Imagine your digital life as a vast map — a record of every online interaction, from messages and calls to website visits, social media engagements. Now, imagine this map spanning not just a week, but a year, or even a decade. Would you feel comfortable sharing this detailed account with anyone online?
This scenario highlights the stark reality of our online existence, where our every move leaves behind a trail of metadata — like breadcrumbs revealing what we're doing, when, and with whom. It's akin to having an open diary that anyone with the means can access and scrutinize.
As our digital footprints grow larger and more detailed by the minute, the risks to our privacy multiply. That's where Hopr comes in. It offers a shield against such unwarranted surveillance, providing robust tools to safeguard your online activities from prying eyes and potential exploitation.
In this Hopr review, we will explore the key features and workings of the Hopr network, including its unique privacy mechanisms such as anonymous routing, mixnets and probabilistic payments. We'll delve into how Hopr's proof-of-relay system incentivizes node operators, ensuring data is securely relayed through the network. Additionally, we'll discuss the HOPR token's utility, the SafeStaking mechanism for secure on-protocol staking, and guidance on running a Hopr node.
Hopr Review Summary
Hopr is a decentralized platform that ensures private and secure online communication through advanced encryption and a peer-to-peer mixnet. It utilizes a proof-of-relay mechanism and SafeStaking to incentivize node operators while protecting user metadata.
The Key Features of Hopr Are:
- Mixnets
- Anonymous Routing
- Packet Splitting
- Tickets and Payment Channels
- Probabilistic Payments
What is Hopr?
Hopr is a decentralized platform on the Ethereum mainnet designed to enable private and secure online communication and data exchange for individuals, companies, and devices. It operates as a peer-to-peer mixnet, where nodes act as relay points for transferring encrypted data between users.
 Hopr Is A Decentralized Platform That Enables Private Online Communication. Image via Hopr
Hopr Is A Decentralized Platform That Enables Private Online Communication. Image via HoprWhat sets HOPR apart from traditional mixnets, such as Tor, is its incentive mechanism known as proof of relay. This mechanism ensures that node operators are incentivized to relay data accurately and efficiently. By incorporating incentives, Hopr addresses a critical challenge faced by previous mixnets — how to encourage active participation and ensure the scalability of the network without compromising user privacy.
The Hopr mixnet is shrouded in layers of encryption and obfuscation, ensuring that data remains secure and anonymous as it traverses the network. Each node in the Hopr network plays a role in this process, encrypting and mixing data in such a way that only the intended recipients can decipher it. This end-to-end encryption scheme, coupled with the decentralized nature of the network, provides users with the assurance that their communications are shielded from prying eyes and malicious actors.
In addition to its focus on privacy and security, Hopr is also designed to be transparent and accessible to all. Anyone with the necessary technical expertise can contribute to the network by running a Hopr node, either on their computer or as a dedicated device connected to their router. By doing so, individuals can actively participate in the maintenance and operation of the network while earning HOPR tokens as rewards for their contributions.
The Hopr network is powered by HOPR, a utility token on the Ethereum network, which we'll touch on in more detail later.
How Does Hopr Work?
The Hopr protocol protects your data and your connection metadata. But how does it achieve it?
Anonymous Routing
Imagine you're sending a secret message to your friend, but you're worried about someone snooping on your communication. You could encrypt your message so that even if someone opens it, they can't understand what it says. But what if you don't want anyone to know you're even talking to your friend? Encrypting the message alone won't solve that problem. So, how do you keep your communication completely anonymous?
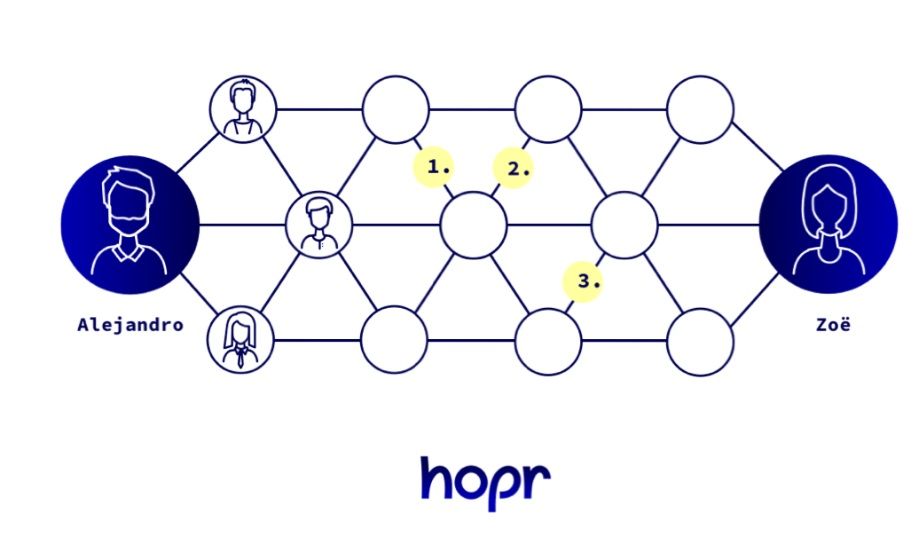 Anonymous Routing Works a Bit Like a Game of Pass-The-Parcel. Image via Hopr
Anonymous Routing Works a Bit Like a Game of Pass-The-Parcel. Image via HoprEnter anonymous routing, which works a bit like a game of pass-the-parcel. Instead of sending your message directly to your friend, you put it in multiple layers of envelopes — like those Russian dolls that nest inside each other. Each envelope has a different address, leading to different people in a chain.
When someone gets the package, they open the outermost envelope, which reveals the next address. They then pass the remaining envelopes to the next person, and this goes on until the final envelope with the message reaches your friend. Here's the neat bit: no one in the chain knows the full route or who the sender or final recipient is because they only see the address of the next person in line.
In the digital world, this process is called relaying, and it's the backbone of Hopr. It’s also what gives the company its name, because data “hops” from one person to the next before reaching its destination. Instead of physical envelopes, data is wrapped in layers of encryption, making it impossible for anyone to see the full message or the complete route it takes.
But even with this system, there's a risk of someone figuring out the connections between nodes and unravelling the anonymity. To counter this, Hopr utilizes packet splitting. Imagine if your message is split into pieces, each with a number. These pieces take different routes through the network, making it much harder for anyone to trace the complete message.
Mixnets
Even with anonymous routing and packet splitting, there's a chance that someone could piece together clues from things like timing or message size. That's why Hopr introduces mixing, which adds another layer of complexity to the process. It's like constantly shuffling a deck of cards so no one can predict the order. This makes it even tougher for anyone trying to spy on the network to make sense of what's going on.
 Mixnets Add Another Layer of Complexity To The Process. Image via Hopr
Mixnets Add Another Layer of Complexity To The Process. Image via HoprHere's how it works: Imagine you're a secret agent hoping to send a message across town without anyone knowing it's from you or where it's going. You could just hand it to a courier and hope for the best, but there's a chance someone might follow the courier and figure it out. So, you come up with a clever plan. Instead of just one courier, you enlist the help of many people. Each person receives a part of the message. Your intended recipient then puts the message together.
This is essentially how a mixnet works. Instead of just sending one message at a time, it handles many messages simultaneously, making it much harder for anyone to trace the origin or destination of any single message.
But there's a catch: running a mixnet is complicated and resource-intensive. So, to keep the mixnets running smoothly, Hopr needed to make sure everyone involved was motivated to participate.
Incentives
Encrypting, mixing, and relaying data through Hopr requires a lot of computing power, which costs money. While some people might be willing to contribute to the network without expecting anything in return, relying solely on altruism isn't sustainable in the long run.
One solution is to have the users who benefit from the privacy network pay for its upkeep. This seems straightforward, but there are challenges. One approach is a subscription model, where users pay to use the service, and the funds are then distributed to the people who run the nodes that make the network function.
However, relying on a central authority to manage these funds introduces risks, like the potential for corruption or data breaches. So, a more appropriate solution was to integrate payments directly into the network itself. For example, each time someone sends data through the network, a payment travels along with it. This payment is then split among the nodes that help relay the data, ensuring that everyone gets compensated for their work.
But how can we be sure that the nodes are actually doing the work they're paid for? After all, if someone can't be tracked, what's stopping them from taking the money without doing anything? Through a mechanism called Proof of Relay, nodes only receive their payment after successfully passing on the data.
Proof of Relay
Trust isn't a viable foundation. This is why crypto is referred to as "trustless," eliminating the need to trust any single member due to the system's inherent reliability.
In the realm of Hopr, the objective was to guarantee nodes received fair compensation only after executing their relay tasks. One conceivable approach involved nodes compensating their predecessors. However, this strategy invited potential exploitation — why bother paying if one can evade the responsibility without consequence?
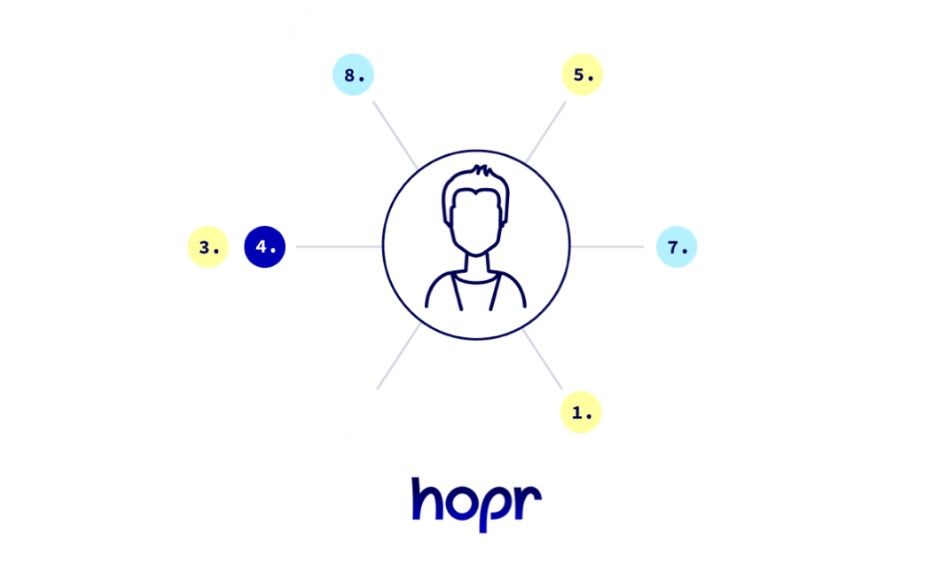
 Hopr's PoS Consensus Is Called Proof of Relay. Image via Hopr
Hopr's PoS Consensus Is Called Proof of Relay. Image via HoprThe Hopr proof of relay is like a digital handshake between nodes. When data traverses the network, each node receives a payment, locked with a unique key. To unlock the payment, both halves of this key are required.
As data progresses along the chain, nodes exchange halves of their keys. This process ensures that all involved in relaying the data receive rightful compensation. Attempting to circumvent responsibilities by withholding data results in forfeiture of payment due to the incomplete key.
Proof of relay not only aligns incentives but also establishes a trustworthy and equitable network environment for all participants involved.
How Hopr Preserves Privacy
Hopr ensures privacy while incentivizing node runners for their role. Here's how it maintains privacy:
Tickets and Payment Channels:
- Instead of direct payments for relaying data, HOPR uses tickets and payment channels.
- When a node successfully relays data, it receives a cryptographic ticket.
- These tickets are akin to lottery tickets, with only a few resulting in significant rewards, while most remain worthless.
By introducing this randomness, HOPR reduces the number of blockchain transactions associated with relaying data, minimizing the metadata footprint.
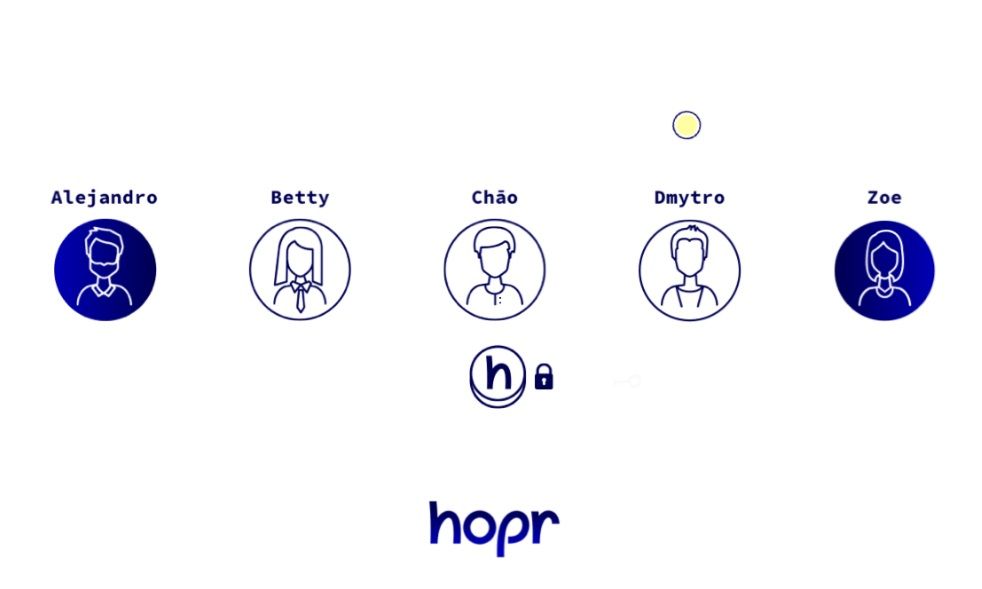
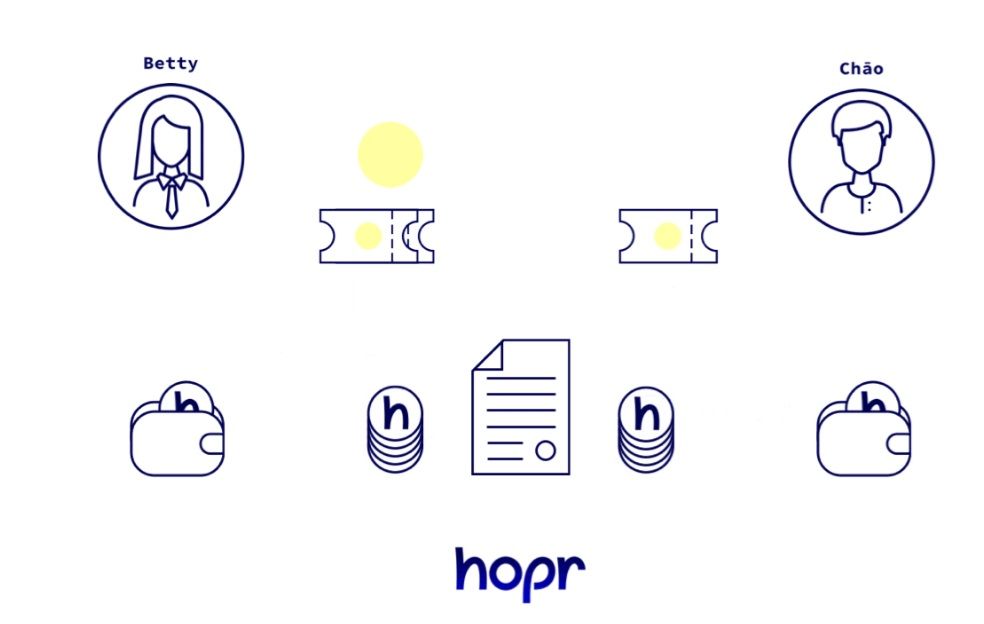 Hopr Ensures Privacy While Incentivizing Node Runners. Image via Hopr
Hopr Ensures Privacy While Incentivizing Node Runners. Image via HoprProbabilistic Payments:
- Rather than triggering a payment transaction for every relayed data packet, node runners receive tickets.
- Each ticket has a probability of winning a substantial reward, reducing the number of transactions recorded on the blockchain.
- For example, a ticket might have a 1% chance of winning a large reward, such as 100 HOPR.
This approach ensures that node runners receive their deserved rewards while minimizing the metadata leakage associated with blockchain transactions.
By combining tickets, payment channels, and probabilistic payments, Hopr incentivizes node runners without compromising the privacy of the network. This trustless system ensures that node runners are rewarded for their efforts while maintaining the network's integrity and privacy.
HOPR Token
The HOPR token serves three primary purposes:
- Users pay with HOPR tokens to send data through the HOPR network privately and securely.
- Node runners stake HOPR tokens to earn rewards for relaying data, receiving fees in HOPR, including tokens from cover traffic.
- HOPR tokens grant users voting power in the HOPR Association DAO.
HOPR tokens will be released over four years from an initial circulating supply of 130 million; its max supply is 1 billion coins. A quarter of these tokens are reserved as rewards for stakers who relay cover traffic.
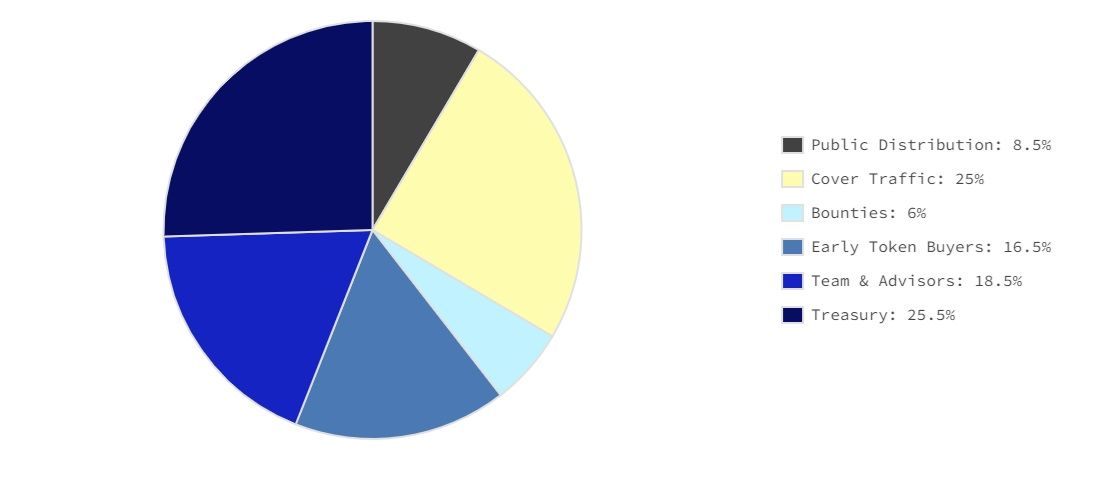 HOPR Tokens Will Be Released Over Four Years. Image via Hopr
HOPR Tokens Will Be Released Over Four Years. Image via HoprAccording to CoinGecko, HOPR is the 729th largest coin with a market cap of $43.6 million. Its current price is down over 90% from its all-time high, which it achieved in March 2021.
Where to Buy HOPR?
HOPR isn't as widely available as many other tokens. Still, you can buy it on exchanges like Coinbase, Gate.io, and MEXC. Also, check out our ranking of the best crypto exchanges.
Uniswap is among the decentralized exchanges where you can buy HOPR.
Hopr SafeStaking
SafeStaking is Hopr's approach to on-protocol staking, designed to secure node runner funds while maintaining a decentralized and incentivized privacy network. The primary goal of Hopr is to create a privacy mixnet where node runners are rewarded for relaying data. SafeStaking ensures that these funds are secure, even if a node is compromised, similar to proof-of-stake systems but with added security features.
In this system, node runners store their funds in a highly secure smart contract account known as the Hopr Safe. They then create a node and link it to their Safe. The amount of funds staked in the node determines the traffic it receives, which in turn increases its earning potential. Managing these funds involves two keys:
- The admin key, which is controlled by the node runner and is used to approve transactions from the HOPR Safe
- The chain key, which is stored locally on the node and used to make blockchain transactions such as opening payment channels or redeeming tickets.
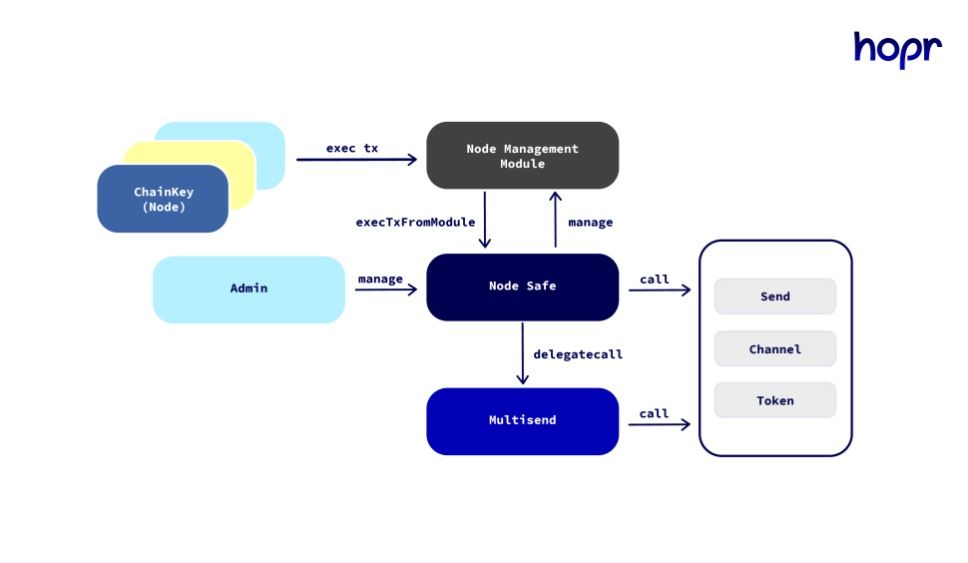 SafeStaking is Hopr's Approach To On-Protocol Staking. Image via Hopr
SafeStaking is Hopr's Approach To On-Protocol Staking. Image via HoprThe node can use the funds in the Hopr Safe in limited amounts to perform necessary operations, but these transactions must be approved by the node runner using the admin key. This setup allows for a customizable balance between security and convenience.
Node runners can choose how much access their node has to the funds in the HOPR Safe, ranging from giving the node full access to requiring admin key approval for every transaction. Additionally, node runners can decide which keys are needed for various actions like sending messages, redeeming tickets, or opening channels, and they can set limits on how much the node can access without additional approval.
Running a Hopr Node
To use the Hopr network, you need to create a Hopr Safe and install a node. There are two methods for installing the node: using a Dappnode device or Docker.
A Hopr Safe is essential for securely storing your funds while operating a node. To create one, follow the onboarding process and ensure you have a minimum of 30,000 wxHOPR tokens (or 10,000 wxHOPR if you have a Network Registry NFT).
The Dufour release is currently permissioned, requiring you to be added to the network by the HOPR association, which may take 1-2 weeks. Hardware requirements include:
- Node can be run on: PC/Mac/Raspberry Pi/Server
- OS: macOS X / Linux OS (Ubuntu 16 and greater versions, Debian 10.x)
- Dual Core CPU ~ 2 GHz
- 4GB of RAM or greater
- Disk space of at least 3GB
- x64 architecture CPU (any)
Setting up a custom RPC provider is crucial for smooth node operation. The best method is running your own Gnosis Chain node, with detailed steps provided for VPS/PC/Mac and Dappnode users. Alternatively, you can use third-party RPC providers like Alchemy, Infura, or Quicknode, or public RPC endpoints from chainlist.org, though these are less reliable.
Hopr Review: Closing Thoughts
Hopr offers a robust solution to protect against unwarranted surveillance by providing a decentralized platform for private and secure online communication and data exchange.
It employs a peer-to-peer mixnet that utilizes anonymous routing and packet splitting to ensure anonymous and secure data transmission. Its proof-of-relay mechanism incentivizes node operators to relay data accurately, enhancing network participation and scalability while maintaining privacy.
The Hopr protocol leverages encrypted mixnets, probabilistic payments and a decentralized incentive structure to preserve user anonymity and protect metadata. By incorporating HOPR tokens, the network facilitates private transactions, rewards node runners, and supports decentralized governance through the HOPR Association DAO.
Hopr stands out by combining advanced privacy measures, a decentralized incentive system, and flexible security features, making it a comprehensive solution for safeguarding online privacy in an increasingly interconnected world.





