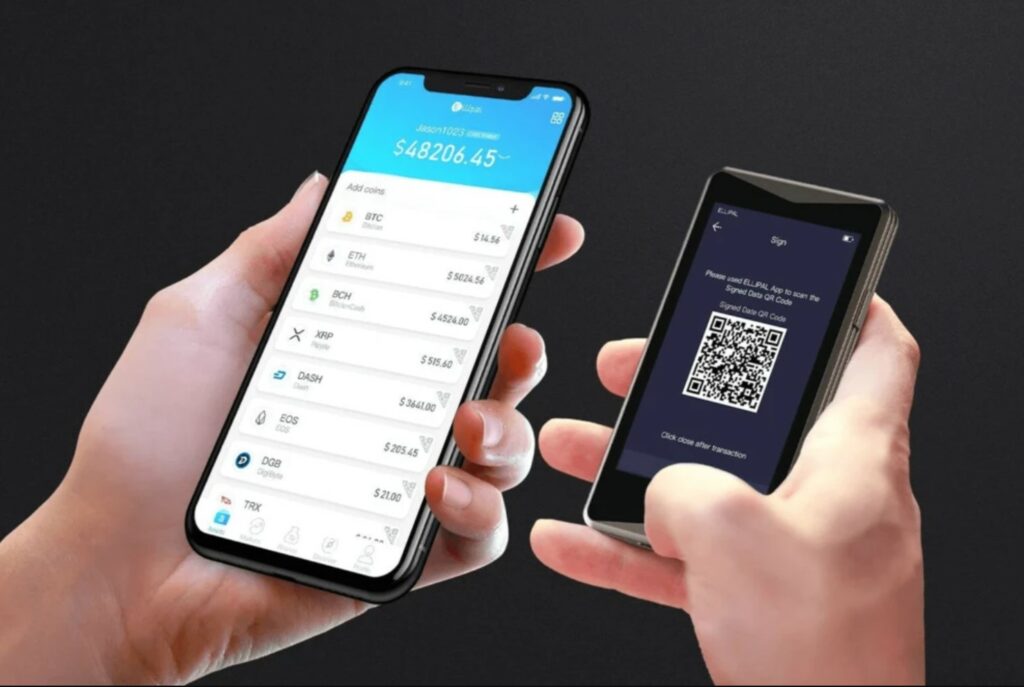 Signing Transactions with The ELLIPAL Titan is Done via QR Code Communication Between a Smartphone and the wallet. Image via ELLIPAL.
Signing Transactions with The ELLIPAL Titan is Done via QR Code Communication Between a Smartphone and the wallet. Image via ELLIPAL.What are Private Keys?
A private key is a code that is used to encrypt and decrypt electronic messages. Every wallet has a unique set of keys, and these keys are required to access cryptographically encrypted data.
Private keys are used in asymmetric encryption systems, where two different keys are used to encrypt and decrypt data.
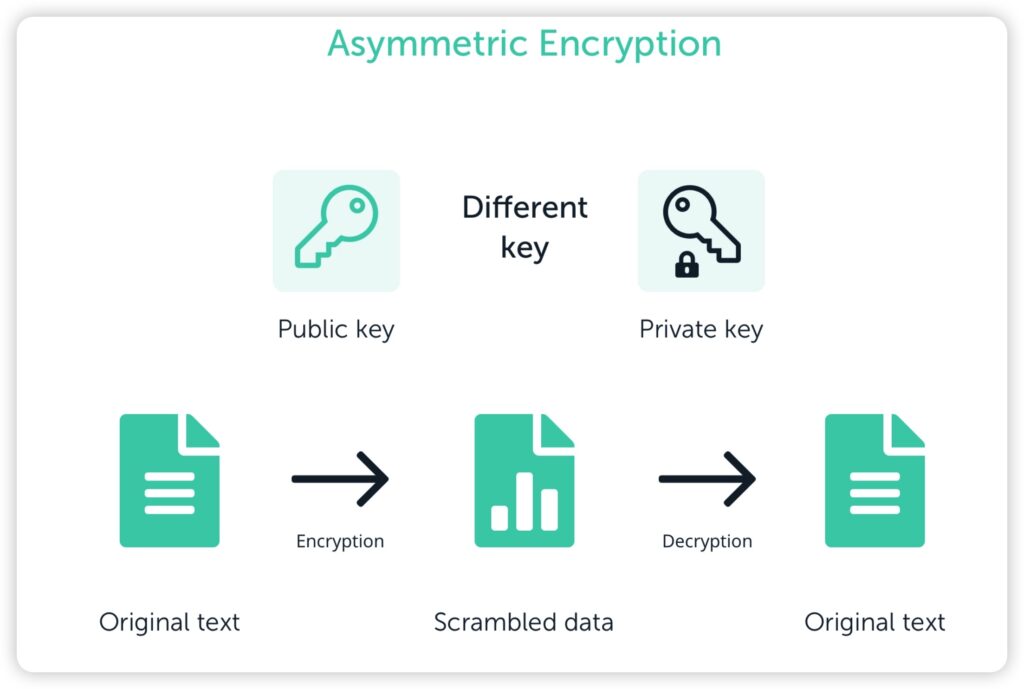 Image via Ledger
Image via LedgerA private key is a string of letters and numbers that provides a user with access to, and management over, their funds. The key is used with an algorithm to encrypt or decrypt data. The long alphanumeric code contains hundreds of digits, and as the name suggests, should be kept private at all times.
A private key should be kept private? Makes sense to me.
This is in contrast to the public key. Each crypto wallet comes with its own unique private and public keys. The public key or public address can be shared with anyone safely and is used to receive cryptocurrency, similar to how you can give someone your email address to receive emails.
The public keys/addresses are also a complex sequence of numbers and letters, usually around 25-36 characters in length. Because the public key is a long alphanumeric string, it isn’t exactly “human-friendly” in terms of memorizing it and sharing it for payments, which is why many people have opted for blockchain domains.
Cryptocurrency public addresses always follow a similar format and vary depending on the network. For example, Ethereum addresses always start with “0x”, Cardano addresses (post Shelly era) start with “addr1”, and Bitcoin addresses can start with the number “3” or “1”, or the letters “bc”, depending on the address format if it is P2PKH, Legacy, Script, SegWit or the newer Bech32 format which covers Native SegWit and Taproot.
Bitcoin address example (Bech32): bc1qar0srrr7xfkvy5l643lydnw9re59gtzzwf5mdq
Ethereum address example: 0x71C7656EC7ab88b098defB751B7401B5f6d8976F
Cardano address example: addr1v9nevxg9wunfckyfkqgypldakvc2rnz34k3mfv99ezjp0lq9t5j5
Solana address example: 7XVgnHgGCUAfsuKvakPgtqEusJTXyUELjwzWjmW7S8mC
Note that Ethereum is not the only address format that begins with 0x, this is a common format for multiple networks.
Blockchain domains are a way of attaching crypto wallet addresses and domains to a name instead of a long string of letters and numbers, so instead of asking someone to make a payment to something like this: 0x71C7656EC7ab88b098defB751B7401B5f6d8976F, you can simply say: "send some Ethereum to bob.eth."
Blockchain domains have a whole host of other benefits as well. You can learn more about them in our Unstoppable Domains article.
Security Tip ⚠️ As public keys are very long, it is common for users to copy and paste them. This is good practice, as it lessens the likelihood of a mistake. Making a mistake and sending crypto to the wrong address could result in a permanent loss of funds. However, be aware that there is malware known as a clipboard hijacker, which has the capability of swapping out a copied and pasted address for the crypto address of a hacker. This has resulted in millions of lost funds, so whenever you copy and paste a crypto address, always double-check it.
Why are Private Keys Important?
As I am sure you have already pieced together, private keys are incredibly important as they provide users with access to their crypto. Anyone who has access to private keys can access the funds stored at that address.
Many in the crypto community opt to take control of their own private keys as that eliminates the need to rely on any third party. Understanding keys is important as they are an integral element with regard to blockchain technology. Without a private key, you would not be able to access your wallet or send transactions, as mentioned, mishandling private keys or letting them fall into the wrong hands can result in permanent loss of funds.
Protecting Private Keys
You might be finding this all a bit complicated and overwhelming and may be feeling like you are not up for the task of taking on the responsibility of storing your own crypto, but don’t worry! Most of what has been covered in this article is happening on the blockchain and is automatically being done by the wallet behind the scenes. Protecting your private keys is incredibly easy!
Seriously, I have friends that I worry about, nearly to the point where I am afraid to lend them a stick of gum as I am afraid they might not know how to breathe and chew gum at the same time, and yet, they are crypto hardware wallet users and manage/protect their own private keys without any issues.
The key thing to know is that you should never share your private key with anyone or store it online or on devices that have access to the internet and are vulnerable to hackers. It is very common for crypto users to store recovery phrases or private keys online in a place like OneDrive or Google Docs. Don’t do this!
A common scam that a lot of people fall for is when they are having a technical problem with a wallet, they will reach out to the support team or community on a site like Reddit, Telegram, or Discord, where they will receive a private message from someone pretending to work for support. The fake customer support scammer will ask for your private keys or recovery phrase, claiming they need that info and then steal the funds.
Again, remember that your private key should remain private and no support team member will ever ask for that information. To drive this point home, here is an image from multiple wallet companies saying they will never ask for private keys or recovery phrases:
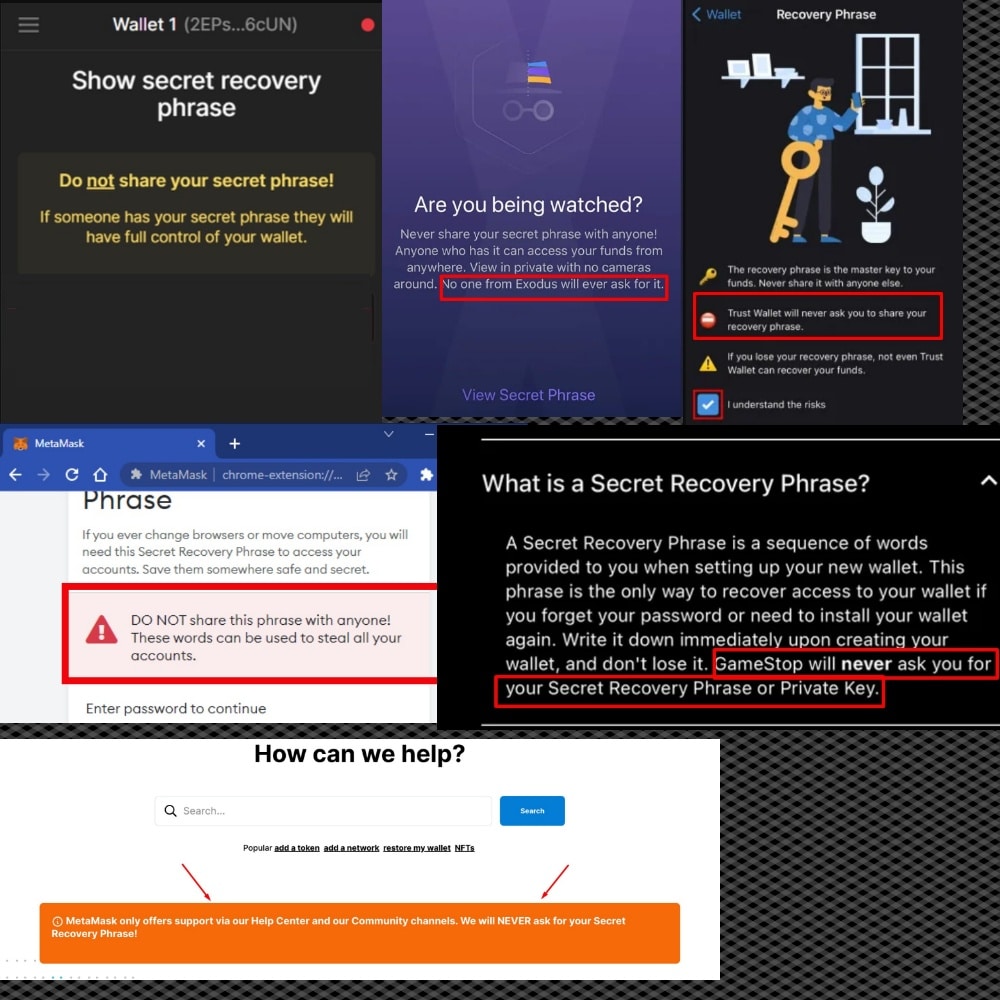 A Collage of Multiple Crypto Companies Saying They Will Never Ask for Your Recovery Phrase. Never Share This With Anyone You Don’t Know And Trust.
A Collage of Multiple Crypto Companies Saying They Will Never Ask for Your Recovery Phrase. Never Share This With Anyone You Don’t Know And Trust.IMPORTANT! Keep That Seed Phrase Safe!!!
Every wallet comes with a recovery phrase, which will be shown to you when you first download or set up a new wallet. Hardware wallets will often come with paper on which to jot this phrase down.
 A Recovery Seed Phrase Card For Writing Down Your Wallet's Recovery Phrase. Image via Shutterstock.
A Recovery Seed Phrase Card For Writing Down Your Wallet's Recovery Phrase. Image via Shutterstock.The Seed Phrase aka Recovery Phrase is a 12-24 word phrase that provides access to a wallet’s private keys. This is what makes it possible to recover crypto funds if you ever lose or break a crypto wallet or the device the wallet is installed on.
There should never be a digital copy of a recovery phrase, not a photo, nothing. It is common for hardware wallets to come with a good old-fashioned piece of paper for users to write this recovery phrase on, which they can then store someplace safe in their home or bank vault. Paper cannot be hacked, which is why this is a safe place to store a recovery phrase.
Of course, paper is quite fragile, which is why many crypto users will carve a recovery phrase onto a metal plate that is fire and waterproof, like these available in the Coin Bureau store:
 Whether You Write the Recovery Phrase on Paper or a More Durable Metal Alternative, Keep it Safe! Image via Merch Store.
Whether You Write the Recovery Phrase on Paper or a More Durable Metal Alternative, Keep it Safe! Image via Merch Store.Writing down this recovery phrase and storing it someplace safe is the #1 most important thing you can do to ensure the safety of your funds. As long as you have these 12 or 24 words written down, you can launch your crypto wallet into the sun, or throw your laptop out the window after rage-quitting a video game, and you will still be able to recover your crypto assets on another computer or hardware wallet that uses the same recovery method, which is nearly all of them.
In addition to keeping private keys secret and storing them someplace secure, it is also a good idea to enable strong passwords on any device you store crypto on and 2FA if possible. There are also many other best practices to follow such as antivirus and malware scanners that I won’t go into here as we cover that in our dedicated Crypto Safety 101 article.
How to Use a Hardware Wallet
Crypto Hardware wallets differ slightly, but generally, the steps are quite similar.
To use a hardware wallet, you can follow these steps:
- Buy a hardware wallet from a reputable manufacturer. Important- Never buy a used hardware wallet or one from an unknown manufacturer as they may have tampered with the device or noted down the seed phrase prior to sale. Many Wallets will come with security features such as holographic tape so users can be confident the wallets were not tampered with during transit.
 Checking Both boxes and Devices for Tamper Proof Stickers. Image via Trezor
Checking Both boxes and Devices for Tamper Proof Stickers. Image via Trezor2. The device will walk you through the setup, backup, and initialization process once it is plugged in and/or turned on for the first time. Most hardware wallets also have handy walk-through guides available on their websites. Set up can typically be done in under 10 minutes.
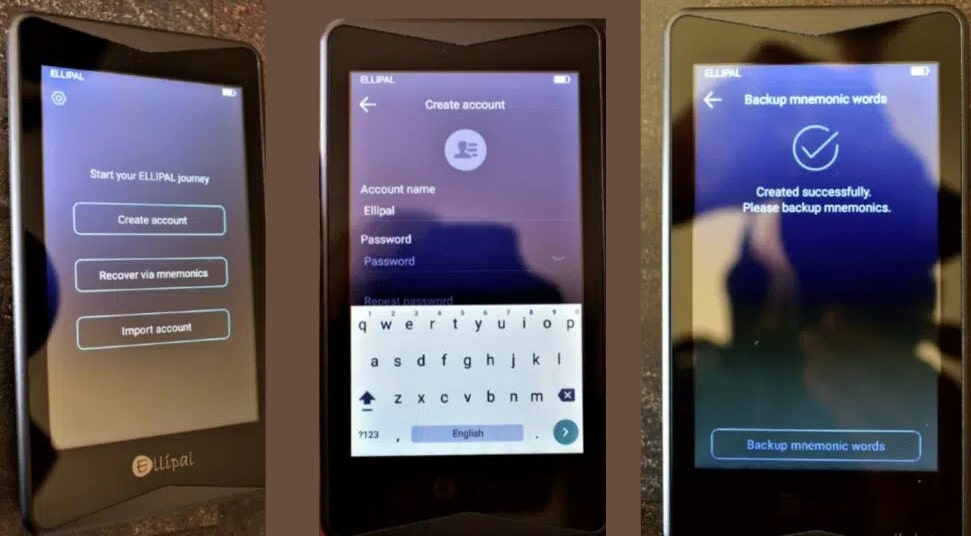 Creating a User Profile and Setting up the ELLIPAL Titan.
Creating a User Profile and Setting up the ELLIPAL Titan.3. Download and install the app or software that is compatible with the device. Be sure to get the install link from a QR code that comes with the wallet, or by downloading the app from the official wallet website. Do Not search for the app in the app store and download it that way as there has been an onslaught of malicious apps nearly identical to the original that steal users' funds.
4. The wallet will show you the recovery phrase upon initialization. Be sure to write down the phrase and set a pin to protect the device.
 Be Sure to Pin or Password Protect Your Wallet. Image via Shutterstock
Be Sure to Pin or Password Protect Your Wallet. Image via Shutterstock5. When you are ready to make a transaction, connect your wallet to your computer or smartphone, unlock it using the pin, and you will find your wallet addresses and balances and be able to transact and access DApps.
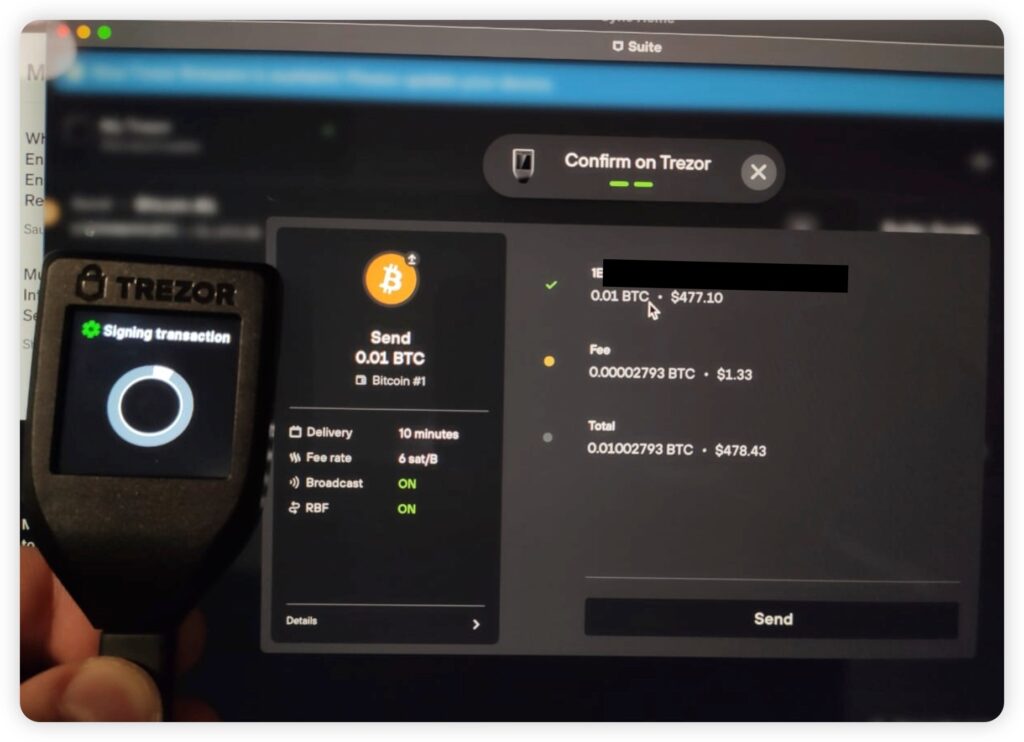 Sending a Transaction with a Trezor Model T. Image via Trezor.Blog
Sending a Transaction with a Trezor Model T. Image via Trezor.Blog6. To receive funds, simply send your receiving address to the sending party or enter the wallet address into your crypto exchange from where you are removing funds. To send funds from your hardware wallet, you will need to enter the receiving address, enter the amount you want to send, then before you can send you will need to verify the transaction on the hardware wallet and confirm the transaction by hitting a button or entering your code.
To show you how easy the process is for setting up a Ledger crypto hardware wallet, Guy put together a fantastic step-by-step video that you can watch here:
He also made a similar Trezor wallet setup video:
Wallets like NGRAVE and ELLIPAL work slightly differently, as these are known as “air-gapped” wallets. With these wallets, instead of plugging them into the computer or mobile phone, the app on the phone communicates with the hardware wallet by scanning QR codes to verify transactions. And that segues me to the next topic.
What Does “Air-Gapped” Mean?
Many people will use the terms cold storage and air-gapped interchangeably and there is no right or wrong, but most experts agree there is a slight difference. We mentioned that wallets like Trezor and Ledger need to be plugged into a computer or phone to use them. The fact they are “plugged in,” in my opinion, means they are not “air-gapped.” The Ledger Nano X can also be connected to a mobile phone via Bluetooth, which raises security concerns for some users, though there have been no known hacks through Bluetooth connectivity to date.
Air-gapped means that the wallets can work without needing to be plugged into or hooked up to anything. So Trezor and Ledger are hardware wallets, and they are classified as cold storage crypto solutions and cold wallets. Wallets like NGRAVE and ELLIPAL can also be described with all those terms, plus being air-gapped.
 Airgapped Wallets Do Not Have Access to any Networks or Connections as an Added Layer of Security. Image via ELLIPAL.
Airgapped Wallets Do Not Have Access to any Networks or Connections as an Added Layer of Security. Image via ELLIPAL.NGRAVE and ELLIPAL have batteries and can operate without being plugged in, instead, they have a camera built in to scan QR codes to transact. There is no consensus as to whether or not one method is better than the other. Many of the most hardcore crypto security experts in the world have no issues trusting Trezor or Ledger, and as an additional point, the software that handles the private keys in Ledger and Trezor are completely separated from where the device is plugged in for use, so there are no known ways that a virus or hacker could ever access a wallet’s private keys as a result of the device being plugged in.
Security Risks
Hardware wallets have proven over the years to be a more secure method of securing crypto assets than leaving them on an exchange, centralized crypto platform, or using software wallets, but that does not mean they are not without their risks.
The biggest risks of using these devices come down to user error. There are many cases of users storing their recovery phrases online in places like their emails, Google Docs, OneDrive, or Apple Cloud storage and having their crypto stolen after hackers gained access to their accounts.
The other common user error is simply losing the recovery phrase, there are countless stories of users who failed to write down the recovery phrase or lost it, and then when their computer, phone, or hardware wallet broke, they had no way to recover their funds. There have also been cases of users falling for phishing attacks and scams that have resulted in the loss of funds.
As for security vulnerabilities, to date, there are no known remote security risks that affect leading hardware wallet manufacturers. As hardware wallets are impervious to hacks, viruses, and malware, there are no known ways to access private keys remotely. A known security weakness comes in the form of a sophisticated hacker having physical access to a hardware wallet, in which they can perform something known as a power glitching attack to gain access to a hardware wallet.
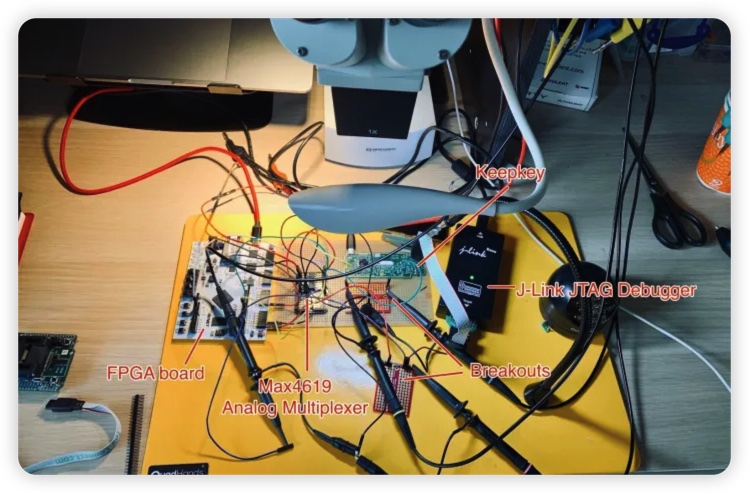 Kraken Security Team Hacking the KeepKey Hardware Wallet. Image via Kraken Blog
Kraken Security Team Hacking the KeepKey Hardware Wallet. Image via Kraken BlogTrezor and Ledger have both improved their security to mitigate power glitching attacks, but it is still a good idea to keep your hardware wallet hidden so it doesn’t fall into the wrong hands.
Different Types of Cryptocurrency Wallets
The main categories of cryptocurrency wallets are:
Hot wallets:
- Mobile Wallets- Exodus, Trust Wallet, etc.
- Desktop Wallets- Daedalus Wallet, Exodus, etc
- Browser Extension Wallets- MetaMask, Fantom, etc.
Cold Wallets:
- Hardware Wallets- Trezor, Ledger, NGRAVE, ELLIPAL, etc
- Paper Wallets
- Key Card Wallets- Arculus
List of the Top Hardware Wallets
- Trezor Model T and Trezor One
- Ledger Nano X and Nano S Plus
- NGRAVE ZERO
- ELLIPAL Titan and Titan Mini
- KeepKey
You can learn more about what makes these our picks for top hardware wallets in our article on the Most Secure Hardware Wallets.
How Do Hardware Wallets Work? Closing Thoughts:
I hope this article helped provide you with a good overview of what hardware wallets are, how they work, and if they are something you should consider for crypto storage. Many veterans in the crypto industry are in agreement that hardware wallets provide the most suitable way to store large amounts of crypto, and are the most ideal way to hodl long-term.
Many crypto users will use a mix of software and hardware wallets, keeping the majority of their funds in a hardware wallet, and only keeping smaller amounts in less secure mobile or browser extension wallets that they need for their daily crypto transactions, DApp access, or using crypto on the go.
So, should you get a hardware wallet?
A hardware wallet can provide peace of mind, knowing your digital assets are secure and well outside of the reach of hackers. Some crypto wallets are very good value for money and perfect for those on a budget such as the Ledger Nano S Plus and Trezor One, both coming in at under $60. These are, in my opinion, pound-for-pound the most solid crypto-security option for those not wanting to spend a fortune on crypto storage.
Even these entry-level wallets provide incredibly high security, the only thing lacking are the extra features available on the more flagship wallets, but the lower price does not mean you are skimping on security. The simplicity of hardware wallet setup and use, combined with their robust security features, makes them an ideal choice for both beginners and seasoned crypto users.
Of course, if you are looking to save even more on a hardware wallet, you can check out our Deals Page, which provides discounts on some of the best wallets in the industry.






