If you have clicked on this article, it is probable that privacy and security are of significant interest to you. The evolving Web3 has transcended crypto wallets from mere tools for transactions to our digital identities. These wallets reflect our on-chain activities, store our valuable assets, and serve as our passports in the decentralized ecosystem. Given their pivotal role, maintaining robust wallet custody is not just an option but a necessity to safeguard our crypto-economic security and personal safety.
Cryptocurrency wallets come in a myriad of forms, each catering to different needs. Some are tailored for the rapid pace of frequent trading, others for the intricate world of DeFi protocols. However, when it comes to unparalleled security, no option surpasses a hardware wallet. Unlike their software counterparts, hardware wallets provide a tangible solution to digital identity protection. When not in use, these devices can be completely disconnected from the internet, effectively placing your assets in a digital vault that is impervious to tampering. Once reconnected, they seamlessly reintegrate you into the blockchain world, ready to resume your on-chain activities.
Among the diverse array of hardware wallet providers, names like Ledger and Trezor often dominate the conversation. Yet, in this review, we turn our attention to the Keystone 3 Pro. Not only does this device boast the largest screen of any hardware wallet, but it also brings a unique blend of features designed to enhance user experience and security.
Whether you are contemplating your first hardware wallet purchase or considering an upgrade, this Keystone 3 Pro review will provide you with the insights needed to make an informed decision. Dive in as we explore what sets this device apart in the competitive landscape of cryptocurrency security.
A Primer on Hardware Wallets
Safeguarding your crypto assets is paramount; they are a medium of exchange and fuel required to perform any operation on-chain. Secure storage solutions are becoming more crucial with the increasing popularity of digital currencies. Crypto storage solutions are broadly classified in two types — hot and cold wallets.
Hot wallets are connected to the internet, making them convenient for transactions but susceptible to online threats. On the other hand, cold wallets remain offline, creating an impenetrable wall against cyberattacks. Cold wallets are the gold standard of crypto asset security.
What Are Hardware Wallets?
Hardware wallets are physical devices designed specifically to store your private keys offline. Unlike software wallets, which are vulnerable to hacks and malware, hardware wallets keep your private keys isolated from your computer and the internet. This means that even if your computer is compromised, your crypto assets remain safe.
Typically, hardware wallets look like small USB drives or compact gadgets with screens and buttons. These devices are built to be robust, portable, and user-friendly. Their size and form factor make them convenient to carry and easy to store securely.
Using a hardware wallet involves a few straightforward steps:
- Initial Setup: Connect the device to your computer or smartphone and follow the instructions to set up your wallet. This usually involves creating a PIN and writing down a recovery seed phrase, which is crucial for recovering your assets if the device is lost or damaged.
- Receiving Funds: To receive funds, generate a receiving address on the hardware wallet and share this address with the sender.
- Sending Funds: When you need to send funds, initiate the transaction on your computer or smartphone. The hardware wallet will then prompt you to confirm and sign the transaction, securely approving it without exposing your private keys.
By isolating private keys from potentially compromised environments, hardware wallets provide an unmatched level of security for your digital assets.
 Keystone Wallet Homepage
Keystone Wallet HomepageImportance of Hardware Wallets
The primary reason for using hardware wallets is security. They offer the highest level of protection against online threats, making them essential for anyone serious about safeguarding their cryptocurrencies. Here’s why hardware wallets are the most secure form of crypto storage:
- Offline Security: Hardware wallets store your private keys offline, away from the reach of hackers and malware. This offline storage method, known as cold storage, is crucial for protecting against remote attacks.
- Secure Transaction Signing: When you perform transactions, the hardware wallet signs the transaction internally and only exposes the signed transaction, not your private key. This ensures that even if your computer is infected with malware, your private keys remain safe.
- Recovery and Backup: Most hardware wallets provide a recovery seed phrase during setup. This seed phrase is a backup that can be used to restore your wallet in case the device is lost, stolen, or damaged. As long as the seed phrase is kept secure and private, your assets can always be recovered.
In the Web3 ecosystem, several hardware wallets have gained a reputation for their security and usability:
- Ledger Nano X: Known for its robust security and Bluetooth connectivity, the Ledger Nano X supports a wide range of cryptocurrencies and integrates with popular software wallets.
- Trezor Model T: With a touchscreen interface and support for numerous cryptocurrencies, the Trezor Model T is a user-friendly option for secure storage.
- Keystone 3 Pro: Featuring the largest screen among hardware wallets, Keystone 3 Pro offers a seamless user experience and enhanced security with its air-gapped design and QR code communication for transactions.
Each of these wallets brings unique features to the table, catering to different needs and preferences. However, the underlying principle remains the same: providing a secure and reliable way to store and manage your digital assets.
In conclusion, as the digital landscape continues to evolve, hardware wallets remain a cornerstone of secure crypto storage. Their ability to keep private keys offline and provide robust protection against cyber threats makes them indispensable tools for anyone looking to protect their crypto investments.
Checkout our selection of the best hardware wallets, or watch Guy’s view about the wallets on YouTube:
What is Keystone?
Keystone, formerly known as Cobo Vault, has established itself as a pioneering force in the realm of hardware wallets. Relaunched under the Keystone brand, the company is led by CEO Lixin Liu and CTO Aaron Chen, who have been instrumental in pushing the boundaries of crypto security. Keystone’s mission is clear: to provide timeless security for digital assets, ensuring that users around the globe can safeguard their cryptocurrencies with unparalleled peace of mind.
Since its inception in 2018, Keystone has consistently demonstrated a commitment to innovation and security. The company first made waves with the Cobo Vault Ultimate, a premium hardware wallet that met American military standards for robustness (MIL-STD-810G). This achievement underscored their dedication to building secure and resilient devices. Keystone's approach to security is deeply rooted in their product design and development ethos, making them a trusted name among both individual and enterprise users.
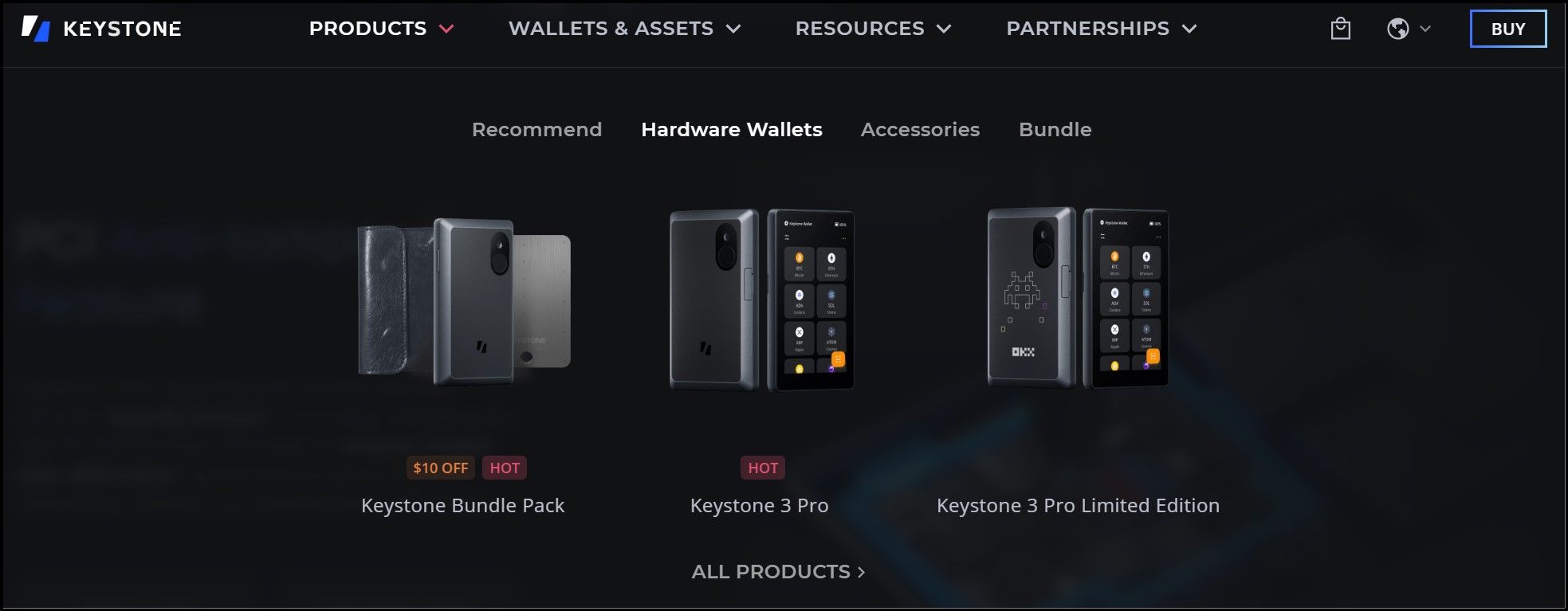 Keystone Product Offerings | Image via Keystone
Keystone Product Offerings | Image via KeystoneOne of Keystone’s significant contributions to the crypto community is the introduction of QR code data transmission. This method was developed in collaboration with the Airgapped Wallet Community to provide 100% air-tight security. By using QR codes, Keystone ensures that data transfer between devices remains completely air-gapped, eliminating risks associated with USB or Bluetooth connections.
Keystone’s commitment to transparency and security is exemplified by its decision to publicly share their Secure Element firmware and auditing reports. They have also innovated in the realm of recovery phrases by developing three types of metal storage solutions. These products provide durable and secure options for storing recovery phrases, ensuring users can recover their assets even in the face of disaster.
The company has also made strides in improving software security. They developed a Bitcoin-only firmware to enhance security for the Bitcoin community and have been recognized for their multi-signature solutions. Additionally, Keystone addressed the critical issue of blind signing for the Ethereum community.
Keystone 3 Pro: What’s in the Box?
The Keystone 3 Pro is well packaged in a sturdy black box. Inside, you will find the wallet device, a removable and rechargeable battery along with a charging cable, a battery pack, some paperwork and a leaflet to write seed phrase.
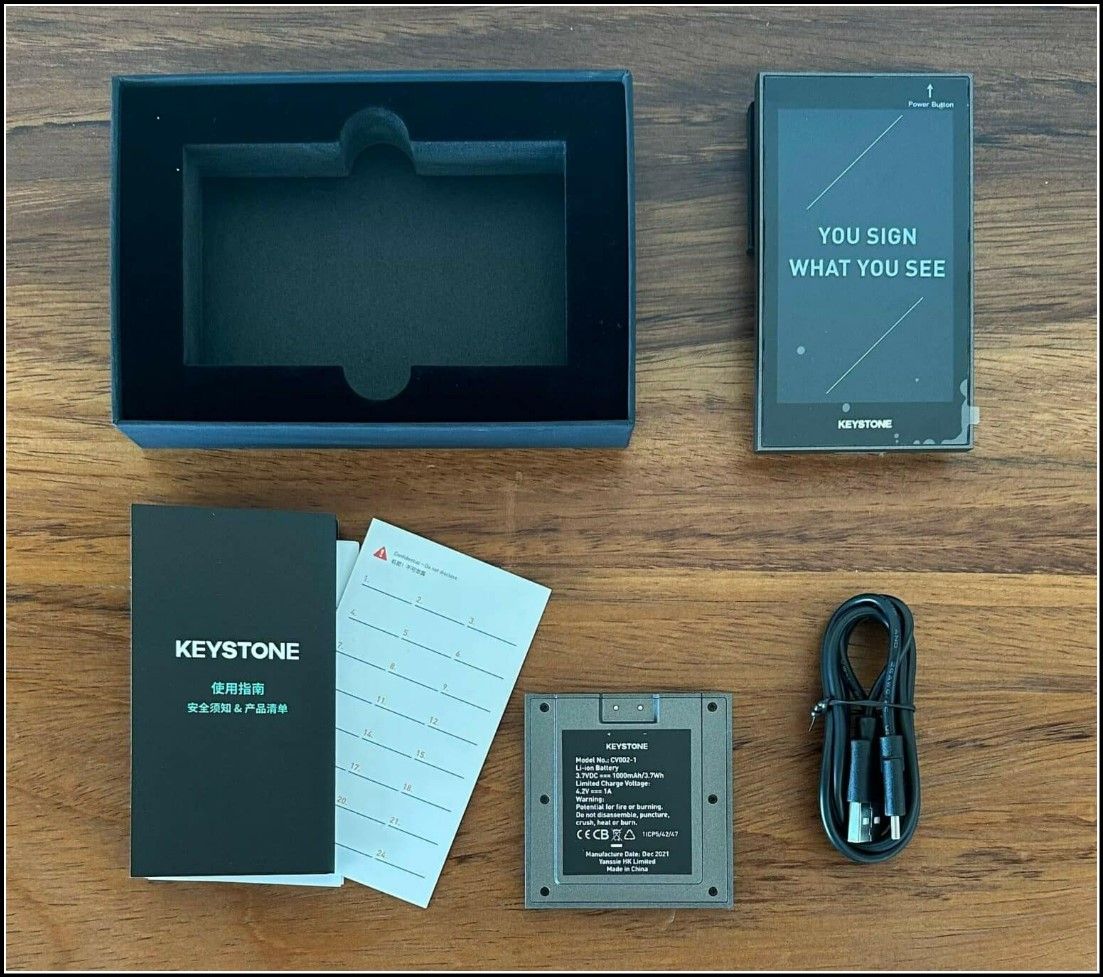 Keystone Hardware Wallet Unboxing | Image via 99 Bitcoins
Keystone Hardware Wallet Unboxing | Image via 99 BitcoinsKeystone Wallet Metamask Integration
In April 2022, Keystone partnered with Metamask to combine the robust security of its hardware wallet with the most versatile and popular software wallet — Metamask. The collaboration enhanced Metamask and Keystone user experience by allowing air-gapped connection to Web3.
Key features of the integration:
- QR Code-Based Transaction Signing: Keystone utilizes QR codes to transmit transaction data between the wallet and MetaMask, eliminating the need for USB or Bluetooth connections. This method ensures that private keys never leave the secure environment of the hardware wallet and are never exposed to potentially compromised devices. This form of air-gapped communication enhances security by minimizing the risk of malware infiltration and unauthorized access.
- Full Interoperability: The integration supports all EVM-compatible blockchains, such as Ethereum, Polygon, and Fantom. This means users can seamlessly manage assets and perform transactions across different networks directly through MetaMask while leveraging the security of Keystone’s hardware wallet. This compatibility extends Keystone’s utility, making it a versatile tool for users engaged in diverse Web3 activities.
- Enhanced Security with Transparency: Keystone’s approach emphasizes transparency in data transmission. Users can verify the content of QR codes before signing, ensuring that no sensitive information is leaked. This feature is crucial for preventing blind signing, where users might unknowingly approve malicious transactions. The large touch screen on the Keystone device further aids in scrutinizing transaction details, reducing the likelihood of user error.
- Open-Source Commitment: Both MetaMask and Keystone share a commitment to open-source development. Keystone has pioneered the adoption of open-source standards for QR code data transmission and secure element firmware. This openness allows for community scrutiny and trust, which is vital in the security-conscious world of cryptocurrencies.
By combining MetaMask's ease of use and extensive DApp support with Keystone's high-security hardware, users can enjoy a robust and secure way to manage their crypto assets. This integration is particularly beneficial for those deeply involved in DeFi, NFTs, and other Web3 applications where security and interoperability are paramount.
Keystone 3 Pro Supported Coins
Keystone, like every major hardware wallet on the market, offers robust support for a vast library of digital assets.
It supports over 5,500+ coins and tokens spread across more than 200 different blockchains. This extensive support allows users to securely manage a wide variety of cryptocurrencies, ensuring that Keystone remains versatile and accommodating for diverse investment portfolios.
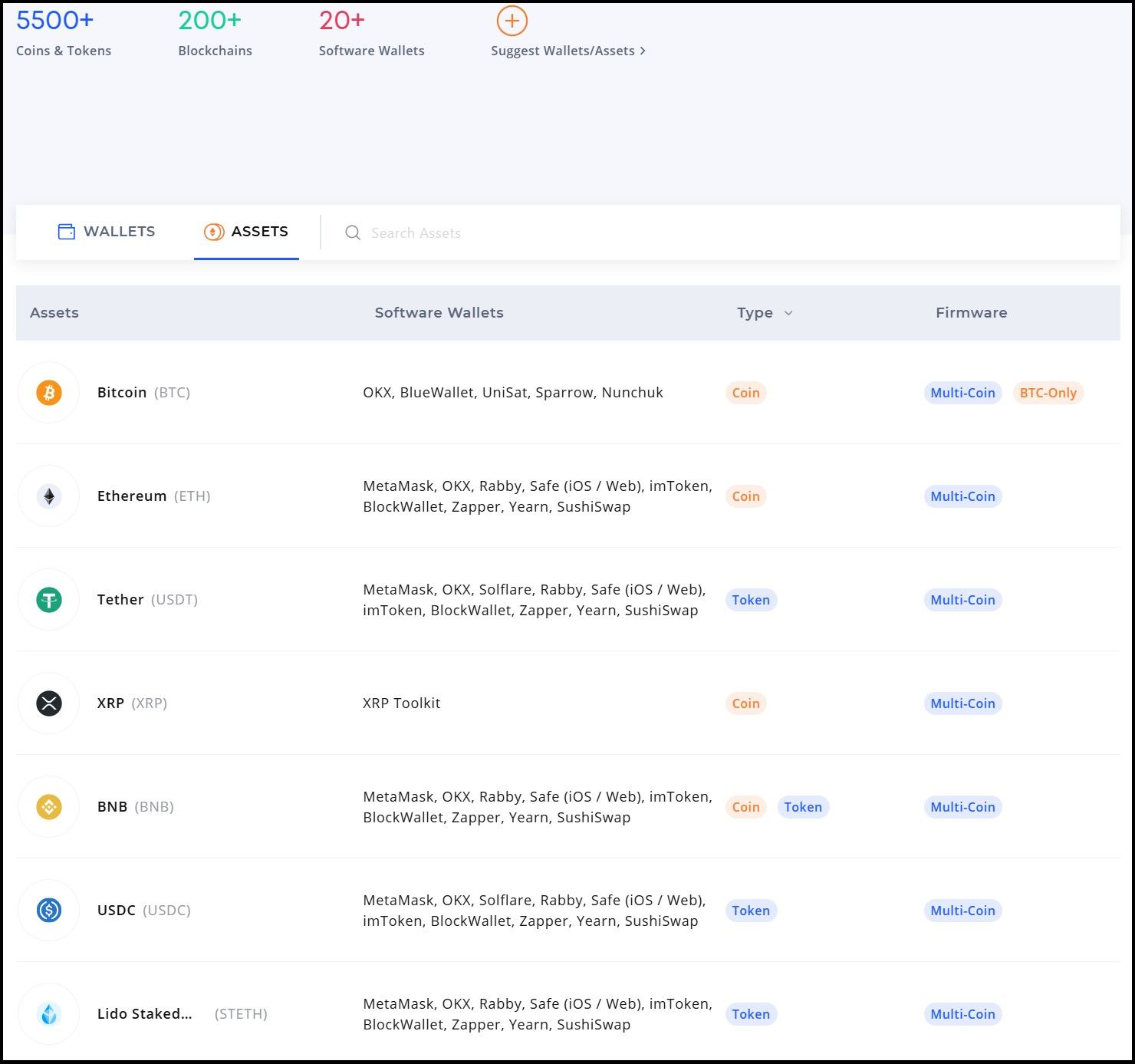 Keystone Wallet Supported Assets
Keystone Wallet Supported AssetsHowever, Keystone's approach to coin support differs significantly from competitors like Ledger, which utilizes its proprietary Ledger Live app to provide a seamless user experience for managing a broad array of assets. Through Ledger Live, users can access and manage thousands of coins and tokens, and for those not directly supported by Ledger Live, additional support is available through integrations with over 20 third-party software wallets. These include popular wallets such as MetaMask, OKX Wallet, Keplr, and BlueWallet. This multi-faceted integration strategy allows Ledger to cover a vast expanse of blockchain networks efficiently.
In contrast, Keystone does not have a proprietary app akin to Ledger Live. Instead, it relies entirely on integrations with third-party wallets to support its extensive range of coins. This means that Keystone users must utilize compatible third-party wallets for managing their assets. While this approach maintains Keystone's flexibility and interoperability, it requires users to navigate through different software wallets for different coins and functionalities.
One more area where Keystone falls short compared to Ledger is its native staking capabilities. While Ledger Live supports staking for several ERC-20 assets directly within its app, Keystone lacks this native feature. Keystone users can participate in staking, but this is limited to specific assets and requires third-party wallet integration. For instance, users can stake Polkadot (DOT) using the Keystone wallet, but this does not extend to a broad range of assets like those available through Ledger Live's staking options.
Despite these differences, Keystone's commitment to supporting a vast array of coins through secure, third-party integrations keeps it as a strong contender in the hardware wallet space. This strategy ensures that users can find the tools and connections they need, albeit through a slightly more complex setup compared to the streamlined experience offered by competitors like Ledger.
How Much Does Keystone 3 Pro Cost?
The Keystone 3 Pro is currently being sold for $149. However, there are two versions that result in a higher price tag:
- The wallet with a 32GB SD card costs about $164.
- Add a pouch to the wallet, minus the SD card, and you're looking at roughly $176.
There's a lifelong 20% discount for Ledger users as well.
Keystone Wallet Security and Features
The Keystone 3 Pro stands out in the competitive landscape of hardware wallets by offering a unique blend of cutting-edge security features and user-friendly attributes. Designed to provide robust protection for your digital assets, it leverages advanced technologies to ensure that your cryptocurrencies remain safe and accessible only to authorized users.
Here’s a detailed look at the security measures and features that make the Keystone 3 Pro a top choice for crypto enthusiasts.
Security
- QR Code Transactions: The Keystone 3 Pro facilitates secure, air-gapped transactions through its innovative use of QR code technology. By enabling users to sign transactions via QR codes scanned with its built-in camera, Keystone eliminates the need for physical connections like USB or Bluetooth. This approach minimizes exposure to malware and other online threats, maintaining the device's isolation from potentially compromised computers or networks.
- Biometric Authentication: Enhancing user security and convenience, the Keystone 3 Pro includes a fingerprint authentication feature. This biometric security measure ensures that only the rightful owner can access the wallet, significantly reducing the risk of unauthorized access. By replacing or supplementing traditional passwords with fingerprint recognition, it adds an extra layer of security against password theft and hacking attempts.
- Triple Layered Security: Keystone 3 Pro sets itself apart with its triple-layered security architecture, incorporating three distinct secure elements: the Microchip ATECC608B, Maxim DS28S60, and Maxim MAX32520.
- Microchip ATECC608B: Provides hardware-level security and authorizes secure interactions, safeguarding recovery phrases.
- Maxim DS28S60: Ensures a trusted platform module for secure recovery phrase storage.
- Maxim MAX32520: This secure microcontroller unit protects fingerprint data with encrypted flash storage, making sure that biometric verification is performed securely within the MCU. This robust setup, exclusive to the Keystone 3 Pro, guarantees multiple layers of protection for both recovery phrases and biometric data.
 Keystone Offers Triple-Layered Security | Image via Keystone
Keystone Offers Triple-Layered Security | Image via Keystone- Support for Multiple Recovery Phrases: Keystone 3 Pro allows users to manage up to three distinct recovery phrases, each protected by different passwords. This capability is ideal for users with multiple crypto accounts, providing a streamlined way to switch between wallets without compromising security. Each set of recovery phrases is isolated, ensuring that even if one set is compromised, others remain secure.
- Open Source and Audited: Keystone embraces transparency by adopting open-source firmware and hardware. This approach allows the crypto community to audit, verify, and contribute to the wallet’s development. Open-source principles enhance trust and security, as the code is continuously scrutinized by developers and security experts worldwide.
- Shamir Secret Sharing Scheme: For enhanced backup security, Keystone 3 Pro supports Shamir Secret Sharing (SLIP 39). This method allows users to split their recovery seed into multiple parts, specifying how many parts are required to restore the wallet. For example, users can opt for a 2-out-of-3 or 5-out-of-10 configuration, providing flexibility and added security in safeguarding their recovery data.
Features
- Large Screen: The Keystone 3 Pro is equipped with a large 4-inch touchscreen, offering a clear and detailed view of transaction information. This sizable screen facilitates biometric authentication and ensures that users can thoroughly review transaction details before signing, enhancing both security and usability.
- Customization: One of the unique aspects of the Keystone 3 Pro is its customizable backplate. Users can personalize their device with a favorite image, adding a personal touch to their hardware wallet. This feature not only provides aesthetic appeal but also allows for easy identification of individual devices.
- MetaMask Integration: Keystone is fully integrated with MetaMask, one of the most popular Web3 wallets. This deep integration ensures seamless interaction with decentralized applications (DApps) and simplifies the management of digital assets across various platforms. Users can easily sign transactions and access their assets through MetaMask while benefiting from the high-security features of the Keystone 3 Pro.
The Keystone 3 Pro combines sophisticated security technologies with practical features, making it a standout choice in the hardware wallet market. Its air-gapped QR code transactions, robust biometric security, and triple-layered secure elements provide unparalleled protection for digital assets.
Additionally, the device’s large screen, customizable backplate, and seamless integration with MetaMask enhance the user experience. For those seeking a secure and versatile hardware wallet, the Keystone 3 Pro offers an exceptional solution that prioritizes both safety and usability.
Keystone 3 Pro Setup and Getting Started Guide
Setting up your Keystone 3 Pro hardware wallet is a straightforward process. Follow these steps to get your Keystone 3 Pro up and running:
Step 1: Unboxing and Charging
- Unbox Your Keystone 3 Pro: Remove the device from the box along with the included accessories: charging cable, recovery phrase cards, and user manual.
- Charge Your Device: Use the provided USB-C cable to fully charge your Keystone 3 Pro before setup. A full charge ensures the device operates smoothly during the initialization process.
Step 2: Initial Setup
- Power On the Device: Press and hold the power button on the side of the device until it turns on.
- Select Your Language: Upon powering up, you will be prompted to select your preferred language from the list of available options.
- Create or Import a Wallet
- Create a New Wallet:
- Choose this option if you are setting up a new wallet. The device will generate a unique recovery phrase (12, 18, or 24 words).
- Write down the recovery phrase carefully on the provided cards. Do not store it digitally or share it with anyone.
- Confirm your recovery phrase by entering the words in the correct order as prompted by the device.
- Import an Existing Wallet: Select this option if you have an existing wallet to import. Enter the recovery phrase or private key associated with your current wallet.
- Create a New Wallet:
- Set Up Your Security
- Create a PIN: Set a PIN for additional security. This PIN will be required each time you access the wallet.
- Enable Biometric Authentication: You can add fingerprint authentication for added security. Follow the on-screen instructions to register your fingerprint.
 Setting PIN in Keystone Wallet | (Image Source)
Setting PIN in Keystone Wallet | (Image Source)Step 3: Using the Keystone 3 Pro
- Accessing the Main Menu: After setup, you’ll be directed to the main menu where you can manage your wallets, check balances, and initiate transactions.
- Adding Coins and Tokens: Navigate to the “Add Asset” section to include various cryptocurrencies in your wallet. Keystone supports over 5500 coins and tokens across 200+ blockchains.
- Receiving Funds: Select the cryptocurrency you want to receive, then display the QR code or provide the receiving address to the sender.
- Sending Funds:
- To send funds, choose the asset, enter the recipient’s address, amount, and any additional transaction details.
- Confirm the details on the large touchscreen and sign the transaction using the QR code mechanism.
- MetaMask Integration: Keystone 3 Pro integrates seamlessly with MetaMask. To connect, go to MetaMask's settings, select “Connect Hardware Wallet,” and follow the prompts to scan the QR code and link your Keystone.
Step 4: Advanced Features
- Managing Multiple Recovery Phrases: Keystone allows you to manage up to three different recovery phrases, each protected by unique passwords. This feature is ideal for users who oversee multiple crypto accounts.
- Using Shamir Backups: If you choose to use Shamir Backup, navigate to the backup section and configure your preferred shard settings. This allows you to split your backup seed into multiple parts for enhanced security.
- Customization: Personalize your Keystone with a custom backplate. Follow the instructions on the device or visit the Keystone website to upload your favorite image.
Step 5: Security Tips
- Keep Your Recovery Phrase Safe: Store your recovery phrase in a secure, offline location. Consider using metal storage solutions for added durability.
- Regularly Update Firmware: Keep your device’s firmware up to date by checking for updates on the Keystone website. This ensures you benefit from the latest security features and improvements.
- Avoid Sharing Sensitive Information: Never share your recovery phrase, private keys, or PIN with anyone. These are critical for accessing your funds and should be kept confidential.
Keystone 3 Pro Review: Closing Thoughts
The Keystone 3 Pro stands out as a robust and reliable hardware wallet, equipped with industry-leading security features that cater to users who prioritize the utmost protection for their digital assets. Its integration with a wide array of wallet applications ensures that software support is comprehensive and versatile, making it suitable for various use cases and preferences.
One of Keystone 3 Pro’s defining advantages is its unique approach to security. The use of QR code transactions for signing ensures that the wallet remains air-gapped, significantly reducing the risk of malware and unauthorized access. Additionally, the implementation of the Shamir Secret Sharing scheme provides a sophisticated method for securing and recovering backup seeds, a feature that sets it apart from competitors like Ledger.
However, it’s important to consider Keystone’s limitations in the realm of DeFi and active asset management. While it excels in providing secure long-term storage, it does not natively support staking for a wide range of assets. Users looking to actively participate in DeFi or leverage staking features might find Ledger Live’s comprehensive staking support more aligned with their needs.
For anyone prioritizing security above all else, the Keystone 3 Pro is a worthy investment in the world of hardware wallets.





