“Anonymous” in crypto isn’t a wallet setting, it’s a system you build. Most blockchains are public by design, so the real question is how hard you can make it to link your transactions back to you through on-chain patterns, network metadata, and sloppy habits.
In this guide, we break down what anonymity actually takes in 2026, review the wallets that help reduce linkability, and show the privacy hygiene that matters more than any single app.
Quick Verdict: Our Top Anonymous Wallet Picks by Use Case
Best for Bitcoin Privacy: Wasabi Wallet
Verdict: The easiest way to run repeatable CoinJoin privacy workflows on BTC without building a full custom stack.
Best for Power Users: Sparrow Wallet
Verdict: The best choice for strict UTXO control, labeling, PSBT flows, and full-node setups that keep identities separated.
Best for Monero: Cake Wallet
Verdict: A Monero-first mobile wallet with strong privacy defaults, making XMR practical without constant foot-gun risks.
Best Beginner Wallet: Exodus
Verdict: Great UX for learning self-custody, but it’s convenience-first, so don’t treat it as an anonymity tool.
Best Hardware Wallet: Ledger / Trezor
Verdict: Excellent key security for long-term storage, but your privacy still depends on the software stack and broadcast path you choose.
Most Secure Air-Gapped: ELLIPAL
Verdict: Strong physical separation via QR signing, ideal if you want minimal cable/wireless exposure for signing devices.
Best Minimalist Hardware: BitBox02
Verdict: A clean, security-first device that shines when paired with a privacy-aware Bitcoin wallet and (ideally) your own node.
Key Takeaways (TL;DR)
- Anonymous ≠ private by default: A wallet can be no-KYC and still leak metadata through servers, integrations, and behavior.
- Bitcoin is pseudonymous: Identities aren’t printed on-chain, but transaction patterns can still be clustered and linked over time.
- Wallets alone don’t guarantee anonymity: Privacy comes from coin control, node choice, routing, and how you transact.
- Operational security matters more than tools: One sloppy merge, reuse, or predictable pattern can undo “privacy” in a single click.
Privacy-Focused Wallet Comparison Table
| Wallet | Type | Chains | Privacy Tech | Tor Support | Full Node Support | Open Source | KYC Required | Price | Best For |
| Wasabi Wallet | Software | BTC | CoinJoin (WabiSabi), coin control | Yes (default) | Yes | Yes | No | Free | Automated BTC privacy workflows |
| Sparrow Wallet | Software | BTC | PayJoin, Whirlpool CoinJoin integration (where available), advanced coin control | Optional (proxy/Tor; can auto-start internal Tor for onion servers) | Yes | Yes | No | Free | Power users, UTXO management |
| Cake Wallet | Software | XMR (+BTC/LTC/etc.) | Monero-first defaults (subaddresses, etc.) | Optional (Tor via Orbot; built-in Tor in some versions) | N/A (chain-specific) | Yes | No | Free | Monero-first mobile privacy |
| Samourai Wallet (historical) | Software | BTC | Whirlpool (CoinJoin), Dojo server model | Yes | Yes (via Dojo) | Yes (client repos) | No | Free (project shut down after 2024 enforcement action) | Historical context for BTC privacy tooling |
| Exodus Wallet | Software | Multi | Limited (no built-in mixing) | No | No | Partial | No | Free | Beginners, convenience |
| ZenGo Wallet | Software | Multi | MPC-based custody model (privacy trade-offs) | No | No | No | No | Essentials: Free • Pro: $9.99/month or $49.99/year | Mobile-first security model |
| Ledger Wallets (multiple models) | Hardware | Multi | Depends on wallet stack (e.g., coin control via paired apps) | Depends | Depends | Partially | No | Varies by model/region/promotions (check official store) | Long-term key security (wide ecosystem) |
| Trezor Wallets (multiple models) | Hardware | Multi | Depends on wallet stack | Depends | Depends | Yes | No | Via Trezor Shop: Safe 3 €59, Safe 5 €129 | Open-source leaning security, backups |
| ELLIPAL Titan 2.0 | Hardware | Multi | Air-gapped signing (QR) | Depends | Depends | Mixed | No | Varies (often listed around $169) | Air-gapped isolation |
| BitBox02 | Hardware | BTC / Multi | Lean stack; Bitcoin-only option | Depends | Depends | Yes | No | Varies (often listed around $176) | Minimalist long-term holding |
| Electrum | Software | BTC | Server control, strong coin control | Yes | Yes (via your server) | Yes | No | Free | Advanced BTC configuration |
How We Tested These Anonymous Wallets
Privacy features
We evaluated whether each wallet actually reduces linkability, not just whether it’s “no-KYC.” This included coin control/UTXO tools (for Bitcoin), support for privacy workflows like CoinJoin or PayJoin, Tor/proxy options, full-node connectivity, and how much metadata the default setup can leak through servers, integrations, or broadcast paths.
Ease of use
We looked at how easy it is to use the wallet without accidentally undoing your privacy. That means checking how clearly the wallet explains what’s happening, whether privacy-critical settings are discoverable, and how often the UI nudges users into risky behavior (like address reuse, UTXO merging, or convenience swaps that add extra tracking surface).
Security architecture
We assessed how keys are generated, stored, and used, plus the recovery model and common failure points. For hardware wallets, we focused on signing isolation and backup options (PIN/passphrase, Shamir-style recovery where relevant). For software wallets, we weighed device risk, phishing exposure, and whether features like MPC meaningfully change the theft/recovery trade-off.
Community trust
We checked the wallet’s reputation in the security and privacy community, the transparency of documentation, and whether past issues were handled responsibly. Open-source availability, audit history (where applicable), and the project’s willingness to explain trade-offs clearly were treated as trust signals.
Active development
We prioritized wallets that are actively maintained and updated. We considered release cadence, responsiveness to bugs and security disclosures, and whether the project still looks “alive” in practice, because stale wallets become soft targets, especially in privacy tooling where threats and surveillance techniques keep evolving.
Understanding Crypto Privacy (Anonymous vs Pseudonymous)
A public blockchain is like a glass building. You might not know who anyone is, but you can still follow their movements. A wallet address is just a badge number. If someone ever matches that badge to you, tracing your past activity and your future transactions becomes much easier.
Pseudonymous vs Truly Anonymous Transactions
Bitcoin address tracking
Bitcoin transactions live on a public ledger. The original design assumes people will use new addresses to reduce linkability, but it also acknowledges that linking can still happen in practice. In other words, Bitcoin is pseudonymous: your identity isn’t printed on-chain, but your activity can often be connected through patterns.
Even if you use fresh addresses, common spending behaviors can connect them over time, including:
- Address reuse, which turns one-off activity into a readable “account history.”
- Change outputs, where wallets send leftover funds back to a new address you control (often a big clue when analyzing flows).
- UTXO spending patterns, like consolidating many small inputs into one transaction, which can look like “one person cleaning up their wallet.”
Check out our guide on Bitcoin.
Blockchain analysis and clustering
Blockchain analysis doesn’t always need names. It often relies on probability and heuristics, rules of thumb that tend to be true often enough to be useful. Academic research has shown how addresses can be clustered into likely “entities,” especially when multiple inputs are spent in the same transaction (a classic example is A Fistful of Bitcoins).
Important caveat: clustering is not perfect. But “not perfect” is still enough to build profiles, flag activity, or narrow down suspects when combined with exchange records, IP logs, or known labeled addresses.
How Blockchain Transparency Impacts Privacy
Public ledger trade-offs
Transparency is a feature, not a bug. It lets anyone:
- Audit supply and issuance.
- Verify payments without trusting a bank.
- Independently validate balances and transfers.
The downside is that the same transparency creates an extremely rich dataset for monitoring behavior over time.
Why explorers are surveillance tools
Block explorers are convenient, but they also make on-chain analysis easy for anyone, not just professionals. They can simplify the steps of:
- Following funds across multiple hops.
- Labeling addresses and sharing those labels.
- Comparing transaction histories across wallets.
“Non-KYC” does not automatically mean “private.” On-chain patterns can still be linked to you through behavior, counterparties, or off-chain metadata.
Privacy-Enhancing Technologies Explained
This section explains what privacy wallets can do under the hood, and what they can’t do for you.
 Privacy Wallets Use Powerful Cryptography To Hide Transaction Details, But They Can't Bypass Real-world Kyc Regulations, Tax Laws, Or User Operational Errors.
Privacy Wallets Use Powerful Cryptography To Hide Transaction Details, But They Can't Bypass Real-world Kyc Regulations, Tax Laws, Or User Operational Errors.CoinJoin and WabiSabi Protocol (Wasabi)
Automated Mixing
CoinJoin lets multiple people share a single Bitcoin transaction. Instead of each person broadcasting a separate payment, everyone pools their inputs and outputs together. If it’s done properly, it becomes much harder to match a specific input to a specific output with confidence.
A useful mental model is a coat-check system:
- Everyone hands in a coat at the same time.
- Everyone gets a ticket.
- Later, coats are returned, but an outside observer has a harder time matching which person handed in which coat, because everything happened as one group.
Sybil Resistance Improvements
Wasabi’s newer CoinJoin design is built around WabiSabi, an anonymous credential scheme that enables variable-amount CoinJoins (so participants aren’t forced into rigid, fixed denominations) and is designed to limit what a centralized coordinator can learn during a round. For the most detailed technical explanation, the WabiSabi: Centrally Coordinated CoinJoins with Variable Amounts paper lays out the protocol mechanics and privacy properties. If you want the practical “how it works in the wallet” view, Wasabi’s CoinJoin documentation walks through the user-facing flow and the main stages of a round.
Ring Signatures and RingCT (Monero)
Plausible deniability explained
Monero hides the real signer among a group. A ring signature proves “someone in this set signed,” without proving who.
RingCT extends this by hiding transaction amounts, so observers cannot simply follow “same-sized” payments through the graph.
Check out our primer on Monero.
zk-SNARKs (Zcash Shielded Pools)
Zcash supports transparent and shielded transfers.
With transparent transfers, nothing is hidden. Anyone can view the addresses involved and the amount. That’s often the easier route for day-to-day use, especially when sending to services that expect fully public transactions.
Shielded transfers are built for privacy. They use zero-knowledge proofs, which let the network confirm a transaction is valid without exposing the key details (like who sent it, who received it, or how much was moved, depending on the transaction type).
In other words, transparent is public-by-default, while shielded is privacy-first when you need it.
Read: What is Zcash?
PayJoin (P2EP)
PayJoin is a two-party payment where the receiver contributes an input, making the final transaction look less like a standard “one person paid another” pattern.
Many heuristics assume all inputs belong to the sender. PayJoin breaks that assumption by design.
Coin Control and UTXO Management
When you spend Bitcoin, you are really spending UTXOs. If you mix “public” coins (linked to your identity) with “private” coins in the same transaction, you can undo a lot of work in a single click.
Coin control lets you choose which UTXOs to spend, helping you avoid address clustering and accidental merging of identities. Sparrow’s privacy guide is one of the clearest practical walk-throughs.
Subaddresses and Stealth Addresses
A common privacy failure is address reuse. Some systems reduce this risk by default.
- Monero subaddresses help you generate many receiving addresses under one wallet without obvious on-chain linkage.
- “Stealth address” ideas also exist in other ecosystems, but the details vary widely. The important habit is the same: minimize reuse and separation mistakes.
Tor and I2P Routing
Even if your on-chain footprint is clean, your network footprint can betray you.
How wallets hide your IP address
Tor routes traffic through multiple relays, so the destination does not learn your real IP.
I2P is a different anonymity network that uses “garlic routing,” bundling messages to complicate traffic analysis.
Full Node vs SPV Wallet Privacy
Why SPV leaks metadata
Light wallets often ask servers for information about your addresses. That can leak what you own, when you transact, and how your wallet behaves. Older SPV approaches using Bloom filters have well-known privacy weaknesses.
If privacy is a priority, pairing a wallet with your own full node usually reduces metadata exposure, even if it adds setup work.
Lightning Network Privacy (Dandelion++, onion routing)
Lightning improves privacy in some ways, but it is not “invisible money.”
- Onion routing on Lightning: Payment routing uses onion packets so intermediate nodes only learn what they need to forward the payment.
- Why LN is not fully private: Channel openings and closings are on-chain, routing can leak timing and liquidity signals, and the network has its own metadata layer.
- Dandelion++ note: Dandelion++ is a transaction broadcast privacy proposal that aims to reduce IP-based deanonymization for on-chain transactions. The formal paper is Dandelion++. It is best thought of as network-layer privacy research, not a magic switch most Bitcoin wallets can “turn on” today.
See which coins we chose as the best privacy coins.
Top Anonymous Crypto Wallets Reviewed (2026 Edition)
Below is a standardized review format for each wallet. “Privacy Score” is a practical, subjective score (1–10) based on default network privacy, metadata leakage risk, coin control, and available privacy tooling. It is not a guarantee of anonymity.
1. Wasabi Wallet
Quick stats
- Platform: Desktop
- Price: Free
- Chains: Bitcoin
- Privacy score: 8.5/10
Overview
Wasabi is a Bitcoin wallet built around CoinJoin. Its strongest feature is that privacy tooling is first-class, not hidden in advanced menus.
Privacy features
- WabiSabi CoinJoin: CoinJoin implementation designed to make collaborative transactions more practical.
- Tor by default: Routes network connections through Tor to reduce metadata leakage.
- Coin control: Helps avoid common linkability traps when selecting UTXOs.
Security features
- Non-custodial keys: You control your private keys.
- Safe defaults: Emphasizes guardrails around privacy workflows.
Supported coins
Bitcoin only.
Who it’s for
Bitcoin users who want practical privacy without building a highly customized setup.
Pros & cons
Pros
- Privacy features are central, not optional extras.
- CoinJoin is integrated into the normal workflow.
Cons
- CoinJoin has costs and takes time.
- You still need discipline, especially after mixing, to avoid re-linking coins.
Our verdict
Wasabi is one of the most straightforward ways to improve Bitcoin transaction privacy, as long as you treat it like a process, not a button.
2. Sparrow Wallet
Quick stats
- Platform: Desktop
- Price: Free
- Chains: Bitcoin
- Privacy score: 9/10
Overview
Sparrow is a power user wallet. It shines when you care about coin control, PSBT workflows, and full-node connections.
Privacy features
- PayJoin support: Supports BIP78 PayJoin (Bitcoin Optech tracks Sparrow’s PayJoin support on its PayJoin topic page).
- Whirlpool CoinJoin support (where available) + coin control: Earlier Sparrow versions integrated the Whirlpool client, but this was removed in Sparrow v1.9.0. If you’re using a setup that still supports Whirlpool, pair it with Sparrow’s coin control and UTXO labeling to keep “clean” and “linked” coins separated.
- Full node integration options: You can connect to your own Bitcoin Core node for more private wallet operation (connect to Bitcoin Core).
- Advanced UTXO labeling and coin control: Built around visibility and deliberate UTXO selection (feature overview).
Security features
- Hardware wallet integration: Works well with Coldcard.
- PSBT support and detailed previews: Transaction construction and review are first-class (BIP174 PSBT format).
Supported coins
Bitcoin only.
Who it’s for
People who want control, run a full node, or actively manage privacy boundaries.
Pros & cons
Pros
- Best-in-class UTXO management.
- Excellent for separating identities and managing “clean” vs “linked” coins.
Cons
- More knobs means more ways to make a mistake if you rush.
- Setup is heavier than beginner wallets.
Our verdict
Sparrow is one of the most capable Bitcoin desktop wallets for privacy-heavy workflows, but it expects you to learn the basics properly.
3. Cake Wallet (Monero-Focused)
Quick stats
Overview
Cake Wallet is known for making Monero usable on mobile without turning privacy into a research project.
Privacy features
- Monero-first defaults: Practical privacy-forward UX for common Monero workflows.
- Tor support (via Orbot): Can route wallet connections through Tor using Orbot (setup guide).
- Subaddress handling: Encourages safer receiving practices that reduce address reuse mistakes.
- Day-to-day guardrails: Settings and design choices aim to reduce accidental privacy foot-guns on mobile.
Security features
- Non-custodial seed control: You control the wallet keys and recovery phrase.
- Open-source availability: Public codebase is available (GitHub repo).
Supported coins
Monero, plus additional assets depending on version and integrations.
Who it’s for
Monero users who want practical privacy on a phone, with fewer sharp edges.
Pros & cons
Pros
- Strong privacy by default when using Monero.
- Easier for day-to-day use than most privacy tools.
Cons
- Mobile devices add risk: malware, backups, and screen capture threats.
- Extra features like swaps can introduce metadata and counterparty exposure.
Our verdict
For Monero-centric privacy on mobile, Cake is one of the most usable options available.
4. Samourai Wallet (Discontinued)
Quick stats
- Platform: Android (historical; app no longer maintained)
- Price: Free
- Chains: Bitcoin (BTC)
- Privacy score: N/A
Overview
Samourai was a major influence on Bitcoin privacy culture, particularly around mixing, UTXO hygiene, and adversarial thinking.
Whirlpool mixing
Samourai popularized Whirlpool-style mixing workflows and strong privacy messaging (see the project’s historical tooling and docs, such as Whirlpool).
Legal and regulatory status note
In April 2024, US authorities charged Samourai Wallet’s founders with money laundering conspiracy and operating an unlicensed money transmitting business, per the official Department of Justice announcement. In August 2025, IRS-CI stated the founders pleaded guilty (see the IRS-CI release). They were later sentenced (Nov 19, 2025; see the IRS-CI sentencing release).
Supported coins
Bitcoin only.
Why it still matters historically
Even if you never used Samourai, many privacy practices discussed today—like strict coin separation, adversarial threat modeling, and “don’t trust defaults”—were pushed into the mainstream partly through its influence.
Our verdict
Samourai’s importance is mainly historical now: it helped shape modern Bitcoin privacy thinking, but functionality and access may vary due to enforcement actions and shutdown.
5. Exodus Wallet
Quick stats
- Platform: Desktop and Mobile
- Price: Free
- Chains: Multi-chain
- Open source: Partial (Exodus terms)
- Privacy score: 4/10
Overview
Exodus is a polished, beginner-friendly wallet. It is not built as an anonymity tool, but many people start here and later care about privacy.
Privacy features
- Dedicated privacy tooling is limited: It’s not designed to minimize metadata in the way privacy-first wallets do.
- Privacy depends on your integrations: Your exposure changes based on third-party services you use and how you manage addresses and UTXOs.
- Policy-level transparency: Exodus documents data handling in its Privacy Policy and discusses information access in Legal Inquiries.
Security features
- Non-custodial wallet design: You control keys locally.
- Strong usability: Smoother UX can reduce beginner mistakes, even if it doesn’t add anonymity.
Supported coins
Broad multi-chain support.
Who it’s for
Beginners who want a simple interface and are not ready for privacy-heavy workflows yet.
Pros & cons
Pros
- Easy onboarding.
- Helpful UX for learning basics.
Cons
- Not designed to minimize metadata exposure like privacy-first wallets do.
- Convenience features can increase privacy risk.
Our verdict
Exodus is approachable, but it should not be mistaken for an anonymity solution.
6. ZenGo Wallet
Quick stats
- Platform: Mobile
- Price: Free (Essentials); $9.99/month or $49.99/year (Pro)
- Chains: Multi-chain
- Open source: No (app/server); some MPC components open (source, GitHub)
- Privacy score: 5/10
Overview
ZenGo is known for MPC-style key management, which changes the risk profile of key theft and seed phrase handling.
Privacy features
- MPC isn’t on-chain privacy: It can reduce certain seed-related risks, but it does not automatically improve transaction privacy.
- Metadata still matters: The network you use, services you connect, and how the app communicates can still expose patterns.
Security features
- MPC-based custody model: Designed to reduce single points of failure compared to classic single-key setups.
- External audits: ZenGo states it performs formal/external audits and highlights audits and security posture in its security materials (security overview).
Supported coins
Multi-chain.
Who it’s for
Users who prioritize mobile convenience and want alternatives to classic seed phrase custody.
Pros & cons
Pros
- Different security model that can be attractive for mobile-first users.
- Seed phrase handling is not the same as typical wallets.
Cons
- Privacy is still mostly about transaction behavior and network choices.
- You must understand what MPC does and does not do.
Our verdict
ZenGo is interesting for key security, but it is not a privacy wallet by design.
7. Ledger Wallets
Quick stats
- Platform: Hardware + companion apps
- Price: Varies by model, region, and promotions; check the official Ledger store.
- Chains: Multi-chain via apps
- Privacy score: 6/10 (depends heavily on your software stack)
Overview
Ledger devices are widely used hardware wallets. They primarily protect keys offline, which is a security benefit. Privacy is more complicated.
Privacy features
- Hardware security isn’t privacy: Protecting keys offline does not hide your on-chain footprint.
- Companion software metadata: Using Ledger Live and integrated services can create extra metadata, as described in Ledger’s Privacy Policy and the Ledger Live tracking policy.
Security features
- Secure element-based architecture: Designed to keep signing keys isolated from internet-connected devices.
- Hardware isolation: Helps reduce risk from many desktop malware threats.
Supported coins
Very broad via device apps and third-party wallets.
Who it’s for
Long-term holders who want offline key protection and are willing to think carefully about the software layer.
Pros & cons
Pros
- Strong key security for long-term storage.
- Works with many third-party wallets, which can improve privacy if you choose the right stack.
Cons
- Companion app metadata is a real consideration.
- Some parts of the ecosystem are not fully open-source (see Ledger’s approach to open source).
Our verdict
Ledger can be a solid security tool, but privacy depends on how you broadcast transactions and what services you connect.
8. Trezor Wallets
Quick stats
- Platform: Hardware + companion app
- Price: Varies by device (e.g., Safe 3 €59, Safe 5 €129; prices shown in EUR and may vary by region/promotions).
- Chains: Multi-chain (and Bitcoin-only options)
- Privacy score: 7/10 (stronger transparency; still depends on network choices)
Overview
Trezor is known for its open-source approach and clear documentation.
Privacy features
- Third-party wallet compatibility: A privacy win if you avoid leaky defaults and choose a privacy-aware software stack.
- Transparency emphasis: Open-source software can make verification and auditing more approachable (see Security and safety in Trezor).
Security features
- Hardware isolation: Keeps signing keys off your everyday computer or phone.
- Transparent software philosophy: Strong documentation around threat modeling and safe use.
Supported coins
Broad support depending on model and software.
Who it’s for
People who value transparency and want strong key security without locking into a single software ecosystem.
Pros & cons
Pros
- Open-source advantage.
- Clear security guidance.
Cons
- Like all hardware wallets, it does not hide your on-chain footprint by itself.
- Your privacy is still defined by your transaction patterns and node setup.
Our verdict
Trezor is a strong option for security-conscious users who also care about verifiability.
9. ELLIPAL Wallet
Quick stats
- Platform: Hardware (air-gapped)
- Price: Listed around $169 for Titan 2.0 (at time of writing) (pricing varies by bundle and promotions).
- Chains: Multi-chain
- Privacy score: 7/10
Overview
ELLIPAL emphasizes air-gapped signing, avoiding USB and Bluetooth connectivity for the signing device.
Privacy features
- Air-gapped operation: Reduces certain attack surfaces by keeping the signing device off direct network connections.
- QR-based signing: The signing device is not directly network-connected, which can reduce some metadata leakage opportunities.
Security features
- Strong physical separation: Designed to keep key operations away from networked devices.
- QR signing workflow: Uses camera scanning instead of cables/wireless links for signing.
Supported coins
Broad support (varies by firmware and companion app).
Who it’s for
People who want strong device isolation and prefer QR signing over cables and wireless.
Pros & cons
Pros
- Excellent isolation from common connection-based attacks.
- Simple “camera scan” workflow.
Cons
- Privacy still depends on how the companion app connects and broadcasts.
- Air-gapped does not automatically mean anonymous on-chain behavior.
Our verdict
ELLIPAL is a strong air-gapped option, especially for users who prioritize physical separation.
10. BitBox Wallet
Quick stats
- Platform: Hardware
- Price: BitBox02; BitBox02 Nova
- Chains: Bitcoin-only or multi-coin editions
- Privacy score: 7/10
Overview
BitBox02 is a minimalist hardware wallet with a “keep it simple” philosophy and strong security design choices.
Privacy features
- Best with your own stack: Works best when paired with privacy-friendly wallets and your own node.
- Bitcoin-only firmware option: Can reduce complexity and attack surface (Bitcoin-only vs multi-coin explanation).
Security features
- Dual-chip architecture: Aims for strong physical and logical protections.
- Designed for straightforward recovery: Focus on simple backups and recovery flow.
Supported coins
Depends on edition: Bitcoin-only vs multi-coin firmware choices.
Who it’s for
People who want a simple, security-first hardware wallet and plan to use a privacy-aware setup.
Pros & cons
Pros
- Minimalist hardware with a strong security story.
- Bitcoin-only option for simpler threat surfaces.
Cons
- Privacy comes from your software and network choices.
- Features are intentionally focused, not “everything in one app.”
Our verdict
BitBox02 is a clean, minimalist pick for users who want fewer moving parts.
11. Electrum Wallet
Quick stats
- Platform: Desktop (and some mobile forks exist)
- Price: Free
- Chains: Bitcoin
- Privacy score: 7.5/10 (high ceiling, depends on configuration)
Overview
Electrum is one of the oldest Bitcoin wallets still widely used. It is flexible, scriptable, and can be configured for privacy, but defaults matter.
Privacy features
- Tor support: Official guidance is available for routing Electrum through Tor (Using Electrum through Tor).
- Server selection: You can choose which servers to use, reducing metadata leakage when configured carefully.
- Coin control: Useful tools for managing UTXOs and avoiding accidental linkability (when used properly).
Security features
- Mature codebase: Longstanding wallet with broad ecosystem support.
- Hardware wallet compatibility: Common hardware wallets integrate well for signing flows.
- Transaction construction control: Strong control over how transactions are built and signed.
Supported coins
Bitcoin only.
Who it’s for
Experienced users who want control over servers, signing flows, and transaction construction.
Pros & cons
Pros
- Powerful and configurable.
- Good building block for privacy-aware setups.
Cons
- Misconfiguration can leak metadata.
- Not beginner-friendly compared to modern UX wallets.
Our verdict
Electrum is a strong choice if you configure it carefully and understand how server connections affect privacy.
What Makes a Crypto Wallet Truly Anonymous?
“Truly anonymous” is a high bar. Most wallets can only reduce risk. Your real goal is usually “harder to link,” not “impossible to trace.”
Non-Custodial vs Custodial
Non-custodial means you control the private keys. In practical terms, that means you’re not relying on a third party to approve withdrawals or “hold” your funds on your behalf. It also reduces certain privacy risks, because there’s no single platform automatically seeing your balances, your full transaction history, and where you send funds.
Custodial platforms are the opposite. If a service holds the keys, it can typically see:
- Your balances and internal transfers.
- Deposit and withdrawal addresses.
- Timing, amounts, and counterparties.
- Often your identity, especially if the service uses KYC.
That doesn’t make custodial wallets “bad” by default, but it does mean you’re trading control and privacy for convenience.
End-to-End Encryption
Encryption helps protect what’s stored on your device and, in some cases, what your wallet sends and receives.
But it does not make your transactions private on-chain. Once a transaction hits a public blockchain, the details are still visible. Encryption helps with device and network security, not with hiding activity on the ledger.
No-KYC Requirements
“No-KYC” simply means a wallet didn’t ask for your passport or proof of address. That can be useful, but it’s not the same thing as privacy.
A wallet can be “no-KYC” and still leak metadata through:
- The servers it connects to.
- Embedded analytics or telemetry.
- Swap, buy, or bridging integrations.
- Default settings that reveal address relationships over time.
A wallet can be no-KYC and still give you away through patterns, servers, or the services it plugs into.
Decentralization and Censorship Resistance
The easiest places to monitor are the big central services. Using your own node and fewer integrations gives you less surface area. It means fewer third parties get to see your IP, your balances, your transaction history, or your timing. It also reduces the number of “extra” services in your wallet that can log activity, phone home, or add their own trackers. In short, the more you self-host and keep things simple, the fewer places there are for your data to leak.
Privacy Hygiene: Essential Practices
If you only take one section seriously, make it this one.
 Privacy Tools Fail Without Discipline
Privacy Tools Fail Without DisciplineAddress Management Rules
- Never reuse addresses.
- Separate identities. One persona, one wallet cluster.
- Treat public donations, social posts, and on-chain proofs as permanent identity anchors.
Coin Control and Coin Separation Strategies
- Keep “public” UTXOs separate from “private” UTXOs.
- Label coins by source. KYC exchange, salary, mining, P2P, mixed, and so on.
- Never merge categories casually.
Network Privacy (Tor vs VPN)
- A VPN can hide your IP address from the site or service you are connecting to, but it shifts trust to the VPN provider, which can still see your connection details.
- Tor spreads trust across relays and is designed specifically for anonymity, as described in the Tor design specification above.
- VPN can be useful, but VPN alone is not a privacy finish line.
Full Node Usage
Running your own full node reduces the need to ask third parties what your wallet owns. It can also reduce server-side metadata leakage that many light wallets risk.
Verification Practices
- Verify downloads with vendor signatures when possible.
- Prefer reproducible builds when projects support them.
- Avoid “random mirror” downloads and unofficial app stores.
Common Privacy Mistakes
- KYC exchange leaks: The moment you withdraw to a known address, linkage risk rises.
- Dust attacks: Tiny incoming UTXOs can be used to trick you into merging identities.
- Timing correlation: Repeating patterns and consistent schedules can leak identity even without KYC.
Privacy Coins and Wallets in Today’s Regulatory Landscape
The annoying part is that privacy tools are often the first to face pressure.
Exchange Restrictions on Monero and Zcash
Many regulated exchanges limit privacy coin support in some regions. The practical outcome is that on-ramps and off-ramps can become the weak link in a privacy plan.
FATF Travel Rule and Chain Surveillance
The FATF’s updated guidance on virtual assets pushes regulated entities toward stronger identity collection and information sharing between service providers.
Monero 51% Attack (2025) and What It Means
In August 2025, the Monero network faced a period of serious hashrate-concentration concerns linked to Qubic’s mining campaign, which was publicly marketed as a “51% takeover” attempt. Researchers later analyzed the episode in Inside Qubic’s Selfish Mining Campaign on Monero and concluded that, despite the alarming framing, there was no sustained 51% control observed (the campaign’s hashrate share was reconstructed as rising into the ~23–34% range across identified intervals).
Around the same time, Kraken temporarily paused and/or delayed Monero funding operations, citing “significant consolidation of hash rate under a single entity” in its official incident report Monero (XMR) Funding Delays.
The privacy lesson is straightforward: Strong on-chain privacy doesn’t eliminate consensus-layer risks. If confirmations become unreliable or exchanges raise confirmation requirements during security scares, your real-world security (and ability to transact on time) can still take a hit, even if the chain does an excellent job hiding amounts and addresses.
Jurisdictional Differences (EU, US, APAC)
- EU: The EU’s crypto markets framework is codified in Regulation (EU) 2023/1114 (MiCA). Privacy coin policy can still vary by local enforcement and exchange licensing choices.
- US: US guidance around “money transmission” and compliance obligations is shaped by documents like FinCEN’s 2019 guidance on convertible virtual currency.
- APAC: Rules vary widely by country. The practical pattern is that regulated on-ramps typically collect more identity data, which raises linkage risk.
Matching Privacy Tools to Your Threat Model
Privacy without a threat model becomes expensive and confusing fast.
Corporate Surveillance (Data Brokers, Exchanges)
- Goal: Reduce identity linkage.
- Recommended wallets and tools: Use Sparrow or Wasabi for BTC privacy workflows, and minimize reuse and merging. Consider hardware wallets for storage, but avoid data-heavy companion apps when possible.
Blockchain Analytics Firms (Chainalysis, TRM)
- Goal: Break common heuristics and reduce graph linkability.
- Recommended wallets and tools: Sparrow for strict UTXO control and PayJoin. Wasabi for CoinJoin workflows. Monero via Cake if your goal is privacy by protocol design. Treat every “bridge” back to Bitcoin or fiat as a surveillance hotspot.
Government Surveillance
- Goal: Assume strong capabilities, including subpoenas and exchange records.
- Recommended wallets and tools: Avoid centralized services whenever practical. Use non-custodial wallets, strict coin separation, Tor routing, and consider a full-node setup. For high-risk models, hardware wallets reduce theft risk, but they do not solve metadata issues.
Physical Security Threats
- Goal: Prevent theft, coercion, and device compromise.
Recommended wallets and tools: Hardware wallets are for not getting robbed by a bad day. Trezor, Ledger, and BitBox keep your keys off the device you browse and download on. ELLIPAL goes further by staying air-gapped and using QR signing instead of cables or wireless. Use a passphrase, store backups like they matter, and do not carry large balances on a phone.
How to Choose an Anonymous Crypto Wallet
Choosing an anonymous crypto wallet comes down to how much privacy you actually need and what you’re willing to trade for it, like convenience, recovery options, and ease of use.
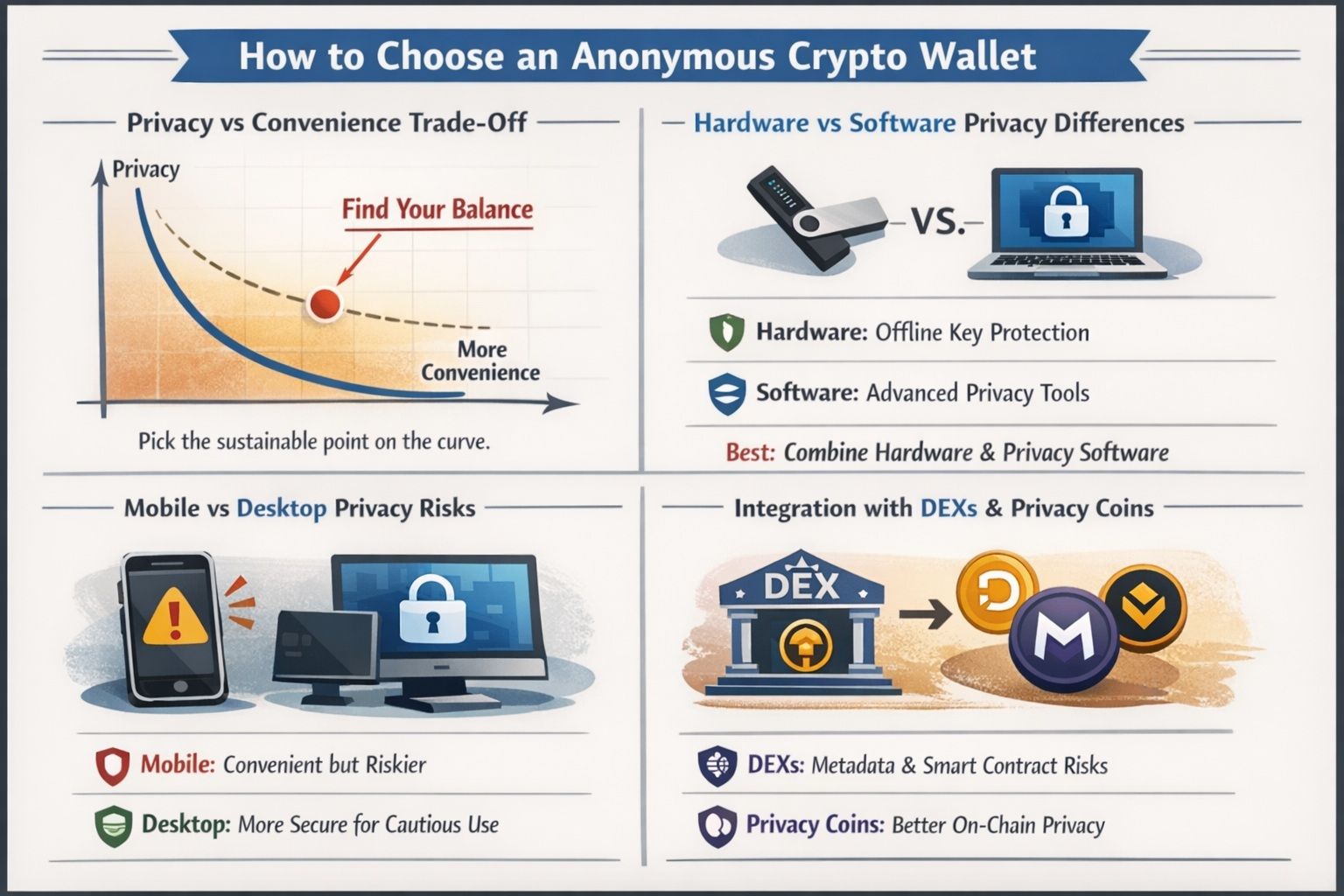 Choosing An Anonymous Crypto Wallet Means Trading Convenience For Privacy Features
Choosing An Anonymous Crypto Wallet Means Trading Convenience For Privacy FeaturesPrivacy vs Convenience Trade-Off
Convenience usually increases metadata exposure. Privacy usually adds steps. Pick the point on that curve you can sustain without cutting corners.
Hardware vs Software Privacy Differences
- Hardware wallets protect keys offline.
- Software wallets can offer more privacy tooling for transaction construction.
- The best setups often combine both, hardware for signing, privacy-aware software for constructing and broadcasting.
Mobile vs Desktop Privacy Risks
Mobile is convenient but riskier. Backups, app permissions, and device compromise are more common. Desktop can be safer for careful workflows, especially when paired with your own node.
Integration with DEXs and Privacy Coins
DEX integrations can introduce both metadata exposure and smart contract risk. Privacy coins can improve on-chain privacy, but they may be harder to acquire or spend depending on regulations and which exchanges or services support them.
How to Acquire Crypto Without KYC
This is about minimizing unnecessary data sharing where legal, not bypassing obligations. Laws and compliance obligations vary by country and can change quickly. Don’t use “no-KYC” routes to evade legal requirements (tax reporting, sanctions rules, local licensing, or AML laws).
P2P Platforms (Bisq, LocalMonero)
- Bisq is designed for peer-to-peer Bitcoin trading without registration, and describes itself as a decentralized exchange.
- LocalMonero historically filled a similar role for Monero, but the platform announced it was winding down on May 6, 2024, with a shutdown timeline and eventual takedown (see the notice on LocalMonero’s site).
No-KYC Onramps (Silent.link, BTC ATMs)
Bitcoin ATMs vary by operator and jurisdiction. Many require ID above certain limits, and policies can change quickly. Treat them as “sometimes less KYC,” not “no KYC.”
Some services are not onramps, but can help reduce network-level identity signals (like SIM-linked identity or connectivity metadata). Silent.link fits here: it’s a connectivity/eSIM service that markets a “zero KYC policy,” not a fiat-to-crypto ramp.
DEX Alternatives
DEXs can reduce centralized exchange exposure for crypto-to-crypto swaps, but they usually do not solve fiat onboarding. Also, DEX use can still be traceable on transparent chains unless you use privacy-preserving assets and strong hygiene.
Security Best Practices for Anonymous Wallet Users
- Private key management: Keep the recovery phrase off the internet. Paper or metal backup, stored somewhere safe. Do not put it in iCloud/Google Drive, notes apps, screenshots, or email.
- 2FA: Lock down your email first. If someone gets your email, they can usually reset everything else. Use app-based 2FA or a hardware key, not SMS when possible.
- Password hygiene: Unique passwords, password manager, and no reuse.
- Phishing: Verify domains, avoid random “wallet support” links, and be skeptical of urgent messages.
- Keep wallets updated, but verify downloads where possible.
Final Verdict: Which Anonymous Wallet Should You Use?
Beginners
Start with usability, then add privacy structure. Exodus can help you learn basics, but move to Sparrow or Wasabi when privacy becomes a real requirement.
Privacy maximalists
For Bitcoin, Sparrow plus a full node and strict UTXO discipline is hard to beat. For protocol-level privacy, Monero via Cake is often more forgiving, but pay attention to network health and off-ramp constraints.
Long-term holders
Start with a hardware wallet so your keys are not living on a laptop or phone. Trezor is the open-source pick, Ledger is the “works with everything” pick, BitBox02 is the minimalist pick, and ELLIPAL is for people who want QR signing with an air-gapped device. From there, focus on the wallet software and node setup you use to send transactions, because that’s where most privacy leaks happen.
Power users
Sparrow is the workhorse. Pair it with your node, learn coin control properly, and use PayJoin or CoinJoin workflows without undoing them later through sloppy merges.





