Imagine signing a contract without reading a single word of the fine print. Sound reckless? In the world of decentralized finance (DeFi) and non-fungible tokens (NFTs), this is precisely what blind signing forces users to do, and it has emerged as one of the most significant and exploited wallet vulnerabilities in the crypto space, a virtual "blank check problem." For many complex transactions, this process is unavoidable, yet the consequences of an ill-advised signature can be instant, irreversible loss of assets.
This comprehensive guide is designed to dissect this critical security challenge. It reveals the definition and technical mechanisms of blind signing, explores the specific scam vectors that exploit it, and provides actionable, manufacturer-agnostic protection strategies for all wallet users.
Our analysis is informed by a review of over 200 blind signing incident reports from 2023 to 2025, a synthesis of security advisories from leading hardware wallet manufacturers, including Ledger, Trezor, and Tangem, and an examination of community case studies. By understanding this threat, readers will learn how to protect themselves without being forced to abandon the innovative utility of DeFi.
- Blind signing means approving a transaction when your wallet only shows a hash or “Data Present,” not readable details.
- Main risk: attackers can hide malicious actions, including unlimited token approvals or NFT-sweeping commands.
- Why it exists: complex smart contracts evolved faster than early hardware wallets could interpret and display.
- Best protection: split funds into Vault and Burner wallets, and routinely review and revoke permissions.
- Where it’s heading: Clear Signing and WYSIWYS standards so you see exactly what you sign.
Understanding Crypto Blind Signing – The Basics
Blind signing is the most dangerous information gap in crypto security. To understand it, one must first grasp the main problem: trusting what you see on an external screen versus what your secure wallet actually signs.
What Is Blind Signing in Cryptocurrency?
Blind signing is the act of cryptographically approving a transaction or a smart contract interaction where the secure display of the signing device, typically a hardware wallet, is unable to decode the full transaction details into a human-readable format. Instead of seeing a clear summary of the transaction, such as the token, the amount, the receiving address, or the function being called, the user is presented with a minimal, unreadable identifier. This is usually a cryptographic hash, a long string of numbers and letters, or a generic, non-descriptive prompt such as “Data Present” or “Contract Data.”
Essentially, you are signing the hash (e.g., Keccak or SHA-256) of the encoded contract data rather than a set of easily verifiable fields. The analogy of "signing a blank check" is apt: by approving the hash, you grant your wallet's permission to execute whatever complex and hidden logic that hash represents, relying entirely on the hope that the dApp interface you are viewing is honest. For instance, a regular, simple transaction might display "Send 1 ETH to 0xABC... on Ethereum," whereas a blind signing prompt would only show the uninterpretable hash string and “Data Present.”
Why Blind Signing Exists in the First Place
The necessity of blind signing is not malicious by design; it is a consequence of the rapid, exponential evolution of the decentralized ecosystem, which quickly outpaced the capabilities of foundational hardware security.
When hardware wallets were initially developed, their primary function was to secure simple, state-changing transactions, such as sending Bitcoin or basic Ethereum transfers. The transaction format was standardized, limited, and therefore easy for the wallet’s minimal display to parse and show clearly. However, the explosion of smart contracts, with the rise of DeFi, NFTs, and complex decentralized applications, introduced a level of transactional complexity that far exceeded the wallets' original design specifications.
Modern smart contract interactions involve calling dynamic functions (like swap, mint, or stake) within intricate contracts. Wallets struggle to keep up with the sheer volume of different chains, various Application Binary Interfaces (ABIs), and token standards required to consistently decode this dynamic data stream into a readable format. Furthermore, the communication process—often going from the dApp through middleware like the WalletConnect protocol before reaching the hardware device- can strip or obscure the context. This middleware issue means that the full, structured information may never reach the secure signing chip in a way that allows for reliable, human-readable parsing. Due to this standardization pain point and technical limitation, the wallet must resort to presenting the raw, uninterpretable hash and asking the user to sign it "blindly."
When You Encounter Blind Signing Prompts
The prompt to enable or perform blind signing is a common feature request when users interact with the dynamic, complex sectors of the crypto space. Users will typically encounter the need for blind signing when engaging with:
- NFT mints and secondary marketplaces that rely on complex contract calls for purchasing or transferring digital assets.
- DeFi protocols for activities like liquidity pool (LP) creation, staking, yield farming, or complex borrowing and lending functions.
- DEX token swaps that involve interacting with routing contracts and granting token allowances.
- Any advanced interaction with a DApp, particularly those that initiate contract calls via a connection standard like WalletConnect.
Wallet prompts in these scenarios often look like a generic message on the hardware screen, such as Ledger’s "Contract Data" or "Data Present," or require the user to enable a specific "Blind Signing" toggle within the wallet's application settings. Before proceeding with any of these interactions, users must understand that they are entering the highest-risk category of crypto transactions. It is essential to only enable this feature for specific, verified, and audited platforms.
When operating with blind signing enabled, users should use a burner wallet with minimal balances, keeping the vast majority of their holdings in a segregated vault wallet that never interacts with DApps. Strict verification of URLs character-by-character and a firm policy of never signing unsolicited requests are critical, non-negotiable safeguards.
| dApp Type | Blind Signing Prompt Example | Common Scenarios |
| NFT Mint | “Data Present” + hash | Minting a new collection or interacting with a custom minting contract. |
| DeFi Staking | “Contract Data” + hash | Depositing assets into a liquidity pool or locking tokens for rewards. |
| DEX Swap | “Data Present” | Trading one token for another via an automated market maker (AMM). |
| WalletConnect | “Contract Interaction” + hash | Using a mobile wallet to bridge an action to a desktop browser or external app. |
Quick Protection Guide
If your wallet shows “Data Present” or a hash, treat it like signing a blank check.
- Only blind sign with verified, audited platforms you intentionally navigated to.
- Use a burner wallet with small balances for dApps.
- Keep 90–95% of holdings in a vault wallet that never blind-signs.
- Verify URLs character by character.
- If anything feels rushed or “too good,” do not sign.
How Blind Signing Actually Works (Step-by-Step)
 Step-by-Step Lookout Of How Blind Signing Actually Works. Image via Shutterstock
Step-by-Step Lookout Of How Blind Signing Actually Works. Image via ShutterstockThe mechanics of blind signing are crucial to understanding the technical vulnerability it creates. It is a precise, multi-step process that moves from the user’s front-end application to the blockchain.
The Technical Process Broken Down
The full cycle of a blind-signed transaction involves six distinct steps, which collectively illustrate the information gap:
- DApp Constructs Call: The decentralized application (DApp) constructs a complex transaction that calls a specific function within a smart contract (e.g., granting an approval or initiating a swap). This data is compiled in accordance with the contract's ABI.
- Data Encoding and Hashing: The compiled and encoded contract data is then processed to create a unique, fixed-length cryptographic hash (e.g., a SHA-256 output). This hash is the compact identifier for the entire set of complex instructions.
- Hash Sent to Wallet: The transaction request, including only the hash and minimal context, is routed to the user's connected wallet, often via WalletConnect.
- Wallet Cannot Parse: The hardware wallet's Secure Element chip receives the hash. Without the corresponding, fully structured ABI and parser logic for this specific contract, the device's secure display cannot decode the hash into clear, human-readable details.
- User Signs Blindly: The hardware wallet displays the generic hash or the "Data Present" prompt. The user is prompted to physically sign the hash alone, relying entirely on the untrusted computer screen for context.
- Transaction Broadcast: The cryptographic signature (often ECDSA on secp256k1 for EVM chains) is generated using the private key secured within the wallet and returned to the dApp. The dApp then broadcasts the completed, signed transaction for immediate and irreversible execution on the blockchain.
The Information Gap Problem
The primary security flaw in this process is the "information gap" that exists between the user's operating system (computer or phone screen) and the trusted display of the hardware wallet.
The wallet screen is driven by the Secure Element chip, making it resistant to screen spoofing and certain OS-level malware. However, this display still only shows what the chip can parse. If an attacker has compromised the user's computer, they can alter the contract data sent to the hardware wallet while simultaneously ensuring the DApp interface on the user's monitor displays a benign message, such as "Approve 10 USDC."
The malicious code sent to the wallet, however, may actually be an unlimited approval to an attacker’s drainer contract. Since the hardware wallet can only display the generic "Data Present" for the complex, manipulated contract, the user blind signs the malicious hash, and the scam lives exactly within that information gap. This is exacerbated by parsing limits when dealing with dynamic contract structures and non-standard encodings.
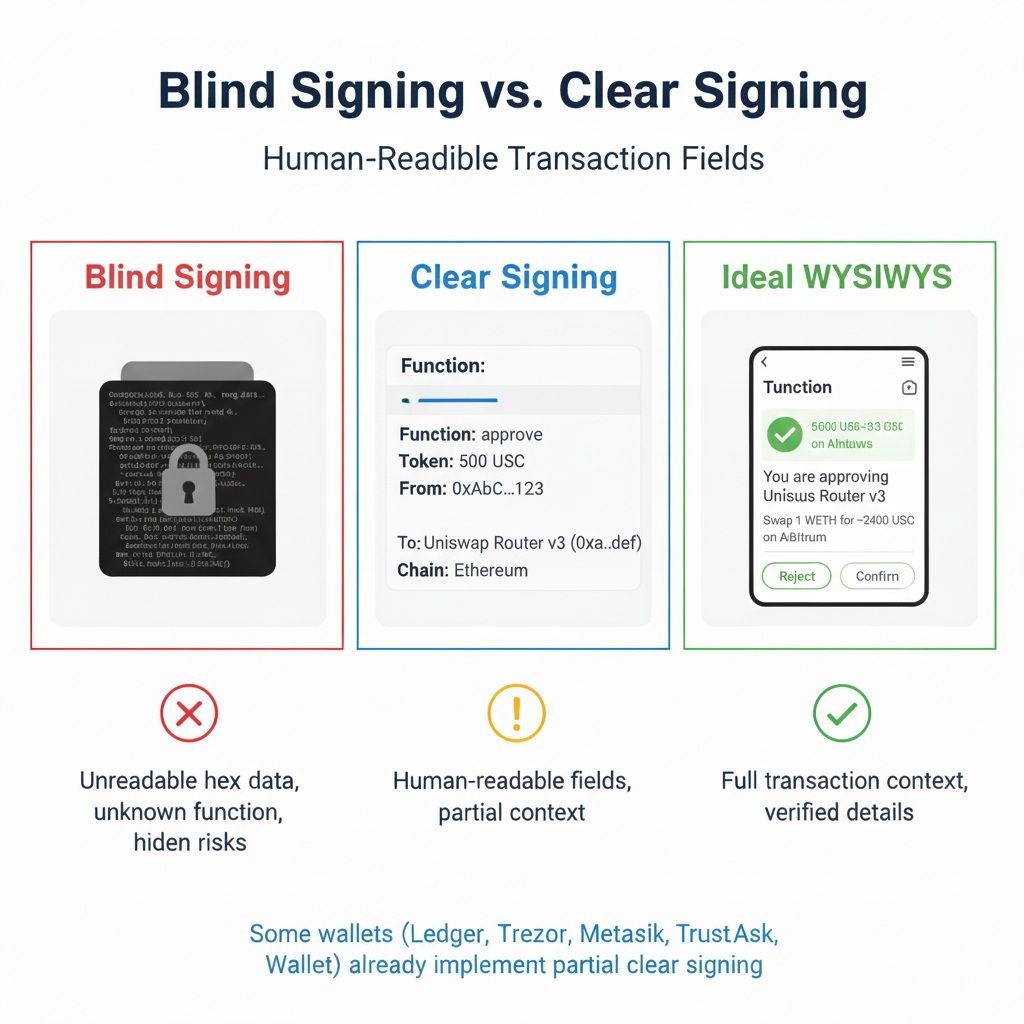
Blind Signing vs. Clear Signing
The industry's technical solution to the blind signing dilemma is the movement toward Clear Signing.
- Clear Signing is the mechanism by which a wallet can securely decode and display all critical, human-readable fields of a smart contract transaction on its own trusted screen. This means the wallet can show parameters like the token, amount, destination address, and the name of the function being called. For instance, the wallet might clearly display: "Approve 500 USDC for Uniswap Router v3 at 0x..." or "Swap 1 WETH for - 2400 USDC on Arbitrum."
- The guiding principle of Clear Signing is WYSIWYS (What You See Is What You Sign), ensuring the transaction details confirmed by the user on the secure screen are exactly what is cryptographically approved.
While major manufacturers like Ledger have pioneered Clear Signing initiatives, full WYSIWYS is not yet universally available across all chains and complex, new contract types. This ongoing lack of standardization across the ecosystem is why blind signing remains necessary in some cases.
 Blind Signing Is One of The Primary Points of Hacks
Blind Signing Is One of The Primary Points of HacksThe Security Risks of Blind Signing
Blind signing is the actual enabler for some of the most lucrative and devastating scams in decentralized finance, precisely because it removes the user’s final, human-readable security check.
How Scammers Exploit Blind Signing
Scammers systematically exploit the trust users place in the front-end interface, ensuring the website they interact with looks harmless and legitimate, while the underlying contract call is profoundly malicious. This is the central tenet of the exploit.
Scammers will often deploy deceptive contracts to execute one of the following attack types:
- Token Approval Drainers: The most prevalent attack. The scammer’s goal is to trick the user into blindly signing an unlimited token approval (often using the max uint256 value) for an ERC-20 token (like stablecoins or major altcoins) to a wallet drainer contract. This permission allows the scammer to systematically sweep those specific tokens from the victim’s wallet at any point in the future.
- Fake NFT Mints/Airdrops: A malicious website is deployed under the guise of an exclusive NFT mint or a surprise reward claim. The "mint" or "claim" button actually executes a complex contract function, such as setApprovalForAll, which grants the attacker permission to transfer all of the user's NFTs.
- "Security Verification" Phishing: Users are directed to phishing sites via urgent emails or DMs claiming their wallet is compromised and needs "verification." This verification process is, in reality, a malicious token transfer or approval request hidden behind a vague blind signing prompt.
The danger is absolute, in the sense that the DApp UI on the user's screen can be programmed to display any benign message to gain the user's trust, regardless of the true, destructive action the underlying contract will execute once the blind signature is provided.
Real-World Attack Vectors (Specific Scenarios)
Concrete examples are the most effective way to highlight the common red flags that accompany blind signing scams:
Scenario 1: The Phishing OpenSea Mint
- Vector: The victim receives an unexpected direct message (DM) on Discord or a social media platform announcing an "Exclusive, Limited-Time NFT Mint - 48 Hours Only!"
- Deception: The link provided points to a URL with a subtle typo, such as opensae.io instead of opensea.io. The website is visually identical to the legitimate NFT marketplace.
- Attack: When the user connects their burner wallet and clicks the "Mint" button, the contract call initiated is not a simple mint but an unlimited token approval targeting the user's most valuable ERC-20 tokens, pointing to a wallet drainer contract.
- Outcome: The user, seeing a generic "Data Present" on their hardware wallet, blindly signs. The attacker immediately uses the granted permission to sweep the user's entire token balance.
Scenario 2: The Urgent Security Update Email
- Vector: The victim receives a professional-looking email titled "Urgent Security Alert: Your Wallet May Be Compromised, Verify Now."
- Deception: The email links to a sophisticated phishing portal that mimics the official interface of a major wallet provider or exchange.
- Attack: The portal prompts the user to click a button labeled "Security Confirmation" or "Verify Address," which is actually a disguised asset transfer approval or an outright transfer request.
- Outcome: The user, operating under a sense of urgency and fear, blindly signs the request. All of their tokens are subsequently moved to a scammer’s address.
These scenarios share common red flags: a sense of urgency, unsolicited contact, slight variations in legitimate URLs, promises of "free" rewards, and the final prompt showing only the generic "Data Present" without clear transaction details.
 Common Red Flags Inlude Urgency Threats, Unexpected Contract, Among Others
Common Red Flags Inlude Urgency Threats, Unexpected Contract, Among OthersWhat Actually Happens When You Sign Maliciously
When a blind signature is maliciously used, the outcome is the same: the user loses control of their assets with no recourse.
The most common consequence is the unlimited approval of ERC-20 tokens. This uses the max uint256 value, granting the malicious contract the ability to spend a theoretically infinite amount of that token from the user’s wallet. Scammers then employ automated wallet drainer contracts to systematically sweep these approved tokens. For NFTs, the scam often revolves around the setApprovalForAll function, which delegates complete control over the user's collection to the attacker.
It is a harsh reality of decentralized ledgers that once a transaction is signed and executed, there is no undo, no chargeback, and no customer support recovery for the victim.
Hardware Wallets, Software Wallets, and Blind Signing
The device used to secure the private key determines the nature of the risk, but even the best-in-class hardware cannot eliminate the blind signing problem.
Why Hardware Wallets Require Blind Signing
Hardware wallets are the cornerstone of self-custody due to their use of a Secure Element (SE) chip, which keeps the private key isolated from the vulnerable operating system of the computer. This key isolation is their primary and most critical security benefit. However, the constraints of the Secure Element contribute to the blind signing dilemma:
- Design Constraints: They were built historically for simple protocols, and their limited onboard memory and screen size restrict the ability to store and display the complex, ever-growing ABI data necessary for modern smart contracts.
- Limited Context: The fundamental trade-off is that while the private key remains safe and isolated, the context of the complex transaction is lost due to parsing difficulty. This forces the device to default to the secure but unreadable blind signing process.
Trusted Display vs. Computer/Phone Screens
A central component of a hardware wallet's security is the trusted display, the small screen that is physically driven by the Secure Element, making it immune to manipulation by malware on the host computer or phone. This feature successfully prevents screen spoofing attacks, where malware might attempt to show a fake transaction summary on the user's monitor.
However, this introduces the Trusted Display Limitation Debate, a point of contention among security experts and wallet manufacturers:
- The Criticism: Critics, notably from companies like Tangem, argue that while trusted displays prevent spoofing, they do not solve the blind signing problem. The display is limited to showing what the wallet can parse, and if the contract is too complex, it still shows "Data Present." Furthermore, critics suggest that the additional hardware components could potentially introduce new risks, such as supply chain attacks that compromise the display components themselves. The takeaway here is that "trusted" does not equate to "complete."
- The Advocacy: Advocates, including Ledger, strongly counter that Secure Element verification is an immense security leap compared to relying on a host computer screen. They point to active Clear Signing initiatives as the solution to the parsing problem, arguing that the prevention of screen spoofing alone is a vital defense against a major attack vector.
Verdict: Trusted displays are unequivocally significantly safer than host screens and are a non-negotiable security layer, but they do not fix blind signing alone. Comprehensive defense still requires the use of asset segregation and active permission management.
Software Wallets vs. Hardware Wallets
When evaluating security, it is essential to distinguish between the two primary wallet types:
- Software/Hot Wallets: These wallets are always online, residing on a device's OS. They are easier for malware to intercept, modify transaction details, and steal private keys. A blind signature performed on a hot wallet is fundamentally riskier because the key isolation is minimal.
- Hardware Wallets: These provide the best key isolation available. Although they still require blind signing for complex contracts, the security benefit comes from the private key never leaving the Secure Element. This means that even if a user blindly signs a malicious contract, the key itself is safe from immediate OS compromise.
In practice, a user might use a hardware wallet in conjunction with a software wallet interface. While this setup helps, it still does not eliminate the risk inherent in signing unreadable data, meaning prudent security practices remain paramount.
Here are our top picks for the best crypto hot wallets for 2026. And while you're at it, also learn the key differences between software wallets and hardware wallets.
Legitimate Uses of Blind Signing
 When is Blind Signing Acceptable. Image via Shutterstock
When is Blind Signing Acceptable. Image via ShutterstockWhile blind signing carries its risk, it is, in certain scenarios, a necessary functional element of the crypto ecosystem.
When Blind Signing Is Necessary and Acceptable
The important principle here is that trust is placed in the protocol, not the transaction's appearance. Blind signing is acceptable, and sometimes necessary, under strict conditions:
- Established, Audited Protocols: Using foundational DeFi protocols (e.g., Uniswap, Aave, Lido) where the contract code is well-known, widely used, and has undergone multiple independent security audits.
- Verified Platforms: Interacting with NFT marketplaces that have been independently vetted and whose contract addresses are confirmed through multiple official sources.
- Minimal Exposure: Even in these acceptable scenarios, the transaction should only be performed with a burner wallet containing minimal, necessary amounts.
Lightning Network and Automated Signing
An example of a legitimate, systemic need for a form of automated or blind signature is found in the Lightning Network for Bitcoin. To achieve instant, low-cost off-chain transactions, Lightning relies on fast, automated updates to payment channels. Manually reviewing and approving every channel update would make the user experience impractical and break the network's function. Here, trust is placed in the audited, fundamental design of the protocol itself, not in a random, high-risk smart contract interaction.
How to Enable and Configure Blind Signing Safely
The decision to enable blind signing should never be taken lightly. It must be a tactical, temporary choice made only under specific circumstances.
When to Enable Blind Signing
The primary rule is: never enable blind signing just because a website tells you to.
- Only for Specific, Verified DApps: Enable the feature only when you are certain you are interacting with a necessary and trusted decentralized application for a specific function. Use-case examples include participation in major, well-known DeFi pools or accessing vetted NFT platforms.
- Avoid Unsolicited Requests: Never enable this function for unsolicited links, DMs, surprise airdrops, or any unverified, high-yield opportunity. These are almost universally a front for a scam.
Step-by-Step Enabling Process
While the process varies by wallet manufacturer and cryptocurrency application, the steps generally involve navigating to advanced settings:
Ledger Setup
Connect your Ledger device, unlock it, and open the specific coin app like Ethereum via Ledger Live or the device. Navigate to Settings on the device screen, select Blind Signing (previously "Contract Data"), and press both buttons to toggle it on. A warning appears confirming risks. Test with a small transaction on a reputable platform like MetaMask, ensuring the Ethereum app stays open, and Ledger Live is closed if issues arise.
Trezor Configuration
Trezor does not require a dedicated "blind signing" toggle like Ledger; it processes non-standard contract data through Trezor Suite's advanced wallet features. Connect your Trezor, select the account in Suite, and proceed with transactions, enabling any prompted data allowances during signing for smart contracts. Verify details on the Suite's interface before approval, as Trezor emphasizes message signing without app-specific blind toggles.
Software Wallets
In MetaMask or Rabby, connect your hardware wallet first, then handle blind signing prompts via the device's settings; no direct toggle exists in the wallet software. For Keplr (Cosmos chains), approve on Ledger when prompted, but avoid blind signing native transfers by using alternative paths if possible. Deep settings may list trusted DApps or networks; review transaction simulations in Rabby for better visibility before device approval.
Crucial Warning:
Always check URLs, use reputable DApps, and reject unsolicited messages requesting signatures. Disable blind signing post-transaction, never share your seed phrase, and limit warm wallet exposure to small amounts for DeFi. Ledger promotes "clear signing" in its ecosystem to reduce reliance on blind methods.
Critical Safety Rules When Enabling
When the feature is enabled, a few critical safety rules must be followed to minimize the window of vulnerability:
- Enable Only Right Before Use: Turn the feature on only in the immediate moments preceding the necessary transaction.
- Disable Immediately Afterwards: Turn off blind signing the moment the transaction is confirmed. This severely limits the time window an attacker has to push a malicious, pre-signed transaction to your device.
- Confirm Official Links: Use tools to confirm the URL, SSL certificate, and official social media links (e.g., from a project’s verified X account or CoinGecko page) before connecting the wallet.
- Never Enable for Unknowns: A prompt to enable the feature for a "debug," "test," or unknown contract should be a major red flag; never proceed.
Protection Strategies Against Blind Signing Scams
The best defense is a layered approach that combines hardware isolation with smart operational security (OPSEC)
.Asset Segregation and Burner Wallets
Asset segregation is the single most important action an individual can take to mitigate the risk of blind signing exploits. This involves clearly defining and maintaining two separate wallets:
- Vault Wallet: The main storage wallet where 90–95% of a user's holdings are kept. This wallet should never be connected to a dApp, should never have blind signing enabled, and should only be used for simple, clear transactions (sending funds to the burner wallet or a verified exchange).
- Interaction/Burner Wallet: A dedicated, lower-balance wallet used specifically for dApp interaction, NFT mints, and DeFi activities. This is the only wallet that should ever have blind signing enabled or be used to grant token approvals.
The security value here is that since approvals are per-wallet, an unlimited approval granted by a compromised burner wallet cannot affect the assets secured in the vault wallet. This containment strategy minimizes the potential financial damage from a blind signing exploit.
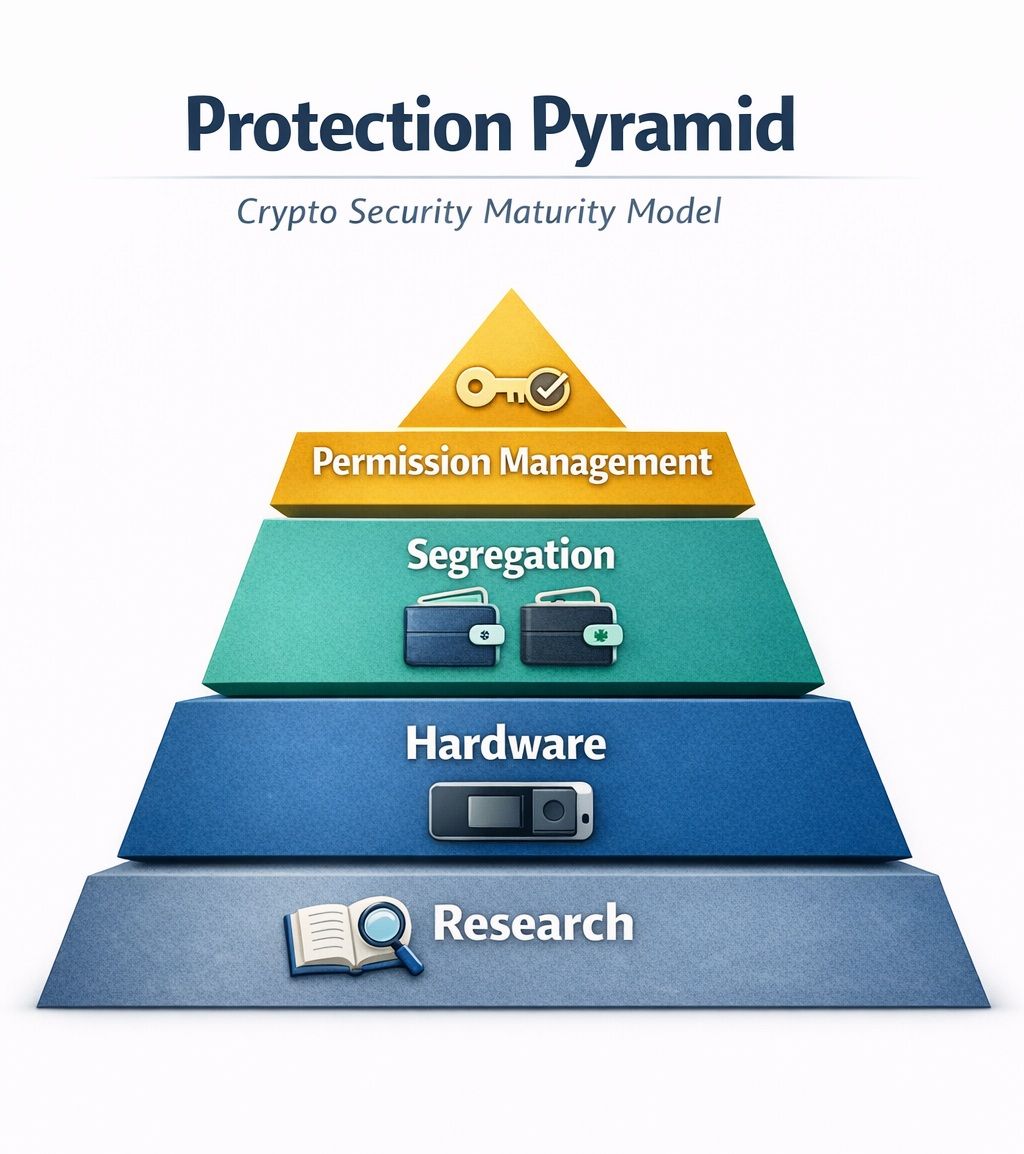 The Protection Pyramid Shows How Crypto Security Compounds
The Protection Pyramid Shows How Crypto Security CompoundsPre-Transaction Due Diligence
Before engaging in any complex transaction, particularly those requiring a blind signature, extensive due diligence is required:
- Check Audits and Auditors: Look for independent security audits of the smart contract and verify the reputation of the auditing firm.
- Confirm Contract Addresses: Use official sources to verify that the contract address you are interacting with is the correct one for the protocol you are using.
- Search for Warnings: Actively search community forums, X, and other platforms for any recent scam or warning posts related to the dApp or its contracts.
- Rule of Thumb: If any part of the verification process is incomplete, confusing, or feels rushed, the user must adhere to the fundamental rule: if you can’t verify it, don't sign it.
Hardware Wallet and Clear Signing Choices
Users should be proactive in choosing hardware wallets that are actively committed to and implementing Clear Signing for the chains they use most. Mentioning entities like the Ledger Clear Signing initiative and the industry's ultimate WYSIWYS goal helps define what users should look for. It is also important for users to understand their specific device’s limitations, knowing which chains or transaction types their hardware wallet can reliably clear-sign helps them manage risk accordingly.
Active Permission Management
A signed approval, especially an unlimited one, grants a contract a perpetual ability to spend your tokens. This permission persists indefinitely unless the user explicitly revokes it.
- Tools: Users should regularly utilize token approval checker tools, such as the Etherscan Token Approval Checker or Revoke.cash, which allow them to see a list of all active allowances on their address.
- Regular Review: It is vital to regularly review and revoke allowances, particularly for stablecoins and major token holdings, which are the primary targets of drainers.
- Recommended Cadence: Heavy DeFi users should perform this review monthly, while lighter users should adopt a quarterly routine.
- Recovery: Should a user suspect they have signed something malicious, the immediate steps are to revoke all approvals for the token/contract involved, and then quickly move all remaining funds from the compromised wallet to a new, clean wallet address.
The Future of Blind Signing (and Clear Signing)
While the risks are current, the industry is moving toward a more secure, human-centric transaction standard.
Industry Efforts to Eliminate Blind Signing
The collective goal of the decentralized ecosystem is to make blind signing obsolete through standardization and better technology:
- Ledger’s Clear Signing Initiative: This is a key driver in the push to develop and implement the decoding logic necessary to parse complex smart contract data into a human-readable format.
- Wallet + DApp Collaborations: Industry leaders are working to establish universal, standardized protocols for DApp-to-wallet communication, ensuring the necessary transaction context is passed securely and reliably.
- WYSIWYS as the Guiding Principle: The concept of What You See Is What You Sign is the primary philosophical and technical objective, but the problem of ecosystem fragmentation, the proliferation of different chains, ABIs, and standards, remains the chief obstacle.
Technological Advances on the Horizon
Technological progress will gradually close the information gap exploited by blind signing:
- Better Decoding: Advances in contract parsing and human-readable decoding tools will allow wallet software to interpret more dynamic contract calls.
- Richer Hardware Screens: Future hardware wallets will likely feature larger, higher-resolution screens capable of displaying more comprehensive transaction details without compromising the security of the Secure Element.
- Standard Formats: Widespread adoption of standardized formats for DApp-to-wallet communication will reduce ambiguity and parsing difficulties.
- Potential AI-Assisted Explanation: Future advancements may even include AI-assisted features that explain the potential consequences of a complex smart contract function in simplified, natural language before the user signs.
What Users Can Expect Next
While some wallets already offer partial clear signing for simple interactions, users must maintain a high level of OPSEC regardless of technological improvements. The evolution of security will continue, but the main responsibility remains with the user. The ultimate goal is to achieve an environment where regular users can safely participate in DeFi without needing an advanced understanding of Solidity or blockchain mechanics.
Best Practices Checklist for Blind Signing Safety
For anyone operating seriously in crypto, these practices should sit at the center of their personal security discipline, especially when interacting with complex smart contracts or signing transactions.
Start with strict pre-connection checks. Verify URLs carefully, assess platform reputation, and cross-check announcements through official social channels before connecting a wallet. If anything feels off, walk away immediately. Unexpected outreach, artificial urgency, unrealistic incentives, or unclear transaction prompts are all reasons to disconnect without hesitation.
Structure your wallets defensively. Use a clear separation between vault wallets and burner wallets so any potential exposure is capped to a small, controlled balance rather than your entire holdings.
On the tooling side, hardware wallets remain non-negotiable. Prioritize devices that already support clear signing or have publicly committed to rolling it out, as visibility into what you are approving materially reduces blind-signing risk. Pair this with a regular permission review routine. At least once every month or quarter, use tools such as Revoke.cash to audit and remove unnecessary smart contract approvals from your interaction wallets.
Finally, know your recovery playbook before you need it. If you suspect a malicious signature, act immediately. Revoke all approvals, assume the wallet is compromised, and move any remaining funds to a fresh, clean address. In crypto security, speed and discipline often matter more than technical sophistication.
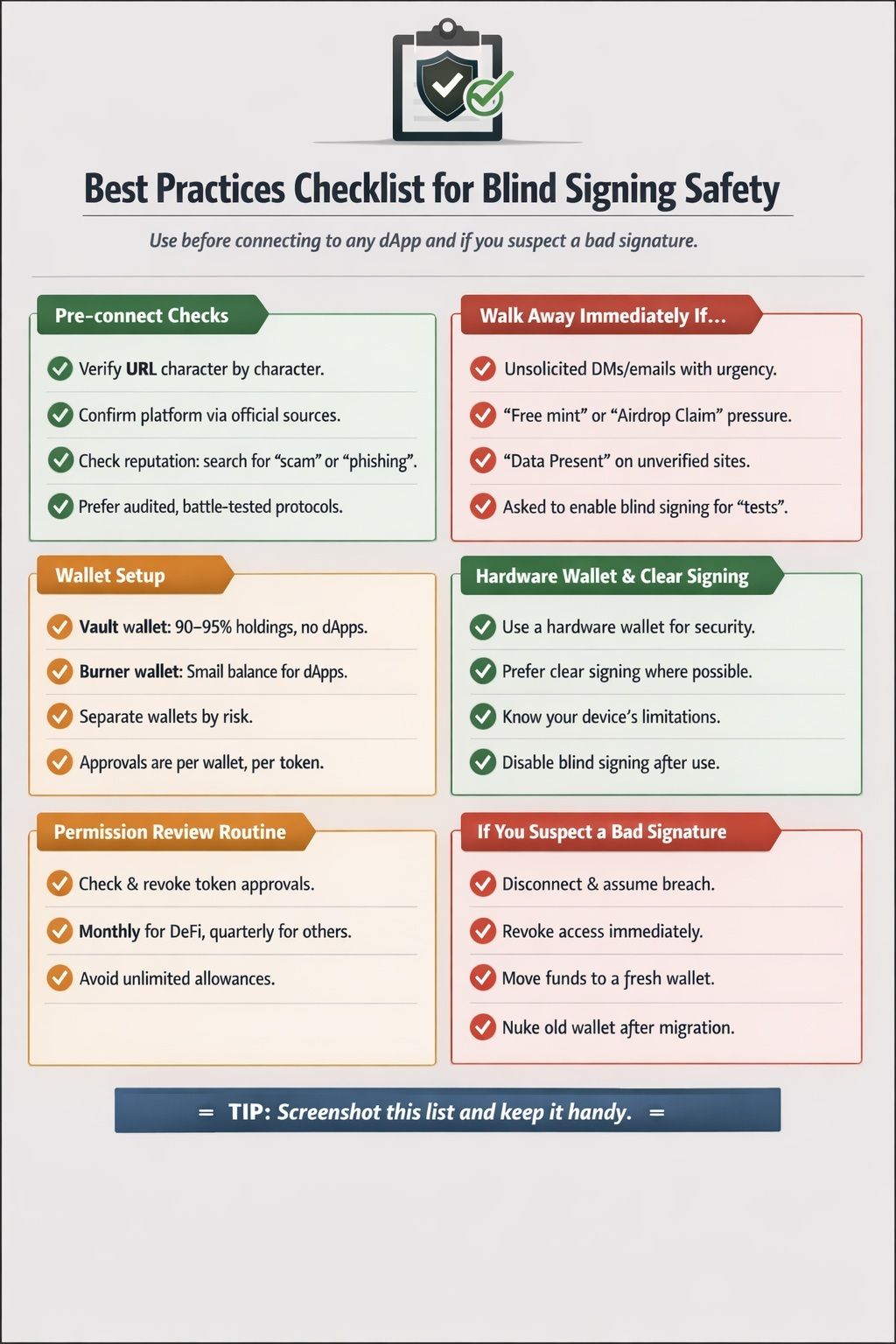 Best Practices Checklist for Blind Signing Safety
Best Practices Checklist for Blind Signing Safety




