Last year seemed like the year for Ransomware. We saw the proliferation of Wannacry, Bad Rabbit and Petya to name a few. These attacks paralysed computers across the board from businesses to hospitals.
Now, it seems as if the ransomware scourge is still alive and strong in 2018.
A new type of Ransomware called "GandCrab" is making the rounds and inflicting harm. This strain, which is of Russian origin is also interesting in the sense that it is one of the few "ransomware as a service" types.
Another interesting thing about GandCrab is that it uses the DASH cryptocurrency instead of Bitcoin. This is probably because of the difficulty that comes with tracking these payments.
Let's take a deeper look into the latest threat and what you can do to avoid it.
What is GandCrab?
GandCrab is Ransomware that is spread through two exploit kits, namely RIG EK and GrandSoft EK. It was first discovered earlier this year on the 26th of January. Below is the tweet by the researcher in question.
The Ransomware has since gained much more attention in the cyber security circles and has had more research done on it. One of these firms was LMNTRIX which is based in Australia. They also delved into the darkweb forums to determine how the ransomware is distributed.
This operates as one of the few "ransomware as a service" attacks. Essentially, the attackers will operate on an affiliate structure where the developers will get a percentage of the cut from the affiliates. The developers of the ransomware offer unlimited fixes and tech support for the code.
They also offer special larger partners the opportunity to get a better cut from the typical 60:40 to the a more lucrative 70:30. Such is the nature of this criminal offer that they have even released a youtube video that takes the partners through setting the ransomware up.
There are few restrictions on where the users can operate however they are not allowed to target citizens of countries in the former Soviet Union. This is most likely as a result of the opertators and the servers being located in these countries.
How Does it Operate?
The GandCrab ransomware uses the well-known Rig and Grandsoft exploit kits. These have been known to deliver Malware in the past through compromised websites. They have only once being used before for a Malware payload.
It has also recently being reported by MalwareBytes Labs that the GandCrab payload is also being distributed through EITest and Necurs mail spam. The latter will request that the user download a pdf invoice for their attention.
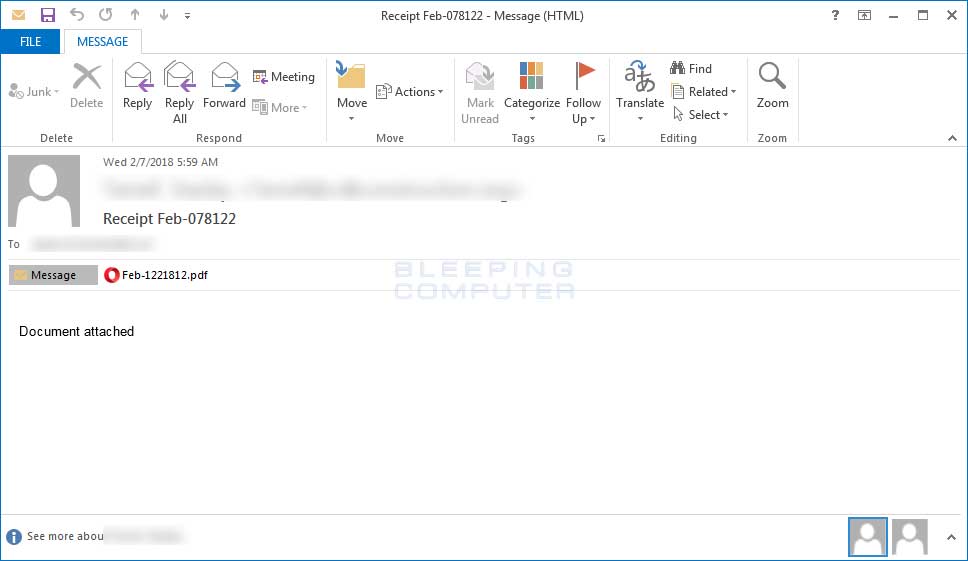
Email with Malicious pdf. Source: bleepingcomputer.com
The moment that the user downloads the pdf, they will be required to complete a captcha in the pdf file. Once that is done, it will create a malicious word file that will require the user to activate macros. If the user does this, it will trigger a macro that will execute a powershell script.
This will then launch the GandCrab ransomware and start connecting to the command and control servers (which use .bit domains). It will encrypt the users files and they will be given an .onion url to which they can access the ransom page. Below is the page in question which is asking for 1.5 DASH.
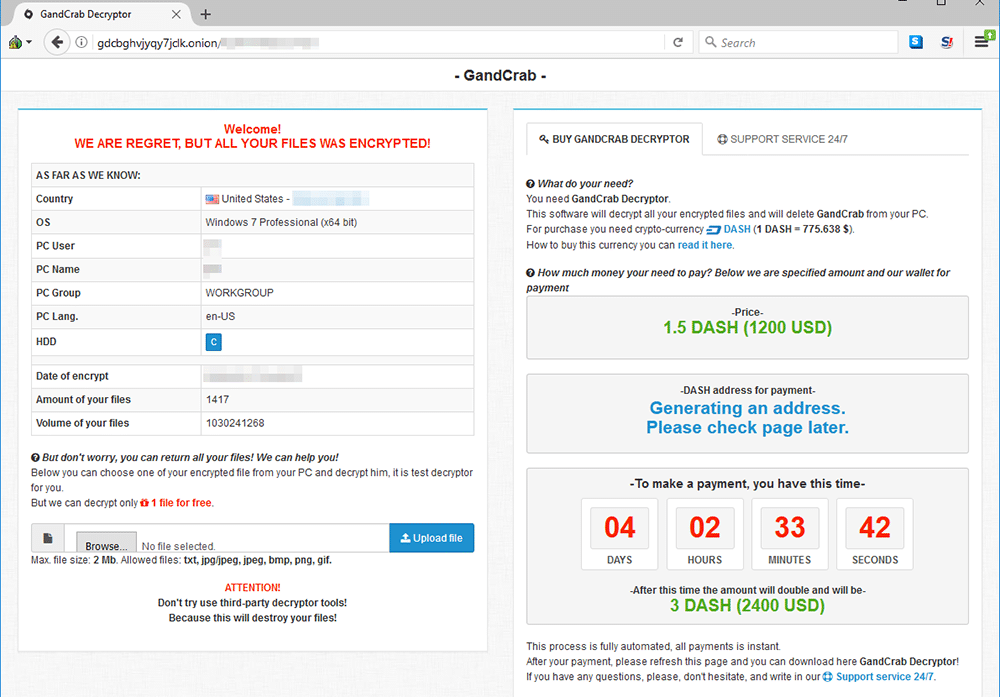
Ransome note screen. Source: malwarebytes.com
Like one would see with similar ransomware campaigns, the price of the decryption will increase after a certain period of time. This is done in order to induce urgency on the part of the victims. At current market prices, the decryption would cost $1,050. This is considerably more than the prices in previous attacks that have demanded in Bitcoin.
DASH has implemented a number of privacy enhancing protocols that try to hide the transactions in question. For example, they use something called Darksend mixing which will mix all of your coins with others on the blockchain. This could help when it comes to authorities tracking transactions.
Lessons to be Learned
It probably goes without saying that you should not be downloading pdf documents from people that you are not familiar with. This should be the tell-tale sign of a malicious exploit that someone is trying to get on your PC.
With respect to the other exploit vectors that GandCrab uses, you should avoid websites that you have been unknowingly redirected to. Try to avoid clicking on links to suspicious ads.
Lastly, and most importantly, installing effective antivirus programs would help to identify the exploits. Often, the user is the weakest link in a ransomware attack.
Featured Image via Fotolia & Dash



