Hardware wallets cut most attack surfaces, but they are not a force field.
This article ranks real risks and shows how they play out: phishing and seed mistakes, supply-chain tampering, physical theft, and “evil maid” access, firmware bugs, host-level malware, fault-injection and side-channel research, and emerging signature-exfil ideas.
You get step-by-step defenses, a quick checklist, an emergency playbook, and a feature matrix to match Ledger, Trezor, Coldcard, and Keystone to your use case. A law-enforcement lens, a fundamentals appendix, and a 2020–2025 incident timeline round it out so you can set up, verify, and maintain self-custody with confidence.
Top Hardware Wallet Threats
Most losses come from fake devices, bad backups, and tricked users, not broken chips. Secure the path around the wallet, not only the wallet itself.
Tampered or cloned units with preset recovery phrases or altered parts steal funds the moment you set them up.
Stolen or unsupervised devices with weak pins or no passphrase let attackers brute and probe at their leisure.
Infected hosts, fake portals, and scam helpers trick users into typing seeds or signing the wrong transaction.
Side channel probes, fault injection, and signature exfil research target very high value wallets yet still rely on weak setup habits.
How Serious Are These Threats, Really?
Hardware wallets are built for safety, but that doesn’t make them immune. The key is understanding which threats matter most and how likely they are to affect everyday users. Compared to exchanges and software wallets, hardware wallets see far fewer compromises, but their protection only works if users set them up correctly and stay cautious.
Let’s look at the hierarchy of risks from most common to least frequent, and how each typically unfolds.
1. Most likely: Phishing and seed mishandling
The vast majority of losses happen outside the device itself. Attackers use fake websites, cloned apps, or impersonation emails to trick users into entering recovery phrases. Sometimes, it’s as simple as a malicious pop-up asking for a firmware update. Once the seed is exposed, the funds are gone.
2. Occasional: Supply chain and counterfeit risks
A hardware wallet bought from an unofficial reseller or pre-owned marketplace can be tampered with before it reaches you. A modified firmware or resealed packaging could insert backdoors or preloaded recovery phrases. Even legitimate supply chains can be exploited through insider manipulation or fake “support” replacements.
3. Moderate: Firmware and connectivity exploits
Although rare, bugs in the device’s firmware or in companion software (such as browser extensions or mobile apps) can expose transaction data or leak key fragments. Devices that rely on Bluetooth or USB connections add another surface of exposure if not properly sandboxed.
4. Rare but severe: Physical and side-channel attacks
These are highly technical attacks involving direct access to the hardware. Examples include fault injection, electromagnetic probing, or power analysis to extract private keys. They’re complex, expensive, and generally targeted at high-value wallets, but they do prove that no system is invincible.
5. Emerging: Social engineering and fake recovery tools
Attackers now use “recovery assistants” or fake customer support numbers that guide victims step by step into revealing their seed. This vector is rising fast because it preys on trust, not code.
6. Long-tail: Backup and recovery vulnerabilities
Even if the wallet itself is secure, poorly stored backups such as plain-text seeds on cloud drives or photo galleries remain one of the weakest links. The best hardware setup collapses if the recovery phrase leaks through digital storage.
When viewed across this spectrum, hardware wallets still outperform every other self-custody option. The key takeaway isn’t that the risks don’t exist, but that most are controllable with proper habits and awareness.
Watch The Coin Bureau's walkthrough of hardware-wallet risks and countermeasures.
Threat #1 — Supply Chain & Counterfeit Devices
 Verify Source Authenticity Before Every Hardware Wallet Purchase. Image via Shutterstock
Verify Source Authenticity Before Every Hardware Wallet Purchase. Image via Shutterstock(Risk: Occasional)
Security starts before the first transaction, that is, at the point of purchase itself. If a hardware wallet has been altered, cloned, or intercepted before reaching you, every safeguard built into it becomes meaningless. That’s why supply chain and counterfeit attacks, while less common, deserve special attention.
What It Is
These attacks exploit the trust between user and device. A pre-compromised hardware wallet might contain modified firmware, hidden components, or pre-generated seed phrases. In many cases, the scam begins with fake online stores, impersonation emails, or “discounted” listings that look completely legitimate.
Some attackers even offer “free warranty replacements” to trick users into sending funds to a compromised wallet. Once that seed or device is exposed, recovery is impossible.
Notable Incidents
- Ledger (2020): After Ledger’s customer data breach, fake “Nano X” devices were mailed to victims. The attackers added a microcontroller to capture seed phrases during setup.
- Trezor Clone Scams (2018–2021): Counterfeit Trezors circulated on eBay and AliExpress, complete with fake holograms and “activation” portals designed to steal recovery phrases.
- KeepKey Resales: Several used units sold on secondary markets were found pre-configured, allowing previous owners to later access wallets remotely.
Each of these episodes revealed the same blind spot: even secure hardware can’t defend against a poisoned supply chain.
How to Protect Yourself
Practical precautions go a long way in closing this gap.
- Buy directly from official or authorized retailers. Avoid auctions, resellers, or “discount” listings on marketplaces.
- Inspect the packaging and device carefully. Check hologram seals, serial numbers, and firmware versions for consistency.
- Run authenticity checks using the manufacturer’s verification or attestation tools, as many wallets now include cryptographic proof of origin.
- Apply the “first-run rule.” Ensure the device generates your recovery seed locally and never trust a wallet that arrives with a pre-printed phrase.
- Watch for fake warranty replacement offers and confirm all returns or exchanges directly with the manufacturer through verified support channels.
- Keep receipts, serial numbers, and proof of purchase for ownership and warranty verification.
- Avoid connecting the wallet before confirming authenticity, both physically and digitally.
- If uncertain, reset the device, reinitialize it, and generate a new seed yourself before transferring any assets.
The good news? These threats are preventable. Buying from trusted channels and following setup rules eliminates nearly every known supply chain vector. In other words, the strongest defense begins before you even press “power on.”
Choosing a wallet? See our hardware wallet picks. If you're looking for one with a sub-$100 price tag, check out our article on the best budget-friendly hardware wallets.
Threat #2 — Physical Theft & Unauthorized Access
 Protect Devices With PINs And Tamper-Evident Storage. Image via Microminderscs.
Protect Devices With PINs And Tamper-Evident Storage. Image via Microminderscs.(Risk: Common)
Digital security gets most of the attention, but physical security often proves just as important. A hardware wallet is, after all, a physical object—one that can be stolen, lost, or accessed when unattended. Once it’s in someone else’s hands, your safety depends entirely on how well you’ve configured it.
What It Is
Physical theft attacks usually occur when a wallet is stolen and protected by a weak or predictable PIN. In public settings, they can also involve “shoulder surfing,” where an attacker observes your PIN entry or recovery phrase setup.
Other cases are subtler: an unlocked wallet left connected to a computer, or a misplaced backup that reveals your seed. None of these involves complex hacking; rather, it was just made easy by opportunity and oversight.
While it’s unlikely a thief can instantly drain funds without knowing your credentials, a determined attacker with access to specialized equipment can attempt brute-force or side-channel extraction—especially if the device lacks proper lockout rules.
Notable Incidents
- Ellipal Cold Wallet Theft (2025): A U.S. investor reportedly lost over 1.2 million XRP when an Ellipal device was compromised through poor isolation and update handling, exposing private keys.
- Ledger Phishing Scams: Hardware wallet phishing letters and QR code scam targeting Ledger users (April & October 2025).
All examples point towards one truth: Even a tamper-resistant device can’t compensate for careless handling.
How to Protect Yourself
Preventing physical compromise requires a mix of strong configuration and disciplined storage:
- Use a strong PIN of at least 8 digits, ideally the maximum your device supports. Avoid simple sequences like “1234” or birth years.
- Enable additional access controls. Use biometrics if available, and turn on lockout timers or automatic wipe settings after repeated failed attempts.
- Activate the BIP39 passphrase (the 25th word) for high-value or “vault” accounts. This ensures that even if the base seed is extracted, funds remain inaccessible without the extra phrase.
- Separate daily-use and vault wallets. Keep smaller funds on one device and long-term holdings on another that stays offline.
- Use tamper-evident storage. When not in use, store the wallet in sealed pouches or tamper bags, ideally inside a locked safe or deposit box.
- Lastly, establish a travel protocol. Carry only a temporary or low-balance wallet when moving. Never unlock or connect the device on shared or unknown computers. Avoid discussing wallet details or seed phrases publicly or during travel.
If stolen, act fast, move your remaining funds to a new wallet using a fresh seed, and treat the old device as permanently compromised. Even the best hardware encryption can’t defend against physical oversight. True security comes from layers of security like strong PINs, optional passphrases, secure storage, and awareness that possession itself can be the biggest vulnerability.
Threat #3 — Physical Tampering / “Evil Maid”
 Inspect Hardware For Signs Of Interference Or Alteration. Image via Trezor Blog
Inspect Hardware For Signs Of Interference Or Alteration. Image via Trezor Blog(Risk: Rare)
When hardware wallets are discussed in security circles, “Evil Maid” attacks sit at the extreme edge of possibility. The name comes from a hypothetical scenario: someone gains unsupervised physical access to your device, say, a hotel staff member, customs officer, or coworker, and tampers with it before returning it undetected.
While these attacks are rare, they’re technically fascinating because they bypass software entirely. Instead of tricking users online, the attacker targets the device’s physical internals.
What It Is
Physical tampering involves opening or probing a hardware wallet to extract secrets directly from its chips or debug ports. Skilled attackers might attempt:
- Memory extraction by connecting probes to flash or EEPROM chips.
- Firmware manipulation to insert backdoors or record seed generation.
- Debugging interface abuse to bypass PIN protection.
- Hardware replacement, swapping the board or USB controller with modified versions.
These attacks require both access and time. Most rely on sophisticated lab tools such as oscilloscopes, JTAG interfaces, or micro-probing stations—resources well beyond the reach of casual thieves. Still, for targeted individuals, the risk can’t be dismissed outright.
Notable Lab Demonstrations
Security researchers have replicated a few controlled examples:
- Ledger Nano S (2018, Wallet.Fail): Demonstrated extraction via fault injection and debug port access, later mitigated through hardware redesign and secure element improvements.
- Trezor One (2020): Researchers showed that unsoldering the MCU could expose the seed, prompting newer models with epoxy potting and enhanced case sealing.
- Coldcard (various): Tested in lab settings against voltage glitching, and has proved highly resistant due to secure elements and tamper-response firmware.
These demonstrations are valuable not because they’re common, but because they drive design evolution across the entire hardware wallet industry.
How to Protect Yourself
While the average user is unlikely to face this kind of threat, a few operational safeguards eliminate most of the residual risk:
- Inspect the device regularly and establish a simple tamper inspection routine. Check for scratches near screws, resealing marks, or loosened casing after travel or extended storage.
- Use tamper-evident seals to detect unauthorized openings. Many users apply serialized holographic seals or UV stickers for quick visual checks.
- Choose wallets with strong physical defenses, such as secure element chips for encrypted key storage and epoxy potting to deter chip removal.
- Prefer models that include mesh shields or conductive coatings designed to erase sensitive data if breached.
- Enable PIN throttling and configure the wallet to enforce delays or automatic wipes after repeated failed attempts.
- Keep your recovery seed off-site. Store recovery phrases in a separate, secure location and never with the device itself.
- Use a BIP39 passphrase to create a hidden vault layer, protecting assets even if the base seed is compromised.
- Limit unattended access. When traveling or staying in shared spaces, store your wallet in a safe or tamper-evident bag, or carry it with you.
Physical tampering sits at the far end of the risk spectrum, rare, specialized, and usually preventable through hardware choice and situational awareness. For most users, the takeaway is simple: pick a wallet with secure hardware, inspect it periodically, and never underestimate the power of basic physical custody.
Threat #4 — Firmware Exploits & Malicious Updates
 Install Updates Only From Verified Official Manufacturer Channels. Image via The New Stack
Install Updates Only From Verified Official Manufacturer Channels. Image via The New Stack(Risk: Occasional)
What It Is
Firmware forms the core of every hardware wallet, the unseen layer responsible for managing private keys, transaction signing, and cryptographic randomness. When tampered with, it can covertly leak keys or weaken the device’s entropy over time.
Such compromises often stem from unofficial firmware downloads, altered installation files, or counterfeit devices mimicking vendor update servers. In rare cases, even official releases have unintentionally introduced entropy flaws or exposed dormant debug functions, underscoring why firmware integrity is the single most critical line of trust in hardware security.
Notable CVEs / Vendor Advisories
- 2018 — Ledger Firmware Vulnerability (Discovered by Saleem Rashid): A 15-year-old researcher uncovered a flaw in the Ledger Nano S firmware that could allow malicious code injection before signature verification. The issue was patched after disclosure and prompted a redesign of Ledger’s secure element communication layer.
- 2021 — Hardware Wallet Authenticity Verification Study (USENIX Security Conference): Academic researchers from Ruhr-Universität Bochum analyzed firmware-signing downgrade paths and reproducibility gaps in multiple hardware wallets. The study led several vendors to introduce stronger attestation protocols and deterministic build verification.
- 2023 — RNG Entropy Weakness in Beta Hardware Builds (Community Disclosure): Security researchers identified a predictable random-number generator (RNG) in an experimental hardware wallet beta, potentially exposing key material in test networks. The issue was fixed before public release, reinforcing the need for reproducible builds and open RNG validation.
How to Protect Yourself
- Update firmware only through official apps, and never from forums or social media links. Always verify version numbers and digital signatures before proceeding.
- Review changelogs carefully and understand what each update changes. Avoid unnecessary upgrades on mission-critical devices until they’re fully vetted.
- Choose wallets that support reproducible builds or transparent firmware verification, enabling you to verify the vendor’s binary against open-source code.
- Enable anti-exfil signing where supported to prevent hidden data leakage, even if the firmware is compromised.
- Test updates on small balances first before deploying them to cold-storage devices that hold significant assets.
Remember that firmware attacks are rare but potentially devastating. Unlike phishing or physical theft, they compromise the trust foundation of the wallet itself. Disciplined update hygiene and verifiable code transparency are your strongest defenses.
Threat #5 — Malware: Phishing, Clipboard Hijacking, MITM
 Double-Check URLs And Never Paste Wallet Addresses Blindly. Image via Shutterstock
Double-Check URLs And Never Paste Wallet Addresses Blindly. Image via Shutterstock(Risk: Common)
Even the most secure hardware wallet can be undermined if the computer it connects to is compromised. Malware attacks don’t target the wallet directly; they go after the bridge between you and it: browsers, USB ports, and clipboard memory. In many cases, the deception happens so smoothly that users never realize something’s wrong until their crypto disappears.
What It Is
This threat category covers a range of attacks that exploit user interaction rather than device weakness:
- Phishing: Fake support sites, cloned wallet portals, and scam emails convincing users to “restore” or “update” their device by entering seed phrases.
- Clipboard hijacking: Malware that replaces copied wallet addresses with the attacker’s address during a transaction.
- Man-in-the-Middle (MITM) attacks: When an infected host system intercepts communication between the wallet and the vendor’s software, it can manipulate transaction data or firmware updates.
- UI spoofing: Malicious browser extensions or fake apps that mimic official wallet interfaces.
These techniques rely on trust—users clicking familiar links, typing seeds into web forms, or assuming their device screen always mirrors what’s on their computer.
Notable Campaigns
- Ledger Phishing Campaign (2021–2022): Following the Ledger customer data breach, attackers sent personalized emails with official-looking domains urging users to “recover their wallets.” Thousands fell for the fake recovery portal.
- Clipboard Malware on Windows: Malware variants like “ClipboardStealer” and “CryptoClipper” silently replaced copied addresses in wallet transactions, redirecting funds mid-transfer.
- Fake MetaMask & Trezor Extensions: Browser add-ons posing as official tools siphoned seed phrases and auto-forwarded credentials to attacker servers.
Each wave of attacks reinforced the same message—malware exploits user trust, not hardware failure.
How to Protect Yourself
Mitigation starts with digital hygiene and verification discipline:
- Always type official URLs yourself or use verified bookmarks. Never click wallet setup links from emails or ads.
- Keep your seed phrase offline. Genuine hardware wallets generate and confirm it only on-device. Any site asking for it is a scam.
- Check recipient addresses directly on your device’s screen. Never rely on copied addresses from your clipboard.
- Send a small test transaction before large transfers. Verify the full address before confirming.
- Secure your host devices with passwords or encryption.
- Keep your operating system and browser fully updated.
- Use trusted antivirus or endpoint protection tools (AV/EDR).
- Avoid browser extensions or apps that request excessive permissions.
- Maintain USB hygiene, connect wallets only to trusted, clean devices.
- Ignore unsolicited messages offering wallet recovery or support on Telegram, Discord, or similar channels
Threat #6 — Fault Injection & Side-Channel Attacks
(Risk: Rare / Advanced)
At the farthest end of the attack spectrum sit fault injection and side-channel exploits. These are techniques that target the physics of a hardware wallet, not its software. These attacks don’t rely on phishing or malware; they use precise timing, voltage, or electromagnetic interference to trick the device into revealing secrets. They’re extraordinarily difficult to execute, yet they represent the frontier of hardware wallet security research.
Power/Clock Glitching & Fault Injection
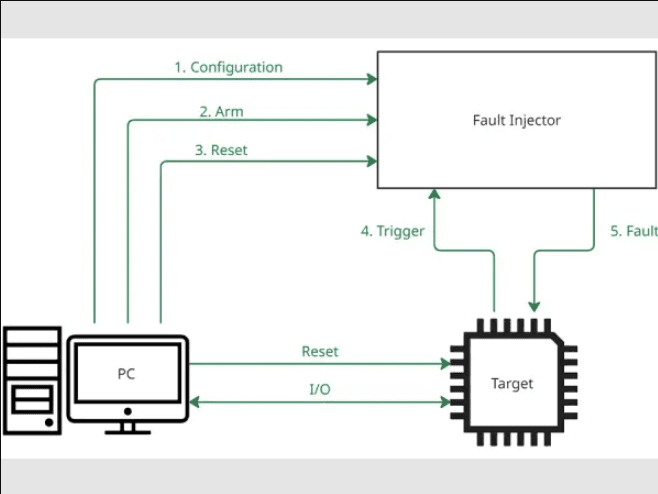 Shield Devices From Physical Probing And Fault Injection. Image via Dekra
Shield Devices From Physical Probing And Fault Injection. Image via DekraIn a fault injection attack, an attacker deliberately disturbs the device’s normal operations by altering its power voltage or clock frequency to induce computational errors. The goal is to force the wallet into skipping security checks or leaking data during cryptographic operations.
Executing such attacks demands lab-grade setups: oscilloscopes, pulse generators, and physical access to the wallet’s circuit board. Under these controlled glitches, researchers have sometimes extracted fragments of recovery seeds or decrypted elements from memory. These are not practical for casual theft, but for nation-state actors or specialized labs, they demonstrate theoretical limits of hardware security.
Side-Channel (EM / Power Analysis)
Side-channel attacks exploit indirect data leaks like fluctuations in power consumption, electromagnetic emissions, or signal timing, which are produced during a wallet’s normal cryptographic operations. By analyzing these patterns with tools such as oscilloscopes, attackers can infer private keys or manipulate random number generators. Well-designed wallets use countermeasures such as electromagnetic shielding, noise generation, and constant-time algorithms to mask these variations. Without such protections, a device’s cryptographic processes can, in theory, be reverse-engineered through repeated monitoring and power profiling.
They happen when the device’s tiny physical signals betray what it’s doing.
While the wallet signs or decrypts, its chip briefly draws different amounts of power, emits tiny electromagnetic pulses, or changes timing. An attacker records many of those traces while feeding known inputs, then runs statistical comparisons between traces and guessed key values to find matches. Repeating this across thousands of operations reveals the secret key or weak RNG outputs without ever touching the private key directly.
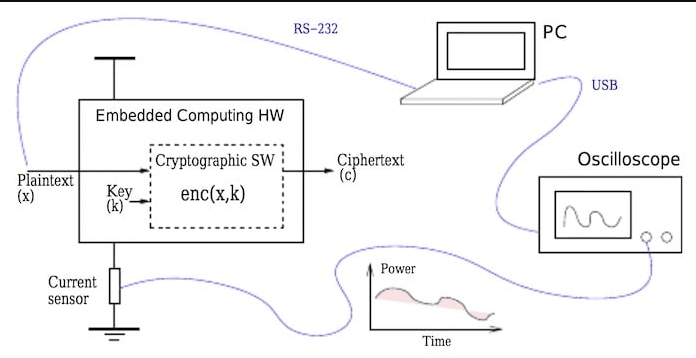 Test Setup For Power Side-Channel Attack With Oscilloscope. Image via All About Circuits
Test Setup For Power Side-Channel Attack With Oscilloscope. Image via All About CircuitsPower analysis is conducted on devices as a targeted diagnostic to measure a device’s tiny power or EM leaks while it runs crypto operations to reveal whether secrets or weak randomness might be escaping. It is used only when there is a suspected device-level issue, before moving large funds, or as part of an audit; the test requires repeated instrumented runs, an oscilloscope or EM probe, and statistical analysis to be meaningful. If nothing suspicious appears, that’s good evidence the device’s shielding and constant-time measures are working; if you do find anomalous traces, treat the device as compromised and move funds using a fresh, securely generated seed.
How to Protect Yourself
Even though these attacks are largely academic, there are practical choices users can make to mitigate exposure:
- Choose devices with certified secure elements that include built-in countermeasures against fault injection and side-channel leakage. Look for EAL5+ or equivalent certifications.
- Check manufacturer documentation for details on epoxy potting, mesh shields, or tamper-response circuitry that triggers wipes on intrusion.
- Keep physical custody at all times. Never leave wallets unattended in hotel rooms, public lockers, or shared offices.
- Enable a BIP39 passphrase to ensure that even if low-level data is extracted, the derived wallet remains inaccessible.
- Rotate hardware over time. For high-value holdings, replace devices every few years as hardware security modules evolve.
While these attacks rarely appear outside research labs, they reinforce a key truth about crypto security: defense is not just software-deep, it’s silicon-deep. For most users, awareness and hardware selection are enough. For those holding millions, these are the fine details that separate theoretical safety from absolute resilience.
Threat #7 — “Dark Skippy,” Nonce-Grinding & Signature Exfiltration
 Validate Firmware Integrity To Prevent Cryptographic Key Leakage. Image via Dark Skippy
Validate Firmware Integrity To Prevent Cryptographic Key Leakage. Image via Dark Skippy(Risk: Theoretical / Emerging)
Attacks like “Dark Skippy” and nonce-grinding exploit the cryptographic layer itself, manipulating the way wallets generate and use randomness when signing transactions. These are not mainstream risks yet, but they sit at the edge of what researchers are watching closely.
What It Is
Every digital signature generated by a hardware wallet includes a nonce, a random number used once to ensure each signature is unique. If that randomness can be influenced or predicted, attackers can start reconstructing private keys—one transaction at a time.
In the so-called “Dark Skippy” scenario, a compromised firmware subtly embeds fragments of secret data (like seed information) inside transaction signatures. Each time the user signs a transaction, a few bits of the secret leak. Over time, an attacker monitoring the blockchain could piece together the entire seed without ever touching the device.
Nonce-grinding is a variant of this approach, where malicious or buggy firmware intentionally chooses weak or biased nonces that leak partial entropy or allow statistical reconstruction of private keys.
While no real-world exploitation has been confirmed publicly, the risk is now well understood in academic research and wallet vendor security testing.
Current Status
These attacks remain research-grade, but they’ve prompted hardware manufacturers to tighten signature-generation standards. Most leading wallets now implement anti-exfil protocols, where each signature is verified to ensure it doesn’t carry unauthorized data. Vendors are also diversifying their True Random Number Generator (TRNG) sources to eliminate deterministic biases.
Independent labs and open-source security communities regularly test firmware for hidden data channels or irregular signing patterns. The conversation has shifted from “if possible” to “how to detect.”
How to Protect Yourself
Because these attacks depend on malicious or manipulated firmware, prevention centers on trust, verification, and diversity:
- Run only verified firmware: Always install updates directly from the manufacturer’s official interface, verifying checksums or signatures before applying them.
- Favor wallets with public firmware builds: Open-source codebases allow researchers to audit for nonce manipulation or signature leaks.
- Enable anti-exfil verification: Some wallets now include optional features to validate signatures or block abnormal signing requests.
- Rotate hardware for high-value operations: Use separate devices for frequent transfers versus long-term holdings; retire older units after major firmware cycles.
- Diverse testing: For institutional or research use, sign test transactions and analyze them for deterministic nonce patterns, a good early detection habit.
While these threats remain largely theoretical, they highlight where wallet security is heading: protecting not just against hackers or thieves, but against subtle cryptographic leakage itself. The frontier is shifting from hardware to math, and awareness is your first line of defense.
To understand this, you must have a better understanding of what blockchain technology is and how it functions.
Quick Security Checklist
 Review Backup, Firmware, And Recovery Steps Before Each Transaction. Image via Shutterstock
Review Backup, Firmware, And Recovery Steps Before Each Transaction. Image via ShutterstockThink of this as your recurring audit sheet, or a simple set of steps to protect your crypto that, if followed, prevent 99% of real-world hardware wallet failures.
Before First Use
- Buy direct: Only purchase from official or authorized vendors; avoid secondhand or marketplace listings.
- Inspect packaging: Make sure holograms, seals, and serials match the manufacturer’s reference photos.
- Generate the seed yourself: Let the device create the recovery phrase on-screen; never accept pre-printed ones.
- Do a test restore: Verify that the seed can successfully recover the same wallet before funding it.
- Set a strong PIN: Use 8+ digits or the device’s maximum supported length.
- Enable a BIP39 passphrase: Add an extra vault layer for high-value holdings.
- Verify firmware: Confirm checksums or digital signatures directly through the companion app.
Monthly Maintenance
- Check firmware versions: Make sure your device runs the latest signed release.
- Inspect the device: Look for any signs of tampering, loose casing, or seal damage.
- Audit your seed storage: Confirm backups remain secure, legible, and off any digital medium.
- Run a phishing drill: Review bookmarked URLs and delete suspicious browser extensions or apps.
Large Transfers
- Always verify on-device: Confirm the full address and amount on the wallet’s display before approving.
- Do a test send: Start with a small transaction to confirm routing before moving large sums.
- Confirm externally: Use a secondary channel, such as a phone call or text, to verify recipient addresses for major transfers.
When used consistently, this checklist reduces hardware wallet risk from a technical challenge to a disciplined routine. Most losses don’t come from hardware failure; rather, they come from skipped steps. Treat these like pre-flight checks, and your crypto stays airborne.
Emergency Response: If You Suspect Compromise
Even with perfect precautions, no setup is completely immune. Whether it’s a lost device, leaked seed, or suspicious activity, a fast and methodical response can make the difference between minor loss and full recovery.
First Hour
Time matters most in the first 60 minutes. Treat every minute as critical.
- If your seed phrase is exposed, immediately generate a new seed on a new, verified device. Then sweep all funds from the old wallet into addresses derived from the new seed. Do not reuse any compromised wallet or recovery phrase.
- If the device is stolen, use your existing seed backup to restore the wallet on a new hardware unit or trusted software interface. Transfer all assets to new addresses right away.
- Disconnect compromised systems. Unplug affected computers or mobile devices from the internet until they’re checked for malware or phishing activity.
Next Steps
Once your funds are safe, document what happened and start the follow-up process.
- Capture evidence: Take screenshots, note dates, and preserve suspicious emails or URLs. These details matter for both vendor support and law enforcement.
- Open a vendor support ticket: Provide serial numbers and a brief incident summary—manufacturers can flag the device or investigate firmware anomalies.
- File a report: If theft or fraud is suspected, submit a police report. Many exchanges and wallet vendors require one to assist with further tracking or recovery.
Future Prevention
After the immediate crisis, focus on closing gaps permanently.
- Never reuse compromised seeds: Treat them as permanently unsafe once exposed or stored digitally.
- Enable a BIP39 passphrase (25th word) for extra separation between wallets and to isolate high-value funds.
- Consider multisig setups for substantial holdings: Multiple key requirements drastically reduce single-point vulnerabilities.
- Review access routines: Keep backups offline, rotate devices over time, and rehearse recovery steps so you’re ready under pressure.
Responding well to compromise is all about how good your procedure is. The faster you isolate, restore, and rebuild, the lower the cost of any breach. Treat it like an emergency drill: fast actions, clear order, no hesitation.
Choosing a Secure Hardware Wallet
 Compare Security Chips, Open-Source Support, And Audit Records. Image via Shutterstock
Compare Security Chips, Open-Source Support, And Audit Records. Image via ShutterstockNot every hardware wallet is built to protect you in the same way. Each model strikes a different balance between transparency, connectivity, and physical resilience. The right choice depends entirely on you and whether you’re storing Bitcoin for a decade, trading DeFi tokens daily, or managing institutional funds.
Security Feature Comparison (Ledger / Trezor / Coldcard / Keystone)
Below is a breakdown of the most relevant technical features across today’s top hardware wallets and what they actually mean for real-world use.
Secure Element (SE):
- Ledger and Coldcard both include certified SE chips (EAL5+ or higher) that store private keys and resist hardware probing.
- Trezor relies on a transparent open-source design instead, without an SE, trading physical resistance for code auditability.
- Keystone integrates an SE with an air-gapped system, adding protection without sacrificing usability.
Open-Source and Reproducible Builds:
- Trezor and Keystone are fully open-source, with verifiable firmware builds.
- Coldcard publishes open firmware but keeps its hardware design proprietary.
- Ledger is closed-source but independently certified and monitored through secure-element audits.
Passphrase, Multisig, and Vault Options:
- All major models support the BIP39 passphrase (25th word) and multisig workflows.
- Coldcard is preferred for advanced multisig and PSBT (Partially Signed Bitcoin Transactions).
- Trezor offers the most user-friendly interface for multisig setup and verification.
Air-Gapping and Connectivity:
- Keystone and Coldcard enable fully air-gapped operation using QR codes or microSD cards with no USB or Bluetooth exposure.
- Ledger and Trezor use USB or Bluetooth, prioritizing integration with wallets like MetaMask or Rabby over isolation.
Firmware Verification and Attestation:
- Ledger uses hardware-level attestation to verify authenticity and firmware integrity.
- Trezor relies on signed open-source builds and public hash verification.
- Coldcard and Keystone both require deterministic firmware signing, blocking unauthorized updates.
Tamper Resistance and Anti-Exfil Protections:
- Coldcard and Ledger employ epoxy potting, mesh shields, and tamper-erase logic.
- Keystone includes magnetic seals and auto-wipe triggers when casing integrity is broken.
- Trezor counters through open hardware verification instead of sealed components.
Emerging Protections:
- Anti-klepto signing to prevent signature exfiltration and nonce bias leaks (now standard on Coldcard and supported in some Trezor firmware).
- MPC and key-share frameworks in enterprise-grade systems (e.g., Safeheron, Fireblocks) split private keys across multiple devices.
- TRNG validation and entropy health checks to ensure randomness quality in signature generation.
Recovery & Lifecycle Management:
- Support for Shamir’s Secret Sharing (Trezor), metal seed backups, firmware lifecycle rotation, and secure device retirement protocols.
- Vendors now include tools to verify device authenticity during firmware updates to prevent supply-chain spoofing.
Match by Use Case
Different wallets shine in different roles. Matching security to your operational context is more effective than chasing specs.
Long-Term Cold Storage / HNWI:
- Coldcard or Keystone with air-gapped signing, metal seed backup, and optional multisig configuration.
- Ideal for high-net-worth holders and self-custody setups that rarely transact.
Active DeFi or Multi-Chain Users:
- Ledger or Trezor for easy dApp connectivity and smooth integration with browser extensions or mobile apps.
- Supports a broad range of tokens and staking features with frequent firmware updates.
Bitcoin-Only Security Maximalists:
- Coldcard remains the top choice for PSBT workflows, advanced scripting, and zero-connectivity isolation.
- Focused purely on Bitcoin, it eliminates altcoin attack surfaces.
Institutional / Treasury Operations:
- Combine hardware wallets with MPC-based custody platforms (e.g., Safeheron, Fireblocks, or Casa Enterprise).
- Enables governance policies, key rotation, and audit logs while maintaining cryptographic isolation.
Travel or Portable Wallets:
- Keystone’s QR-based signing or a slimline Ledger Nano X (with Bluetooth disabled) for quick mobile use.
- Best for traders who need temporary, limited exposure on the move.
Even among top-tier hardware wallets, design priorities differ. Some focus on open-source transparency, others on tamper resistance, air-gap isolation, or smooth dApp connectivity. The table below compares the leading models—Ledger, Trezor, Coldcard, and Keystone—across the features that actually matter.
| Feature | Ledger | Trezor | Coldcard | Keystone |
| Secure Element (EAL5+) | Yes (proprietary) | No | Yes | Yes |
| Open-Source Firmware | No | Fully open | Partially open | Fully open |
| Air-Gapped Operation | No | No | Yes (QR / microSD) | Yes (QR only) |
| Connectivity | USB / Bluetooth | USB / WebUSB | microSD / USB (optional) | QR / mobile app |
| BIP39 Passphrase (25th Word) | Supported | Supported | Supported | Supported |
| Multisig Support (PSBT) | Basic | User-friendly | Advanced | Supported |
| Anti-Exfil / Anti-Klepto Signing | Partial (newer firmware) | Supported | Built-in | Supported |
| Tamper Resistance (Epoxy / Mesh) | Yes | No | Yes | Magnetic seal / auto-wipe |
| Firmware Verification / Attestation | Secure Boot + Attestation | Signed Hash Check | Deterministic Builds | Signed QR Validation |
| TRNG / Entropy Quality | Hardware RNG | Software RNG | TRNG + Entropy Check | TRNG |
| Supported Assets | 5,500+ | 2,000+ | Bitcoin-only | 5,000+ |
| Interface UX | App-based, polished | Simple desktop | Command-line or PSBT workflow | Mobile + QR |
| Best For | Active DeFi traders | General users | Bitcoin maximalists | Air-gapped or travel users |
Our Short Picks by Profile
| User Profile | Recommended Wallet(s) | Why It Fits |
| Long-term Cold Storage / HNWI | Coldcard, Keystone | Air-gapped, tamper-resistant, ideal for vault-level storage. |
| Active DeFi / Multichain User | Ledger, Trezor | Wide asset support, clean interface, strong app integrations. |
| Bitcoin-Only Maximalist | Coldcard | Designed for Bitcoin security, PSBT workflows, minimal attack surface. |
| Institutional / Treasury Ops | Ledger Enterprise, Safeheron, Casa | MPC or multisig governance, policy control, audit logging. |
| Mobile / Travel Setup | Keystone, Ledger Nano X | Lightweight, QR or Bluetooth signing, easy verification on the go. |
There’s no universal “best” wallet; choose only one that fits your risk profile and workflow.
- For transparency, choose Trezor or Keystone.
- For tamper-proof, enterprise-grade protection, Ledger or Coldcard.
- For total isolation and long-term custody, Coldcard and Keystone are the standout options.
The Bottom Line
There is no “perfect” wallet, but only the one aligned to your reality.
If you prioritize transparency, choose open-source. If physical tamper-proofing matters, go for a secure-element model. If you need absolute isolation, select an air-gapped design.
Hardware wallets now operate like a spectrum: from convenience to sovereignty. The right pick is the one that keeps you secure without breaking your own workflow.
Check out our picks for the top 10 crypto hardware wallets.
How Criminals Exploit These Weaknesses (Law-Enforcement Lens)
 Trace Attack Patterns Using Seized Devices And On-Chain Data. Image via Shutterstock
Trace Attack Patterns Using Seized Devices And On-Chain Data. Image via ShutterstockWhile hardware wallets were designed to protect legitimate users, the same properties (self-custody, offline operation, and privacy) that make them secure can also complicate criminal investigations. From an enforcement standpoint, these tools present unique challenges around tracing, recovery, and accountability.
Seed Sharing & Unrecorded Transfers
Hardware wallets make it easy to move digital assets between individuals without a centralized record. In criminal networks, this feature can be misused to bypass traceable exchange transactions.
- Seed sharing allows multiple individuals to access and transfer funds using the same recovery phrase. This practice effectively decentralizes control, making attribution difficult.
- Unrecorded physical transfers, for instance, passing a wallet device or a metal seed backup during an in-person meeting, leave no blockchain trail until funds are later moved.
- Cold-wallet shuffling through air-gapped setups can create long latency periods between illicit acquisition and on-chain movement, complicating asset tracing timelines.
These techniques exploit the strength of self-custody itself: no intermediaries, no logs, and no built-in audit trail.
Asset Forfeiture Evasion Scenarios
Hardware wallets also pose difficulties during legal seizures or forfeitures. Once investigators obtain a device, access depends entirely on whether the PIN or passphrase is known. Without those, brute-forcing is often impractical.
Common evasion tactics include:
- Passphrase partitioning: Criminals split holdings between hidden “vault” accounts using the BIP39 25th word, ensuring only partial wallets are visible.
- Decoy wallets: Some devices can generate multiple accounts from the same seed, allowing a user to reveal only small balances under coercion.
- Multisig or MPC splitting: Distributing keys among trusted associates across jurisdictions prevents unilateral recovery or freezing by authorities.
- Immediate sweeping: Funds can be relocated within seconds after seizure notice, especially if the suspect retains partial key access.
These methods don’t make the wallets inherently criminal—they simply expose gaps in existing asset seizure frameworks that were built for custodial systems.
Investigative Challenges & Policy Notes
For law enforcement and forensic specialists, the technical resilience of hardware wallets shifts focus from breaking devices to breaking context. The main hurdles include:
- No legal backdoor: Most hardware wallets cannot be reset or decrypted without user credentials; manufacturers rarely store any key data.
- Encrypted firmware and secure elements: These block chip-level forensics, leaving limited physical extraction routes.
- Air-gapped and QR-only devices: Fully offline models like Coldcard or Keystone can remain isolated indefinitely, cutting off digital forensics entirely.
- Cross-border enforcement: When seeds or devices are stored in separate jurisdictions, mutual legal assistance processes are slow, often outpaced by fund movement.
- From a policy standpoint, regulators are now focusing on recovery compliance rather than device access. Some proposals under discussion include:
- Mandating vendor reporting when firmware tampering or stolen-device access attempts are detected.
- Requiring forensic cooperation protocols—secure channels where manufacturers can assist law enforcement in verifying firmware authenticity or transaction metadata without compromising user privacy.
- Exploring self-custody registries for high-value assets (voluntary or institutional) to improve post-seizure coordination.
The takeaway is that hardware wallets don’t create crime, but they expose the limits of enforcement in a world built for centralized control. Their legitimate privacy benefits far outweigh misuse, but the investigative model around them still needs to evolve.
Take a look at the best Bitcoin multisignature wallets to hold BTC with maximum security.
Hardware Wallets vs. Alternatives
 Evaluate Custody Control, Attack Surface, And Long-Term Resilience. Image via Shutterstock
Evaluate Custody Control, Attack Surface, And Long-Term Resilience. Image via ShutterstockThe rise of hardware wallets reshaped crypto custody, but they aren’t the only option. Each custody model, like software, exchange, or hybrid, sits somewhere on the spectrum between control and convenience. Understanding the differences helps users make choices that align with their operational and security needs.
Hardware vs. Software Wallets
Software wallets, or “hot wallets,” live on internet-connected devices. They’re fast, convenient, and ideal for small, frequent transactions, but they’re permanently exposed to online threats like malware, phishing, and clipboard hijacking.
Hardware wallets, by contrast, keep private keys sealed in offline environments. Even if your computer or phone is compromised, the attacker cannot access the key directly. The trade-off is usability: signing transactions through a separate device adds friction, and firmware must be managed carefully to prevent vulnerabilities.
In practice, the line between the two is narrowing. Some modern software wallets now integrate hardware signing modules or companion apps that mimic air-gap principles, blurring distinctions for mid-tier users. Still, for long-term security, hardware isolation remains unmatched.
Check out our top picks for mobile crypto wallets.
Hardware vs. Exchange Custody
Exchange custody offers simplicity, no devices, no backups, no seed phrases. But it comes with the oldest risk in crypto: counterparty failure. History shows repeated examples where user balances vanished with the exchange, be it through hacks, insolvency, or regulatory seizure.
Hardware wallets remove that risk entirely by putting users in control of their keys. The cost of that control is responsibility: the user becomes their own bank, accountable for seed management, device upkeep, and recovery discipline.
For traders or institutions using exchanges daily, hybrid setups, where assets are split between a hardware cold wallet and an exchange. Hot wallets offer the best of both worlds.
It is very important to know the difference between what a wallet can do and what an exchange does before assigning roles to them.
Multisig & Additional Layers
For higher security or shared control, multisignature (multisig) setups add another layer between compromise and catastrophe. In a 2-of-3 multisig scheme, for example, at least two separate devices or people must authorize any transfer. This structure prevents single-device failure and mitigates theft or coercion risk.
Institutional users increasingly pair hardware wallets with multi-party computation (MPC) frameworks. MPC replaces traditional multisig with distributed key shares that never exist in one place, allowing auditability without exposing secrets. MPC wallets like the Bitget Wallet, for instance, allow multiple parties to jointly compute a function over their inputs without revealing those inputs to each other.
For individuals, adding a BIP39 passphrase (the 25th word) or air-gapped signing via QR codes achieves similar layered protection without complex coordination.
Bottom line:
Hardware wallets remain the strongest single layer of self-custody. But real resilience comes from combining them with operational layers—multisig, device rotation, and proper cold-storage hygiene. Security is what you buy and maintain.
Fundamentals
 Understand Core Principles Of Security of Hardware Wallets And Cold Storage. Image via Shutterstock
Understand Core Principles Of Security of Hardware Wallets And Cold Storage. Image via ShutterstockThis appendix clarifies the core ideas that underpin modern wallet security. These concepts help decode vendor claims and guide better decision-making when comparing devices or architectures.
Cold vs. Hot Storage
The simplest distinction in crypto security comes down to network exposure.
- Hot storage refers to wallets connected to the internet—like exchange wallets, browser extensions, or mobile apps. They offer convenience but are constantly vulnerable to phishing, malware, and API exploits.
- Cold storage keeps private keys entirely offline. Hardware wallets, paper backups, or air-gapped systems fall under this category. They dramatically reduce attack surfaces but require more disciplined management.
In short, hot wallets are for speed; cold wallets are for safety. The most secure setups use both—hot for active trading, cold for reserves.
BIP39 & Cross-Brand Recovery
BIP39 (Bitcoin Improvement Proposal 39) standardized how recovery phrases are generated and interpreted. It defines the 12- to 24-word mnemonic seed system most wallets now use. Because it’s an open standard, users can restore the same seed across multiple wallet brands—Ledger, Trezor, Coldcard, Keystone, and others—without losing access to funds.
This interoperability is critical for long-term security: even if a company shuts down, your BIP39 seed remains valid anywhere.
While the base BIP39 standard is universal, additional features like the BIP39 passphrase or proprietary derivation paths may differ across wallets, so always test recovery on a secondary device before storing large amounts.
Secure Element vs. Open MCU
At the hardware level, wallet designs split into two camps:
- Secure Element (SE) devices like Ledger or Coldcard store private keys inside dedicated, tamper-resistant chips certified to EAL5+ standards. These resist physical probing, side-channel attacks, and fault injections.
- Open MCU devices—like Trezor—eschew SEs for full open-source transparency, allowing anyone to inspect firmware and hardware design. The security model shifts from “trust the chip” to “verify the code.”
Neither model is objectively superior; they reflect different philosophies. SEs emphasize physical resilience, while open MCUs prioritize auditability and community trust. The best choice depends on your risk tolerance and your view of supply-chain trust.
Check out these top hardware wallet alternatives for Trezor
Anti-Exfil & Reproducible Builds (Why They Matter)
A subtle but growing risk is signature exfiltration. This is nothing but the leaking of private data through manipulated signatures or firmware backdoors. Anti-exfil protocols prevent this by validating every signature to ensure it contains no hidden payloads or biased nonces. Devices like Coldcard and Trezor have integrated these protections after extensive research.
Reproducible builds ensure that the compiled firmware installed on your device matches the published source code exactly. This makes hidden changes—malware, telemetry, or altered randomness—detectable by anyone who rebuilds the firmware from source.
Together, these features push hardware wallet security toward verifiable trust: not “trust us,” but “trust the math.”
Timeline: Major Hardware Wallet Incidents (2020–2025)
 Chart Key Breaches To Learn From Industry Security Failures. Image via Kaspersky
Chart Key Breaches To Learn From Industry Security Failures. Image via KasperskyBelow is a chronological summary of notable hardware wallet vulnerabilities, exploits, and disclosure events from the past five years. Each entry includes the affected model, nature of the issue, its impact, and the remediation status.
June 2020 – Ledger Data Breach (User Info Leak)
Model: Ledger Nano S / X (backend incident)
- Bug/Attack: Customer database compromise via a third-party e-commerce plugin.
- Impact: Over 270,000 users’ personal details (names, addresses, emails) leaked, no wallet keys exposed.
- Fix Status: Security systems rebuilt; Ledger Live backend isolated. Highlighted the importance of data separation between hardware and CRM systems.
January 2021 – Trezor Model T “Evil Maid” Attack Demonstration
Model: Trezor Model T
- Bug/Attack: Physical access exploit using firmware modification and key extraction through debugging interfaces.
- Impact: Required device possession; no remote vulnerability. Confirmed risk of unsealed devices.
- Fix Status: Firmware and bootloader updates restricted debug access; users advised to inspect seals and buy only from official channels.
May 2021 – Coldcard Mk3 Side-Channel Research
Model: Coldcard Mk3
- Bug/Attack: Electromagnetic side-channel leakage allowing partial key recovery in lab conditions.
- Impact: No real-world exploitation; required specialized lab gear and repeated probes.
- Fix Status: Mitigation included additional shielding and randomization in Mk4 hardware design.
July 2022 – Keystone QR Parsing Bug
Model: Keystone Essential / Pro
- Bug/Attack: Malformed QR transaction parsing could lead to UI freeze and partial denial-of-service during signing.
- Impact: No key leakage, but affected transaction reliability.
- Fix Status: Patched in firmware v1.5.3; additional input validation introduced.
April 2023 – Supply Chain Clone Scam
Model: Multiple (Ledger/Trezor fakes)
- Bug/Attack: Counterfeit hardware with modified microcontrollers shipped via unauthorized Amazon and eBay listings.
- Impact: Devices captured seed phrases on setup, sending them to attacker-controlled servers.
- Fix Status: Vendors launched serial-check verification pages and public advisories; consumer awareness campaigns intensified.
December 14th, 2023 – Ledger ConnectKit JavaScript Exploit
Model: Ledger ConnectKit / Live Plugin
- Bug/Attack: Malicious script injection on front-end integration affecting dApp connectors.
- Impact: Some users were tricked into signing malicious transactions via spoofed pop-ups.
- Fix Status: Issue patched; vendor implemented stronger signature verification and runtime integrity checks.
March 2025 – Trezor Firmware Reproducibility Update
Model: Trezor Model T / One
- Bug/Attack: Not an exploit, but a milestone fix addressing reproducibility gaps that previously hindered firmware verification.
- Impact: Strengthened user trust and transparency by aligning binary and source verification.
- Fix Status: Completed rollout in firmware v2.7; reproducible builds are publicly verifiable.
Ongoing – Research into “Dark Skippy” Signature Exfil (2025)
Model: Multi-vendor (theoretical vector)
- Bug/Attack: Experimental method embedding partial seed info in nonce values during signing.
- Impact: No confirmed real-world exploit; observed in controlled lab testing.
- Fix Status: Active research; vendors are incorporating anti-exfil safeguards by default.
Summary
From data breaches to side-channel research, the 2020–2025 period proved that no security model is immune to scrutiny. Yet, nearly every major incident led to tangible design or firmware improvements—proof that responsible disclosure and transparency have raised the bar across the entire hardware wallet ecosystem.
Bottom Line
Hardware wallets remain the most resilient way to safeguard digital assets, but their strength depends on how they’re used. Security is built into the discipline behind it. Most real-world losses trace back not to cryptographic flaws, but to human shortcuts and unverified assumptions.
Every firmware update, transaction, and purchase is a trust decision. The closer you move toward independently verifying those choices, the closer you come to true self-sovereignty. It can be through reproducible builds, firmware attestation, multisig protection, or secure custody practices.




